Arid Viper Deploys Spyware in Egypt and Palestine via Trojanized Android Apps
- Security researchers found five campaigns targeting Android users with trojanized apps.
- These campaigns were active in Egypt and Palestine, where they deployed malicious code.
- The threat actor, whose main aim is espionage, was identified as the Arid Viper APT group.
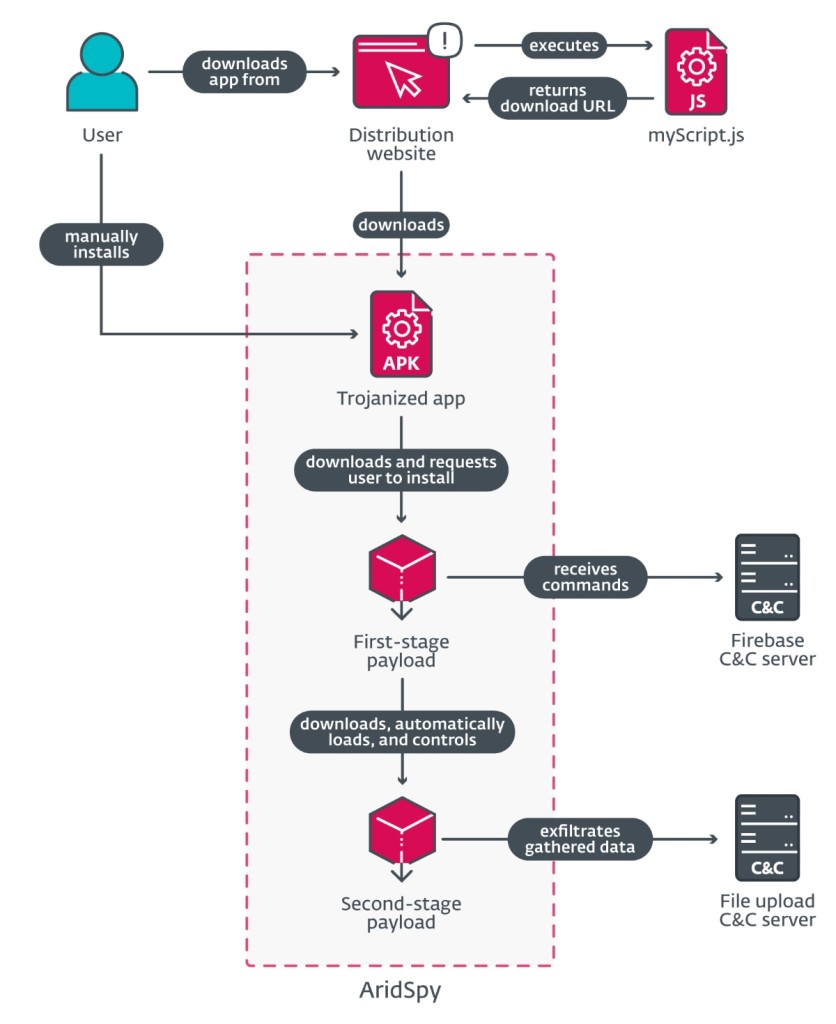
ESET researchers discovered five espionage campaigns distributing trojanized apps to Android users in Egypt and Palestine via dedicated websites. The threat actor behind these appears to be Arid Viper. Victims could download and manually install a functional Android application trojanized with malicious code named AridSpy in the security report.
The Android spyware impersonates messaging apps like NortirChat, LapizaChat, ReblyChat, a job opportunity app, and a Palestinian Civil Registry app. Three of the five discovered campaigns were still active when the report was issued.
AridSpy is multistage malware that downloads first- and second-stage payloads from its command-and-control (C&C) server to help it avoid detection. Several of these distribution sites use the malicious myScript.js, a unique JavaScript file previously linked to Arid Viper by 360 Beacon Labs and FOFA. Thus, this attack targeting organizations in Palestine and Egypt appears to be carried out by the Arid Viper APT group.
Most of the observed spyware instances registered in Palestine were for the malicious Palestinian Civil Registry app, with one other unrelated detection. In Egypt, the same first-stage payload had a different package name, and another used the same C&C servers as the LapizaChat and job opportunity campaigns.
The malicious app that pretended to pertain to the Palestinian Civil Registry claiming to offer name, place of residence, date of birth, ID number, and other information on the residents of Palestine, was promoted via a dedicated Facebook page.
The security researchers said a similar piece of JavaScript was found on the sites distributing NortirChat, LapizaChat, and ReblyChat. This connection was independently confirmed by the FOFA search engine research team, who attributed this malware to Arid Viper after finding seven of the same Android AridSpy distribution websites that contained myScript.js.
This same JavaScript code was also used in the campaign that targeted the FIFA World Cup in Qatar with an earlier version of AridSpy but with a different final payload, noticed by 360 Beacon Labs.