APTs Targeting American Organizations via Pulse Secure VPN Zero-Day
- At least two groups of actors, one apparently Chinese, were exploiting a zero-day in Pulse Secure VPN.
- The exploit enabled the actors to bypass single and multi-factor authentication on Pulse Connect Secure.
- The zero-day was combined with previously fixed flaws that are still to be found out there.
Hackers of at least two APT groups were actively exploiting a zero-day flaw in Pulse Secure VPN, chaining it with previously discovered vulnerabilities to compromise high-profile American entities such as networks of the U.S. Defense Industrial Base (DIB). The zero-day vulnerability is tracked as CVE-2021-22893, and it was discovered by researchers of FireEye this month. The other flaws used in conjunction with it are CVE-2019-11510, CVE-2020-8243, and CVE-2020-8260, all fixed a while ago but are evidently still present on many systems out there.
Pulse Secure has released an “out-of-cycle” advisory for the zero-day, giving it a CVSSv3.1 score of 10 (critical). According to the details given, the vulnerability is an authentication bypass that allows unauthenticated users to perform remote arbitrary file execution on the Pulse Connect Secure gateway.
The solution to the flaw is to upgrade the Pulse Connect Secure server software to 9.1R 11.4 (other versions to follow soon). There’s also a mitigation that involves importing a Workaround-2104.xml file which disables the ‘Windows File Share Browser’ and the ‘Pulse Secure Collaboration’ features on the PCS appliance.
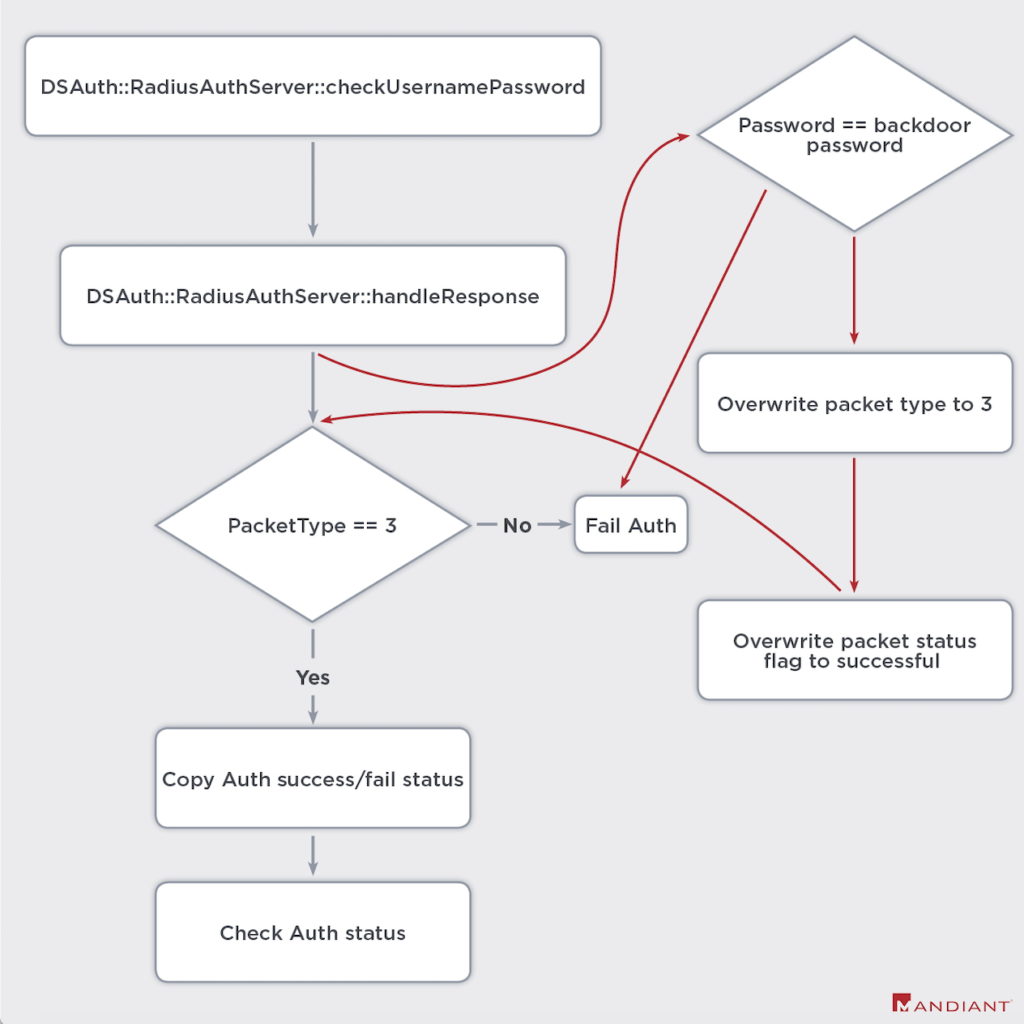
The exploitation of the above enabled the actors to bypass single and multi-factor authentication on Pulse Secure VPN devices, persisting across upgrades and maintaining access through web shells. The attacks followed certain steps as identified by Mandiant (FireEye) experts on multiple occasions they were called to investigate, as laid out below.
- Trojanize shared objects with malicious code to log credentials and bypass authentication flows, including multifactor authentication requirements. We track these trojanized assemblies as SLOWPULSE and its variants.
- Inject webshells we currently track as RADIALPULSE and PULSECHECK into legitimate Internet-accessible Pulse Secure VPN appliance administrative web pages for the devices.
- Toggle the filesystem between Read-Only and Read-Write modes to allow for file modification on a typically Read-Only filesystem.
- Maintain persistence across VPN appliance general upgrades that are performed by the administrator.
- Unpatch modified files and delete utilities and scripts after use to evade detection.
- Clear, relevant log files utilizing a utility tracked as THINBLOOD based on an actor-defined regular expression.
The FireEye investigation concludes that the APTs exploiting the zero-day in Pulse Secure VPN are UNC2630 and UNC2717. The former was more focused on American targets, and FireEye found several connections with the APT5, a group of Chinese hackers who are engaging in espionage operations since at least 2014.
Heather Paunet, Senior Vice President at Untangle tells us: