North Korean ‘APT45’ Targets NASA and Other US Critical Infrastructure and Military Bases
- North Korea-backed APT45 cyberespionage and ransomware group targeted U.S. government facilities and agencies.
- The hackers stole information from the American Air Force and NASA, among others.
- Several other institutions from the nuclear, defense, and aerospace sectors were among the victims.
North Korean cybercriminal group tracked as APT45 has been actively targeting critical infrastructure and military operations located in the U.S., trying to steal nuclear and military secrets from government facilities and agencies, a new report from Panda Security reads.
A joint advisory released by the U.S., U.K., and South Korea on Thursday confirmed that North Korean hackers infiltrated the systems of several entities in the nuclear, defense, and aerospace sectors.
The cybercriminals managed to steal valuable information from important private US defense contractors, two U.S. Air Force bases, and NASA’s Office of Inspector General.
The APT45 group deployed espionage campaigns as early as 2009, mostly targeting critical infrastructure, and attacks aimed at American entities have been ongoing for years.
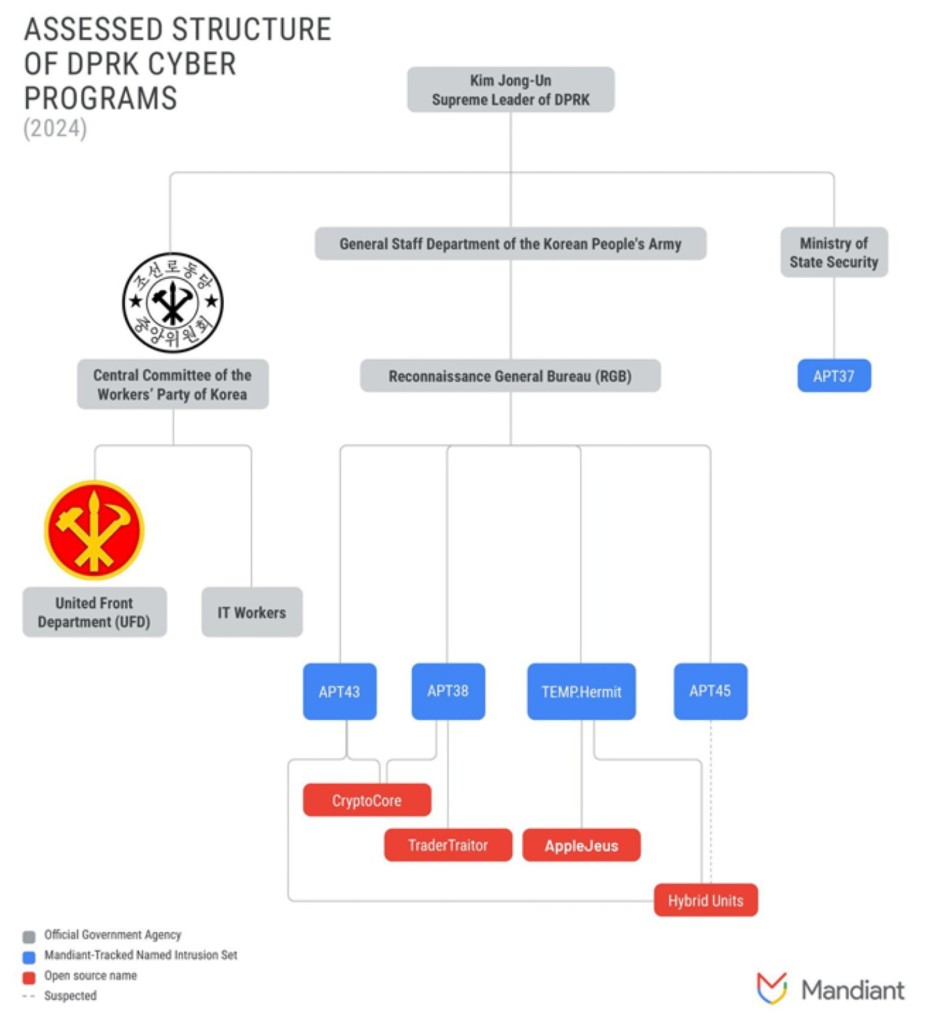
Google-owned Mandiant is tracking the activity cluster under a new moniker, APT45, which overlaps with names such as Andariel, Onyx Sleet (formerly Plutonium), Silent Chollima, Nickel Hyatt, and Stonefly.
The hacker group is believed to be controlled and supported by North Korea’s military intelligence agency, the Reconnaissance General Bureau (RGB), and the U.S. and the U.K. are among the countries targeted by Pyongyang’s global cyber espionage campaign.
Multiple government agencies indicted and announced a $10 million reward for North Korean hacker Rim Jong Hyok, who is believed to have been involved in the cyberattacks targeting the U.S. and its allies.
The individual was charged with using ransomware to target 17 U.S. entities across 11 states, including NASA, military bases, healthcare facilities, and defense and energy companies in China, Taiwan, and South Korea.
APT45, APT38, APT43, and Lazarus Group are all believed to be part of North Korea's RGB.