APT39 Iranian Cyber Espionage Group On FireEye’s Spotlight
- FireEye identifies APT39 as an Iranian cyber-espionage group and releases details about their operation.
- APT39 uses the same set of tools as APT34 does, but develops and incorporates different modifications to them.
- The group targets mainly communication infrastructure, IT, and travel companies.
FireEye has released a blog post that presents more details about APT39, an Iranian cyber-espionage group that is responsible for extensive personal information collection. FireEye has been tracking the particular group for over five years now, so providing an insightful overview of how they orchestrate their attacks and publishing details on their operation is something that only they can do. According to the collected data, most of the activities of APT39 are concentrated in the Middle East countries, although countries from Europe, the USA, South Korea, and Australia are also targeted selectively.
The organizations that are targeted by APT39 are mainly engaged in the telecommunications and IT sector, while travel-related industries are also monitored. The only logical explanation for this is to track specific individuals, while the data collection from telecommunication companies is likely done to facilitate operational planning for existing and future campaigns. This assumption is supported by the fact that APT39 also targets government entities, having collected crucial information on several occasions. As FireEye suggests, this espionage group is using a similar set of tools and methods to APT34, another Iranian espionage group that is also known as “OilRig”. However, the two are using different variants of the same malware tools, so they are possibly collaborating or share resources.
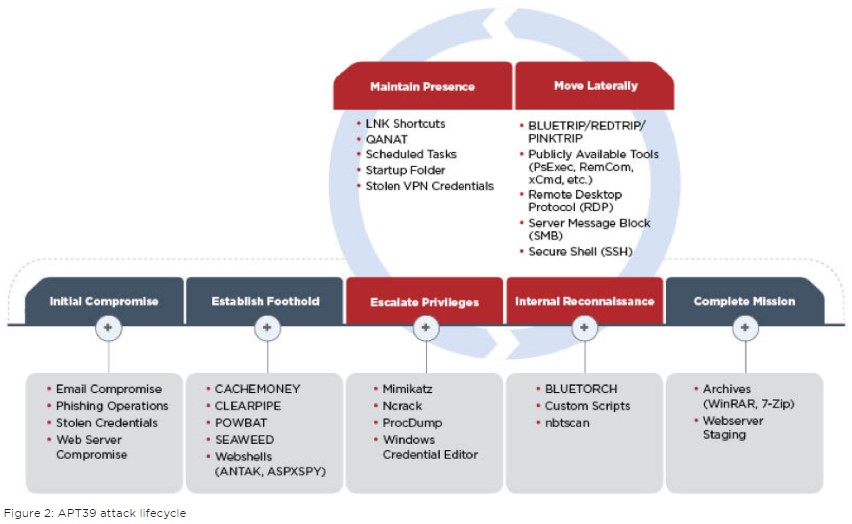
According to FireEye’s observations, APT39 is leveraging phishing emails with POWBAT malware attachments to achieve the initial compromise. Other ways include the stealing of login credentials by redirecting victims to masqueraded domains and the targeting of vulnerable web servers and the installation of web shells. From there, APT39 utilizes custom backdoors like SEAWEED, POWBAT, and CACHEMONEY to establish their presence in the target systems, and then proceed with the required privilege escalation by using Mimikatz, Ncrack, ProcDump, and other free tools. Next, the group indulges in lateral movement by using a rich set of tools as shown in the following diagram:
image credits: fireeye.com
The fact that APT39 uses modified and highly tailored versions of the tools mentioned above make them harder to detect by anti-virus tools and network defense systems. Right now, APT39 is considered a severe threat for organizations that support critical infrastructure in the targeted countries, as well as their clientele. Considering the scale of the data theft that is achieved by APT39, the associated cost to support the operation of these groups is considered minuscule. For now, the only thing that can be done is to monitor their activity, analyze their operations, identify trends, and devise stronger protection strategies.
Where do you stand on the above? Let us know in the comments below, and feel free to share this story by visiting our socials on Facebook and Twitter.