APT29 Has Not Retired, But Instead, Was Flying Under The Radar
- APT29 never left the hacking scene, but instead focused more on high-profile targets.
- Researchers found three new malware samples that they can attribute to the group with certainty.
- The group is using Twitter, Imgur, and Fotolog to host steganographic images that hide code inside them.
As reported by ESET researchers, the Russian espionage hacking group known as “APT29” (or Cozy Bear, or The Dukes) has been lurking in the darkest sides of the net, even though they managed to stay away from the media’s attention in the recent years. The group has been active since 2013 and peaked in 2016, but other than a suspected comeback on November 2018, there has been nothing leading to their trail. Some thought that APT29 might have retired, but the latest report by ESET shows that this was never the case.
Source: WeLiveSecurity
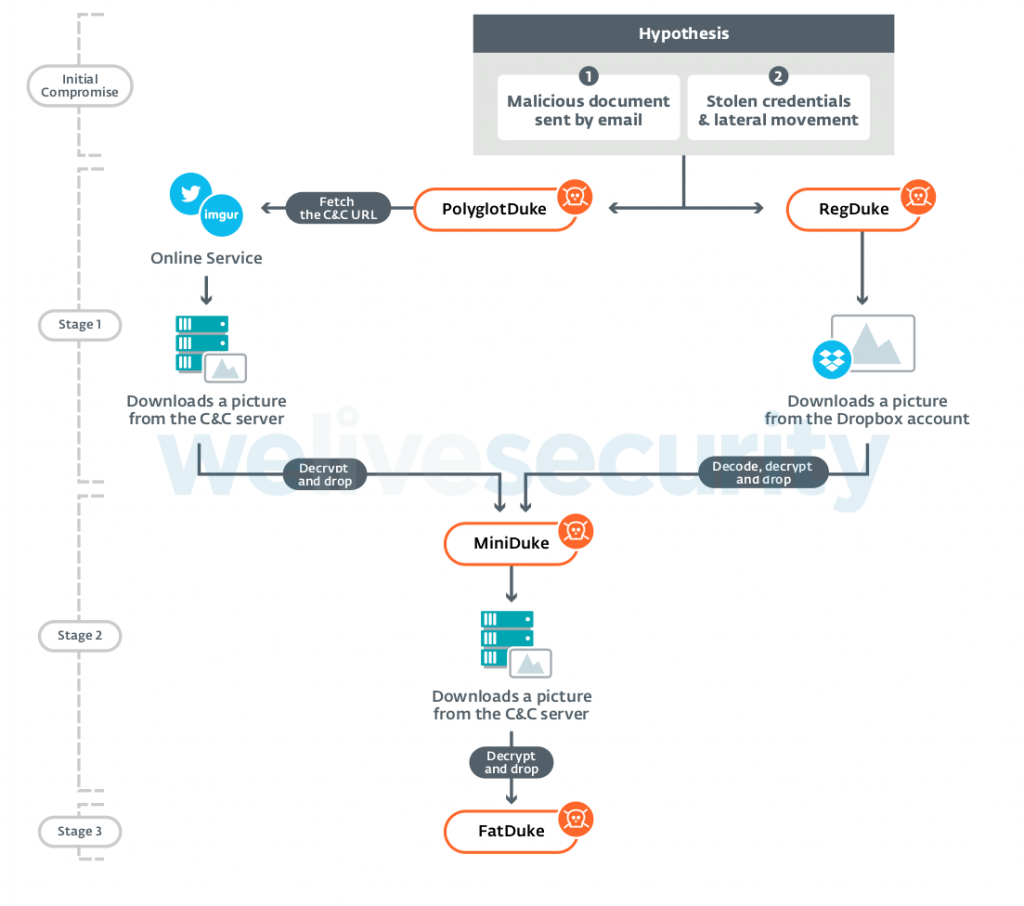
In the recent months, the team of researchers discovered three new malware families called “PolyglotDuke”, “RegDuke”, and “FatDuke”, all of which are attributed to APT29. The new malware tools were deployed within 2019, starting with FatDuke in June. Some of the elements that gave the group away are the use of Twitter to host C2 operations, the use of steganography to hide payloads in images, and the extensive use of WWI (Windows Management Instrumentation) for persistence. The targeting is also characteristic of APT29, with the targets including Ministries of Foreign Affairs and various organizations which were known to have been compromised before.
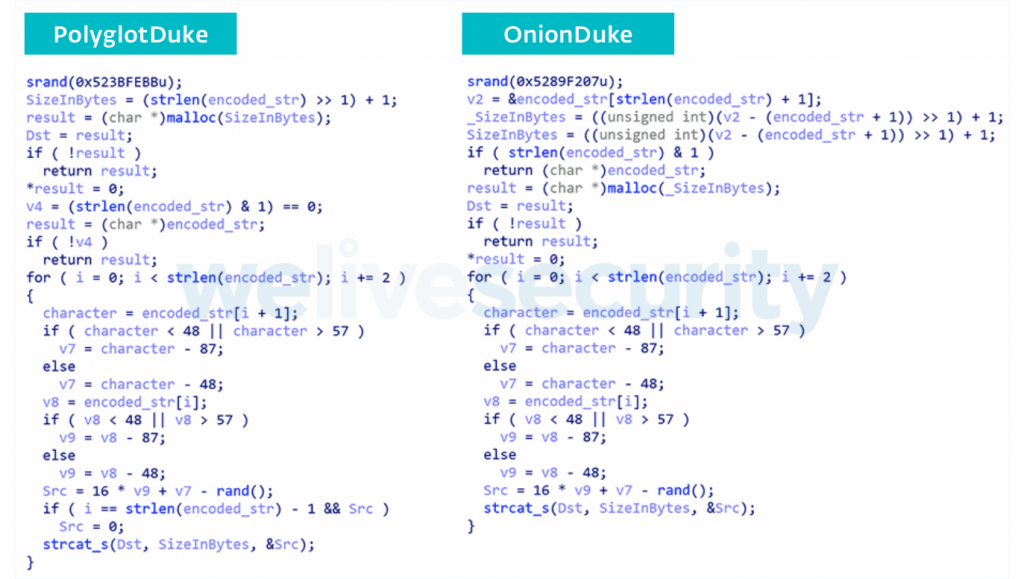
As for the malware tools themselves, the researchers noticed similarities in the custom encryption algorithm that is used by PolyglotDuke and OnionDuke (from 2013). Similarly, the most recent samples of MiniDuke feature the same backdoor that samples from five years ago deployed. All of this is indicative and not definitive, as another group might have gotten their hands onto the code of the old samples, and used it on newer iterations. However, this is unlikely to be the case considering how many pieces of the puzzle are in place.
Source: WeLiveSecurity
The ESET team has compiled a detailed list with the indicators of compromise, and you may check it out on GitHub. If you do, you’ll notice how many Twitter profiles are used for the hosting of steganographied images which contain the malware samples. Other channels of infection include Kiwibox, Reddit, Fotolog, Evernote, and Imgur. For more details on the findings of ESET and the tracking of the whole “Ghost Operation” as they call APT29 activity, check out the whitepaper that underpins the report.
Source: ESET Whitepaper
Were you among those who thought that APT29 went dormant, or did you think they are still out there doing their thing? Let us know where you stood in the comments down below, or on our socials, on Facebook and Twitter.