APT Group “RedCurl” Has Been Stealing Sensitive Data for Three Years
- “RedCurl” is a Russian group of actors who compromised at least 14 firms from six countries.
- The group wasn’t using custom malware tools or highly sophisticated methods but still succeeded.
- The main way in was through phishing emails that dropped self-propagating malware.
Group IB is giving details about yet another “hackers for hire” group that has the capacity to compromise large companies and organizations and steal sensitive documents. Named “RedCurl,” the group has been active for three years now, has carried out 26 individual attacks on entities based in six countries, and stole sensitive data from 14 companies.
Group IB has actually been tracking the actors since last summer when one of RedCurl’s victims called the intelligence firm to aid them with the investigation. The victimized entities include banks, law firms, consulting organizations, insurers, big retailers, and construction firms.
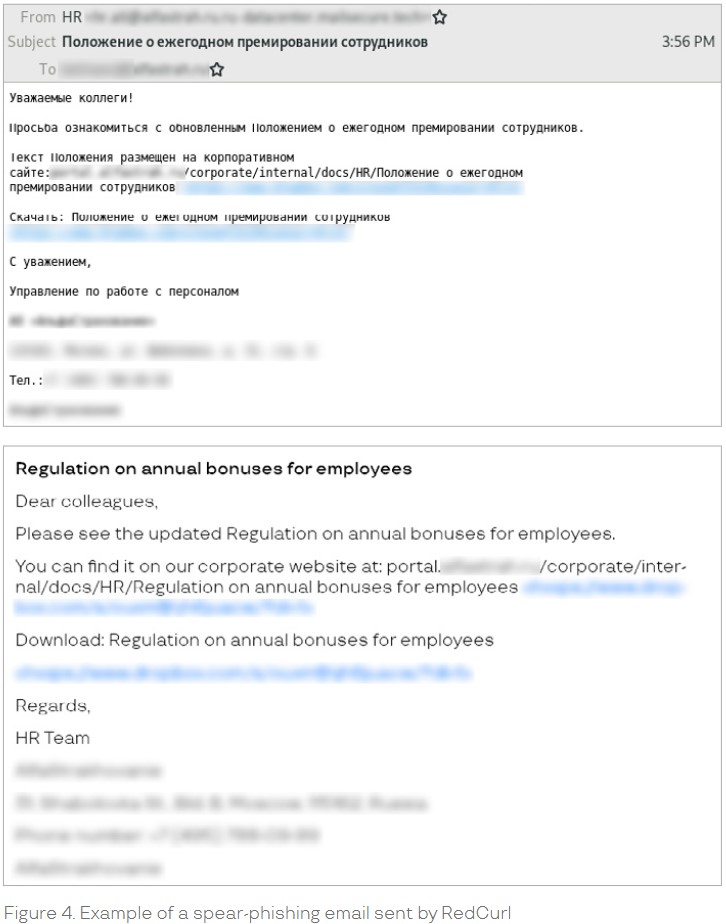
RedCurl is followed the typical approach of this kind of actors, relying mostly on phishing emails that dropped malware-laced files. No custom tools or complex hacking methods were followed, and there wasn’t the need for it anyway. They prepared the phishing emails with diligence, using official company letterheads, full details with correct addresses, etc. To reach out to a large number of people in an organization, the actors often pretended to be members of the HR department, so no suspicions were raised when these emails circulated.
Source: Group IB
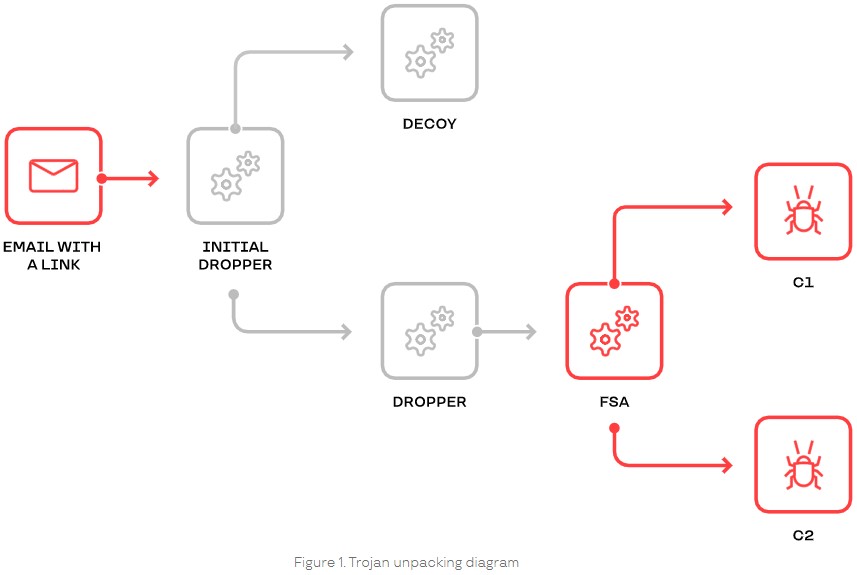
The attached files include SFX archives, LNK files, XLAM documents, and JS files. If opened, a sensitive data-exfiltration process initiated. The malware scanned the infected machine and generated a directory listing the details that were exfiltrated via WebDAV.
The malware attempts to propagate across the compromised network if possible (via LNK replacement). At the same time, a PyArmor-wrapped LaZagne attempts to steal email account credentials that may lie in web browser cookies. If that fails, victims are met with a Microsoft Outlook phishing form where they are tricked into entering their domain account credentials.
Source: Group IB
The actor also sets up access to the target machine via SSH, so all in all, the group is using off-the-shelf open-source tools and a pretty “standard” break-in methodology. This is precisely what helps the actors stay undetected, as security tools are usually not generating warnings for LaZagne, 7-Zip, ADExplorer, curl, NirCmd, etc. So, this isn’t an indication of a lack of skills, but more of a clever approach that enables RedCurl to maintain stealthiness.
Group IB believes that RedCurl is Russian-speaking actors, but they could find no evidence of overlaps with other similar hacking groups. The C2 server was set up using Russian profiles, the SFX archives were created with the WinRAR utility set to Russian, so it’s clear that RedCurl is a Russian group. However, this doesn’t stop them from attacking Russian firms too, which is another indication that they were acting on behalf of clients.