‘Aprilaire’ Exposed Millions of IoTs Online via Live Database
- The database that logged IoT data from the smart devices of Aprilaire has been exposed online.
- The firm hasn’t responded to the reporting researcher, so the duration of the exposure is unknown.
- The IoTs could have very easily been compromised by a coin-mining of DDoS swarming botnet.
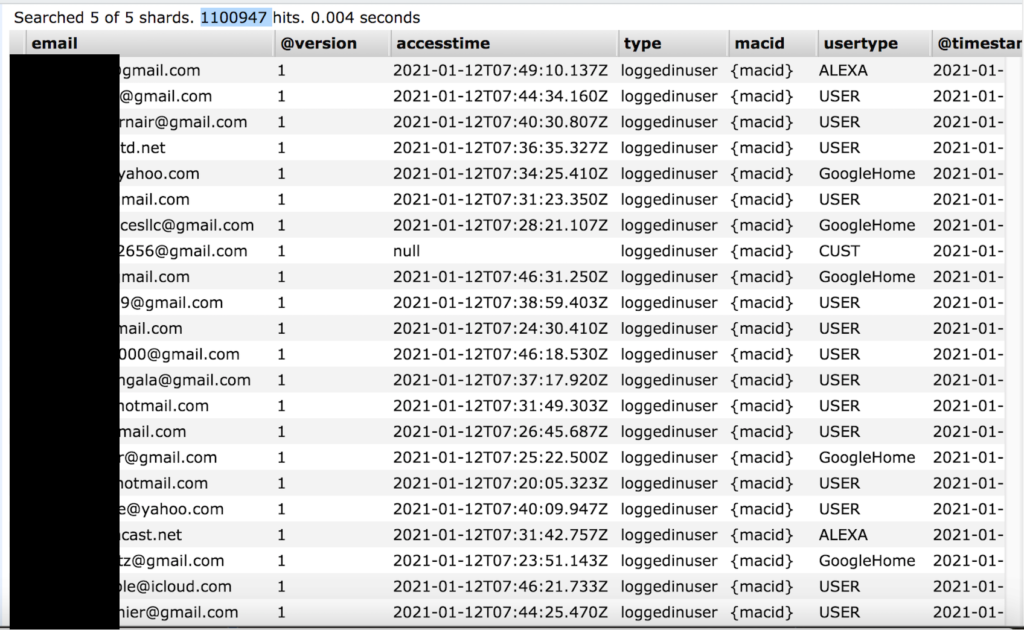
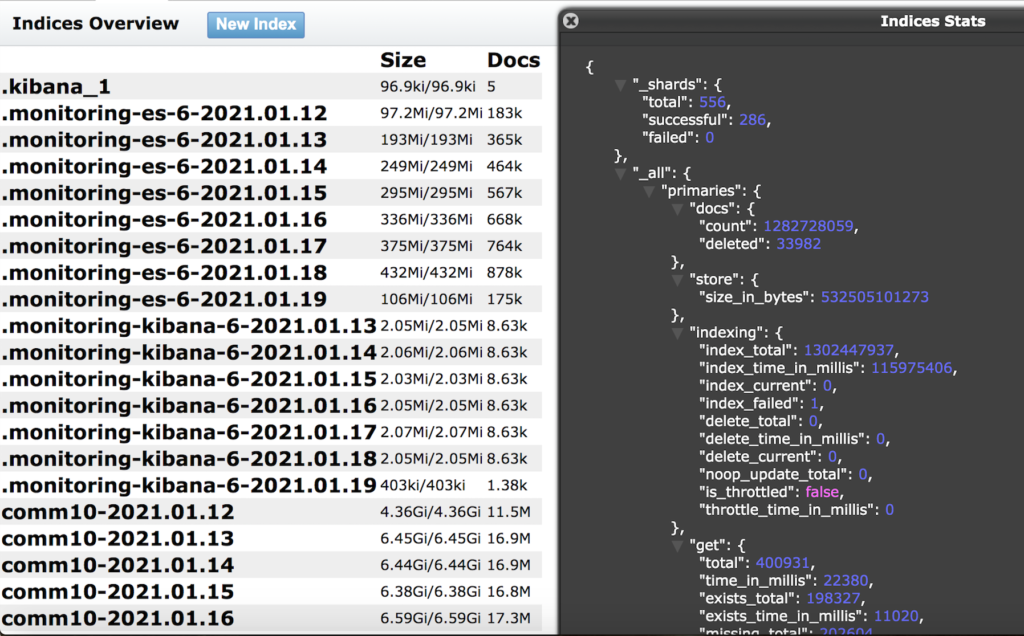
‘Aprilaire,’ the American maker of dehumidifiers, humidifiers, thermostats, air purifiers, and air filtering systems, has made a configuration mistake on one of its live databases, exposing details about IoT devices that were sending data back home. In total, 1.25 billion records have been leaked online, including a subset of 1.1 million “logged in users.”
The discovery and relevant report come from security researcher Jeremiah Fowler, who immediately informed Aprilaire via a phone call and helped them secure the database eventually. The duration of the exposure remains unknown.
According to what is shown in the evidence published by the researcher, the details that have been exposed include user email addresses, device status, access timestamps, user type (Google Home or Alexa), and IoT connection data.
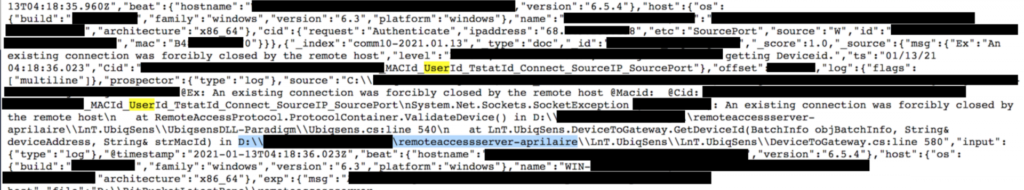
Having things like WiFi details, connection data, configuration settings information, IP address, MacIDs, device IDs, error logs, and device firmware versions exposed is like an invitation to hackers who specialize in botnet operations. In the case of Aprilaire, the number of the exposed smart devices is large enough to make such an endeavor worth the trouble.
While the researcher didn’t find any signs of compromise in the short time he had available to scrutinize the database, skillful actors may have infiltrated and accessed Aprilaire’s remote access server. The error logs may have exposed the network’s operations, what vulnerabilities can be exploited, how the service operates from the backend, and where the data is stored.
If you have an Aprilaire device and you’re worried about the botnet risk, you can monitor the device and see it overheats inexplicably. You can also use a packet analysis tool like WireShark to figure out if it’s connecting to anything other than Aprilaire’s servers.
Compromised IoTs are typically used in DDoS (distributed denial of service) swarms or crypto-coin mining operations. In either case, you should notice a resource-binding effect that cannot be attributed to normal operations. If the device is running on battery, you should see the battery levels being depleted very soon too.
Finally, since email addresses have been exposed too, users shouldn’t forget about the scenario of receiving phishing messages from crooks. Remember, the only thing these scammers know about you is that you’re using an Aprilaire device, so if they’re to impersonate a brand, this will be it.