Apple Vision Pro Vulnerability Patched After GAZEploit Attack Discovery
- Security researchers discovered a now-patched flaw that enabled an attacker to see what users typed on the device's virtual keyboard.
- Dubbed GAZEploit, the abuse leveraged the eye movements of a user's virtual avatar.
- The attack utilized a supervised learning model trained on recordings of the Persona view.
A critical vulnerability in Apple's Vision Pro mixed reality headset enabled attackers to extract data from the virtual keyboard through a sophisticated exploitation technique known as GAZEploit, as per a recent security report. The now-patched flaw posed a significant risk, as an attacker could obtain user passwords and other sensitive data.
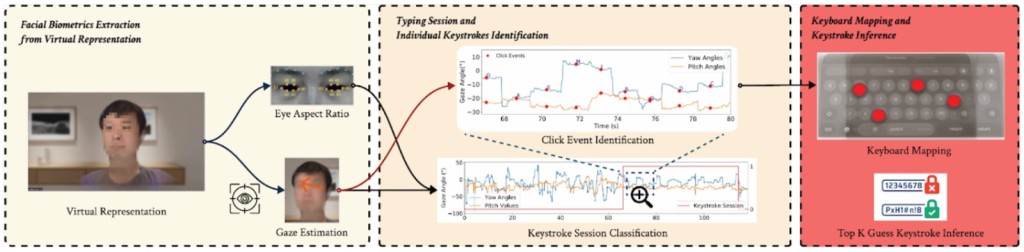
The research team, comprising experts from the University of Florida, CertiK Skyfall Team, and Texas Tech University, discovered that attackers could potentially infer keystrokes by observing virtual avatars shared via platforms like video calls and live streaming.
Tracked as CVE-2024-40865, the GAZEploit attack capitalized on vulnerabilities inherent in gaze-controlled text entry systems. This security breach allowed attackers to deduce the text entered on a virtual keyboard by analyzing the eye movements of a user's virtual avatar.
The GAZEploit attack utilized a supervised learning model trained on recordings of the Persona, eye aspect ratio (EAR), and eye gaze estimations. This model differentiated between various virtual reality activities like typing and entertainment, like watching movies or playing games.
By mapping the gaze direction to specific keys on the virtual keyboard, attackers could reconstruct the keystrokes. The attack methodically considered the keyboard's virtual space location, offering a comprehensive approach to keystroke inference.
Upon responsible disclosure of the vulnerability, Apple swiftly addressed the issue in their visionOS 1.3 update released on July 29, 2024. The patch involved suspending the Persona component whenever the virtual keyboard was active, effectively neutralizing the threat.
In other news, the June 2024 Pixel update bulletin released patches for several security vulnerabilities, including elevation of privilege (EoP), remote code execution, information disclosure, and denial of service, which impact Pixel devices and Qualcomm components.