Apple T2 Is Vulnerable to Hacking and There Can Be No Fix for It
- Apple’s custom “T2” security chip can be accessed and abused by using two published exploits.
- The exploits are working even on the latest system versions, and they cannot be addressed with patches.
- Apple has been indifferent about this even though researchers have been reporting the problem to the firm for months now.
Apple T2 is the second generation security chip that was custom-made with Mac user safety in mind. It is the central point where all hardware controllers are integrated on, where the sensor, camera, and microphone activation approvals take place, its where encrypted keys are stored, where SSD “on-the-fly” encryption and decryption happens, and where the boot process passes from. Unfortunately, though, a team of researchers from Iron Peak has discovered a way to break into T2 by combining two known exploits.
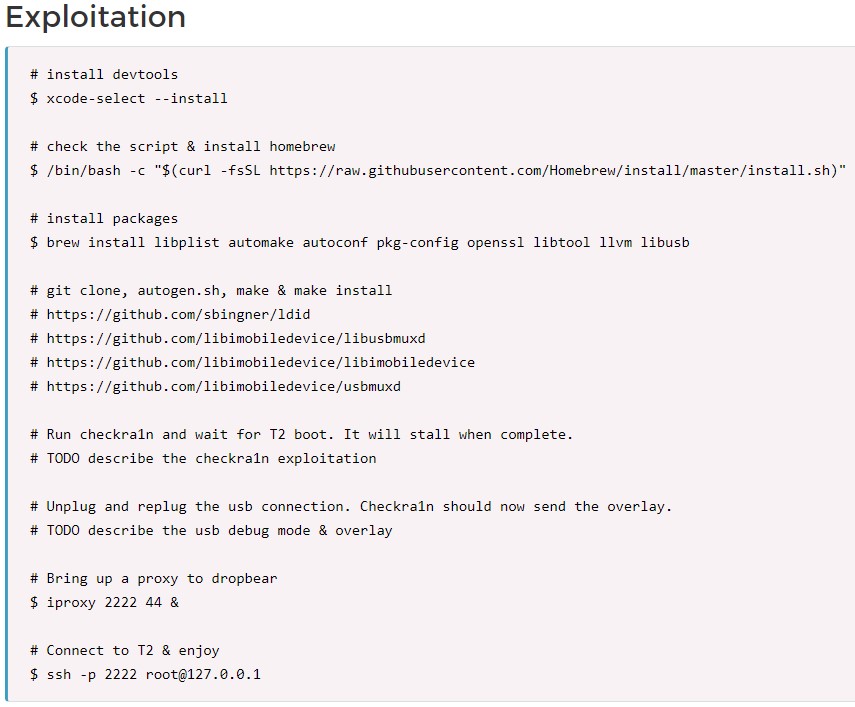
As they explain, the problem lies in the SepOS system that runs on the T2 independently of the macOS, which can be unlocked with the “checkm8” method. If this method is combined with the “blackbird” exploit, the internal “Device Firmware Update” check that would otherwise lock down T2 is bypassed, so access to this highly sensitive chip is opened. Accessing T2 practically means becoming a root user with kernel execution privileges, so essentially, the exploitation scenarios and possibilities are endless.
To make matters worse, because the SepOS was specifically made to be locked to a “Read-Only Memory” state for security reasons, Apple cannot possibly patch the flaw. All that they can do is to replace the chip with a new one, which would be out of the question for existing devices, of course.
If you’re wondering which Apple devices feature the T2 Security chip, you may check the following list:
- iMac introduced in 2020
- iMac Pro
- Mac Pro introduced in 2019
- Mac mini introduced in 2018
- MacBook Air introduced in 2018 or later
- MacBook Pro introduced in 2018 or later
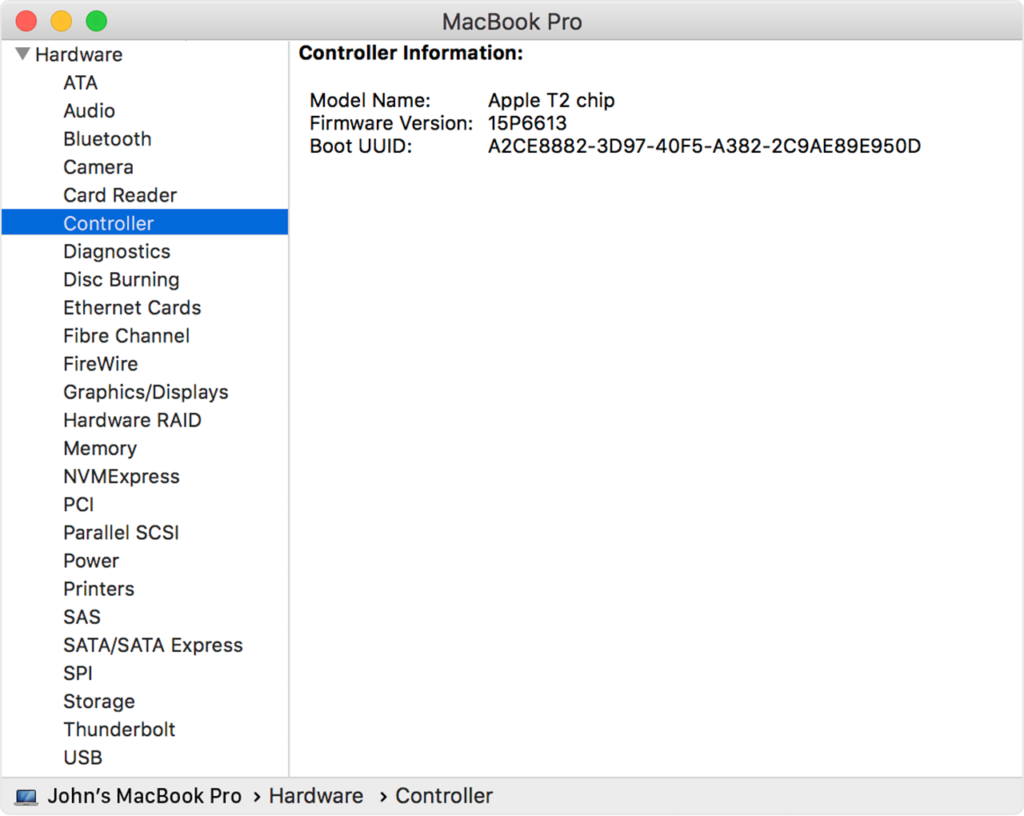
Alternatively, you may go to System Information, select Hardware, choose Controller, and check on the “Model Name” entry. If you find that your device uses the T2 chip, you should never leave it unsupervised because someone stealing it could unlock it. In general, we see this flaw in systems that use Intel processors along with the T2, whereas the A12 has fixed this problem.
As the ‘Iron Peak’ team points out, they have repeatedly tried to get Apple to accept this huge security issue with their T2 chip and fix it, but the tech giant just pushed this under the rug and denied to respond with some kind of feedback at least four times.
Even now, with the release of iOS14, a minor adaptation allowed checkra1n to work well again in managing to bypass all security mitigations. The hackers are using blackbird to access the Secure Enclave and disable all security measures in place. So far, Apple hasn’t made an official statement on any of that, but we’ll update this piece once they do.