Apple iMessage Phishing Campaign Asks Users to Disable Built-in Protection by Replying to Texts
- Threat actors found a way around Apple’s iMessage protection mechanism that automatically disables links from unknown senders.
- Scammers impersonate known entities and, using an urgent tone, ask users to reply to the phishing text to re-activate the flagged URLs.
- Besides the malicious link, the messages also include steps for the potential victim to take to disable Apple’s protections.
Apple iMessage users are manipulated into disabling the platform’s built-in phishing protection via phishing texts that impersonate entities such as USPS or toll collection agencies and ask receivers to reply. Once individuals follow the message’s directives, they become vulnerable to malicious links.
Apple iMessage has implemented a protection mechanism that automatically disables links in messages received from unknown senders, including both phone numbers and email addresses, to combat such attacks.
However, an Apple statement revealed a critical exception to this protection. If users respond to a malicious message or add the sender to their contact list, the links become re-enabled within the iMessage app, exposing the user to potential risks.
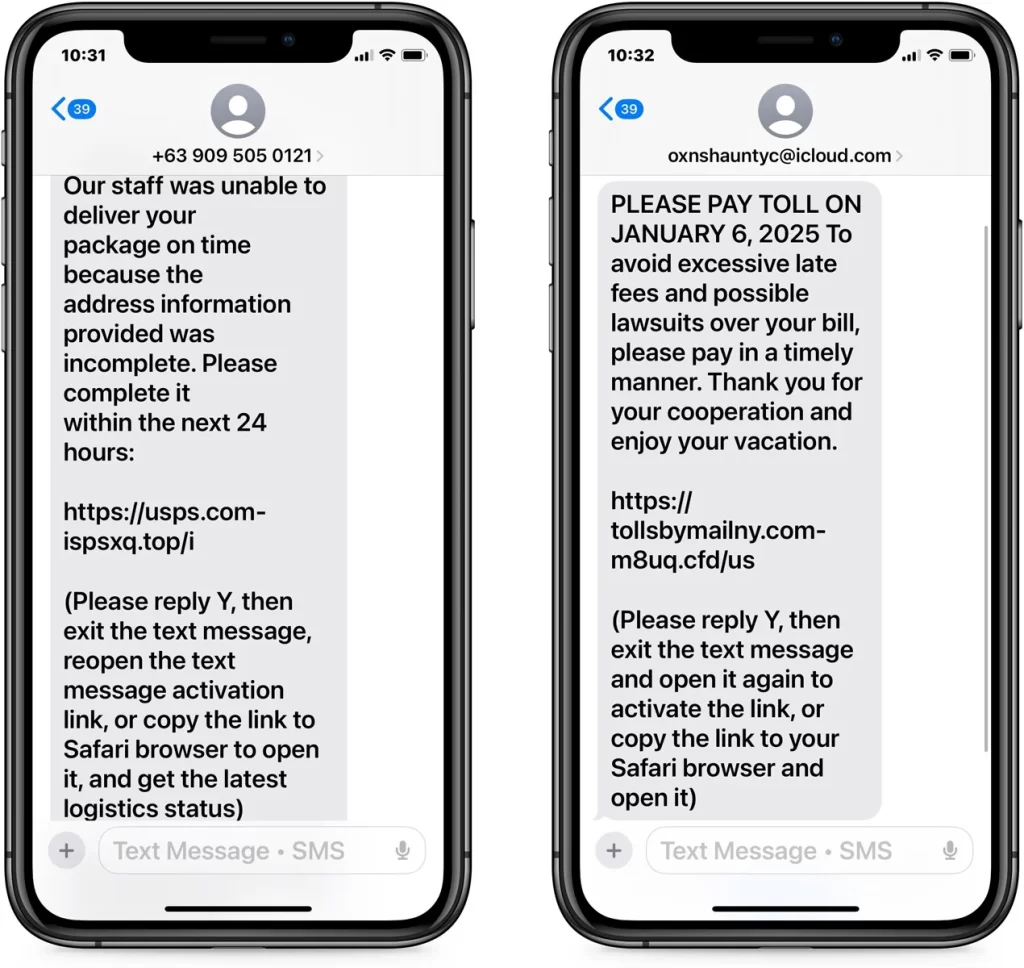
Over the past few months, there has been a significant increase in smishing attacks that exploit this exception to bypass iMessage’s security measures. The messages invoke issues like a failed delivery or unpaid road toll, urging recipients to reply in order to enable any disabled links.
For example, one smishing message reads, "Please reply Y, then exit the text message, reopen the text message activation link, or copy the link to Safari browser to open it." These instructions are an intentional ploy to reinstate active links within the text message, undermining Apple’s anti-phishing defenses.
This deceptive tactic has reportedly been used for at least a year, with notable surges in activity observed this past summer.
Threat actors capitalize on users' general familiarity with responding to text messages, particularly to opt out of subscriptions or confirm appointments by replying with "YES" or "STOP." This conditioned behavior makes it easier for unaware users to comply with these fraudulent prompts.
Clicking these re-enabled links can lead recipients to malicious websites that extract sensitive personal information, such as login credentials, credit card details, or other private data.
Alarmingly, even if users do not click on the links, merely replying confirms to the attackers that the recipient is an active target who responds to phishing attempts, thus increasing the likelihood of future attacks from similar threats.