Anubis Android Malware is Back With Thousands of New Samples
- Anubis is back with 17500 samples, spreading globally and stealing banking information.
- The malware comes with the same bag of tricks as before, and a couple of new capabilities.
- The distribution of the malware takes place through malicious APKs that pretend to help with system maintenance.
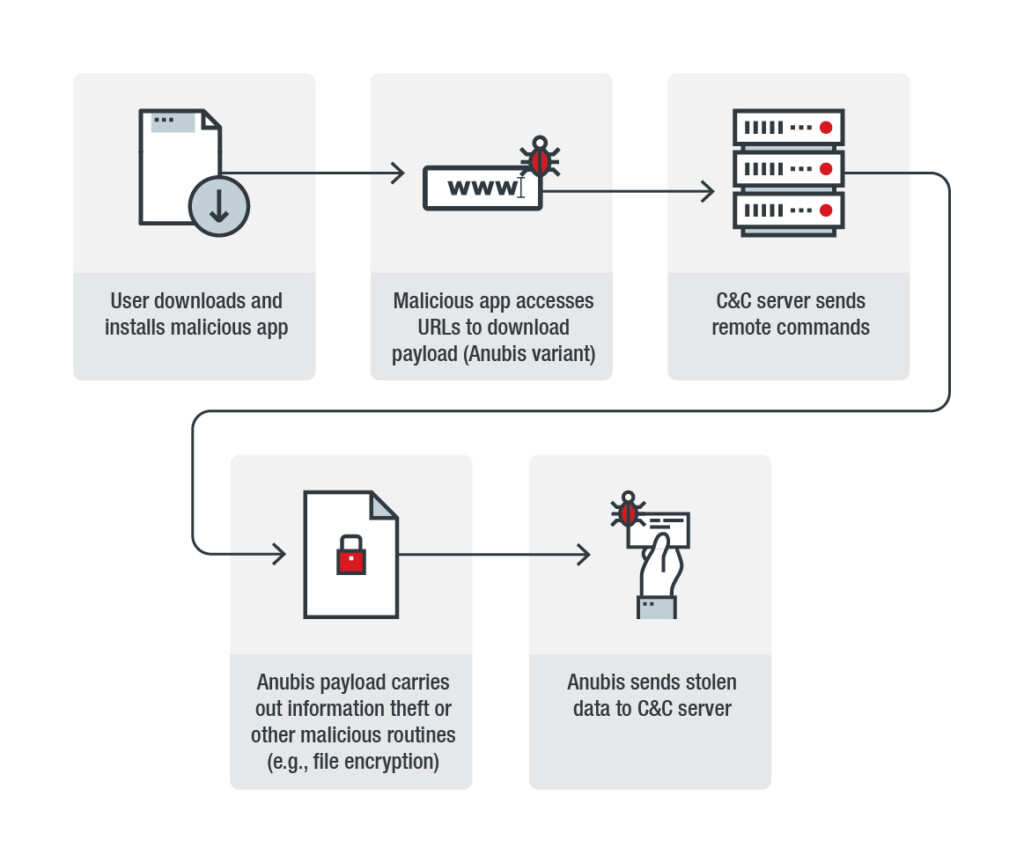
Anubis is a particularly nasty banking malware that hits Android devices and steals the payment information of its victims through a rich repertoire of tricks. Back in January, we saw how Anubis activated only when the user was on the go and not paying attention to what is going on in the device, how the malware pushed fake system updates, and how it was able to steal data from 377 individual financial apps by serving fake overlay screens. Trend Micro researchers have noticed a spike in the deployment of Anubis lately, warning people of over 17500 samples that are currently propagated globally.
image source: blog.trendmicro.com
In these campaigns, Anubis is packed inside malicious APKs that have names like “Google Services”, or “Operator Update” in various languages, tricking people into thinking they are downloading a system update utility. The newest samples of Anubis have the following technical capabilities:
- Take screenshots on the device
- Enable or configure admin settings
- Steal the contact list
- Open any URL
- Disable Google Play Protect
- Record audio
- Remotely control the device via VNC
- Send, receive, and delete SMS
- Check the device’s running tasks
- Lock the device’s screenshot
- Send text messages between apps and the device (USSD)
- Encrypt files on the device and on the SD card
- Search and locate files
- Get the device’s geographic coordinates
- Retrieve remote control commands from Twitter and Telegram
- Hijack a specified “Activity”
- Abuse the “WebView” feature to push overlays
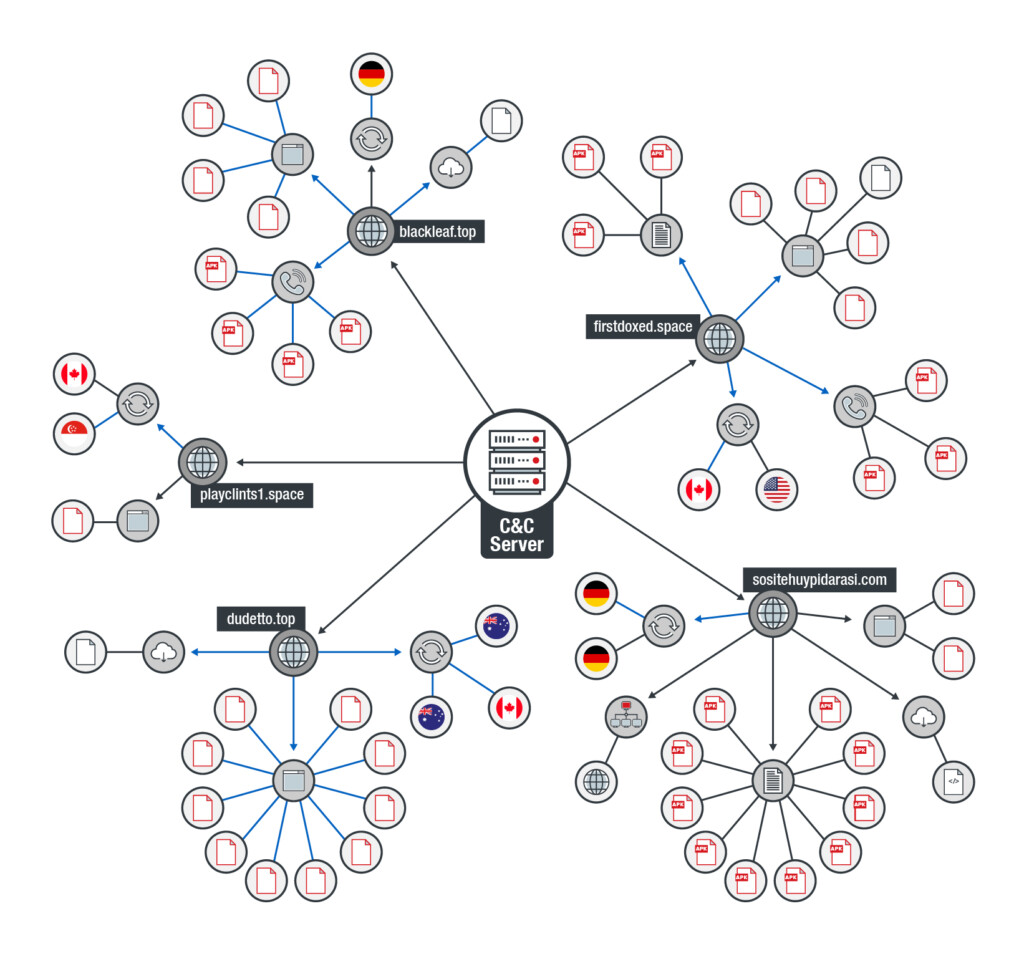
According to the analysis of the samples, Anubis is mainly targeting Poland, Australia, Turkey, Germany, France, Italy, Spain, U.S., and India right now, mimicking the login screens of financial apps that are used in these countries. The C&C infrastructure shows some level of versatility, with the servers being located in various countries, and having cloud service and internet data service abuse in the mix.
image source: blog.trendmicro.com
To stay safe from the Anubis danger, avoid downloading and installing apps (APKs) from untrustworthy sources, use a mobile security tool from a reliable vendor, and apply Android system and security updates when they become available. Even if Anubis gets activated when you’re not using your device, its activity traces can still be seen in the battery and network data consumption graphs that you can access in your device’s settings.
Have you ever had an Anubis experience? Share the details with us in the comments down below, or help us spread the warning by sharing this post through our social media, on Facebook and Twitter.