Android-Targeted SMS Stealer Campaign Infects User Devices in 113 Countries
- A malicious campaign stealing one-time passwords infected devices in over 110 countries, including Russia and India.
- The threat actors used automated Telegram bots and fake ads for legitimate app stores to distribute the SMS-stealing malware.
- Users’ one-time passwords coming from over 600 services have been intercepted by cybercriminals.
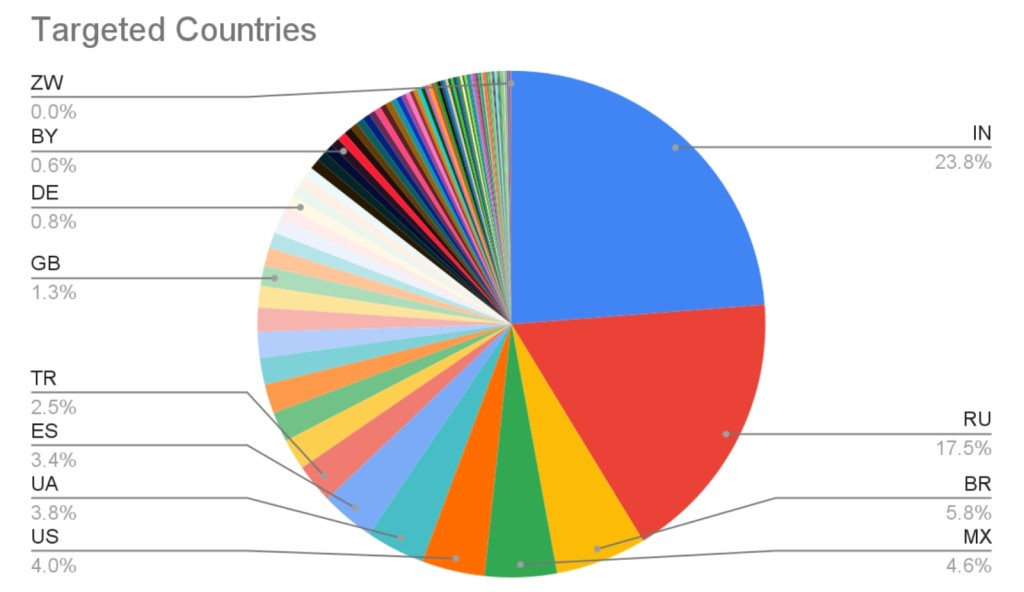
An SMS stealer campaign targeting Android devices was observed in 113 countries around the world, including India, Russia, Brazil, Mexico, the U.S., and more. The security research team at zLabs has identified over 107,000 malware samples, which the attacker tweaked over the course of the last two years to stay relevant and effective.
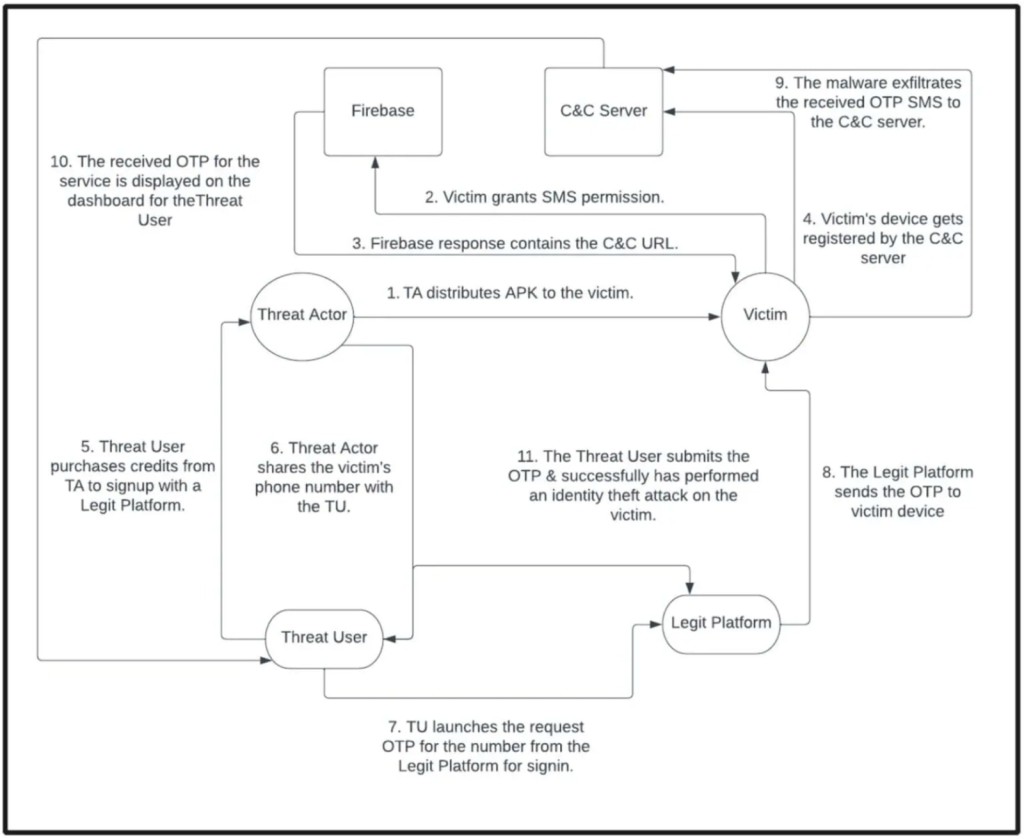
The malicious campaign infected Android devices with SMS-stealing malware that intercepted users’ one-time 2FA passwords (OTPs) for over 600 services. The malware was distributed via roughly 2,600 automated Telegram bots communicating directly with the target, also using fake ads for legitimate app stores as a lure, which downloaded a malicious app instead.
While interacting with Telegram bots to search for unofficial or free Android apps, some bots request access to the user’s phone number and send an APK (Android application package) that appears to embed the relayed phone number to personalize the attack.
Once the user installs the malicious app, it requests permission to read SMS messages, gaining access to sensitive personal data that some legitimate apps may require for specific, well-defined functions.
The malware then contacts its Command and Control (C2) server, which executes commands and collects stolen data, using Github repositories to retrieve the C2 address or even embedding the C2 server address directly within the app itself.
The C2 communication exfiltrates the stolen SMS messages it intercepted, including any valuable OTP codes, mostly the ones used for online account verification.
The security researchers discovered a connection between a website (fastsms.su) and one of the campaign’s malware samples. They discovered a complex C2 platform that accepted payment in crypto.
It had a user-defined geographic selection model that worked as a MaaS (Malware as a Service) with a range of service providers and their available phone numbers, displaying the OTP generated upon successful account setup.
Earlier this month, a now-patched zero-day flaw targeting Telegram for Android was up for sale on a hacker forum, which permitted displaying an Android app as a multimedia preview in chat, downloading a malicious APK payload on users’ phones.