Android Ransomware Poses as a COVID-19 Tracer for Canadians
- A new ransomware that spreads as Canada’s official COVID-19 tracing app has been discovered.
- The app is using a slightly modified version of an open-source ransomware project that’s available on GitHub.
- Researchers have developed a decryptor for this existing version, but future ones will be patched.
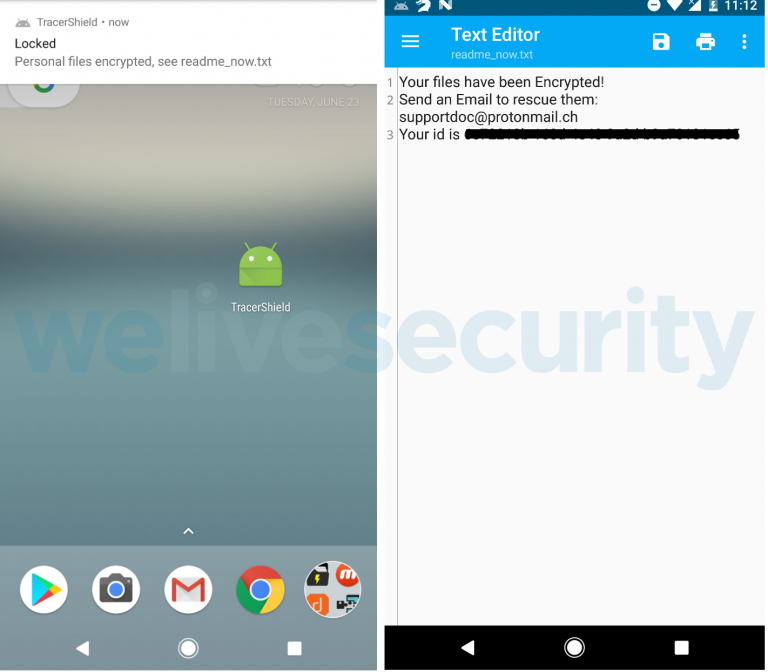
Canadian Android users will have to watch out for a new ransomware strain of the “CryCryptor” family, which is currently distributed under the disguise of the country’s official COVID-19 contacts tracing app, supposedly developed by “Health Canada.” Lukas Stefanko of the ESET research team has discovered this new malicious piece of software, and the team is already in the position to offer a decryption tool for those who have fallen victims to it. Moreover, the Canadian Centre for Cyber Security has been notified, and action to stop the spread has been taken.
The CryCryptor is partially locking down the device and encrypts the files stored on its memory, leaving a “readme” file on every directory. The file warns the victim about the state of their files and urges them to send an email to a Proton address to “rescue” them. A unique ID is also provided for the decryption key.
Source: ESET
Thankfully, none of this is needed, as a security weakness in the encryption system allowed the researchers to develop a decryptor. More specifically, the encryption key is stored in the shared preferences of the service that undertakes the process, so there’s no C2 communication involved. Of course, the actors will now realize their mistake, and future versions of the CryCryptor ransomware won’t be that easy to deal with. Considering that the encryption is using AES in combination with a randomly generated 16-character key, the first victims were fortunate for the existence of the flaw.
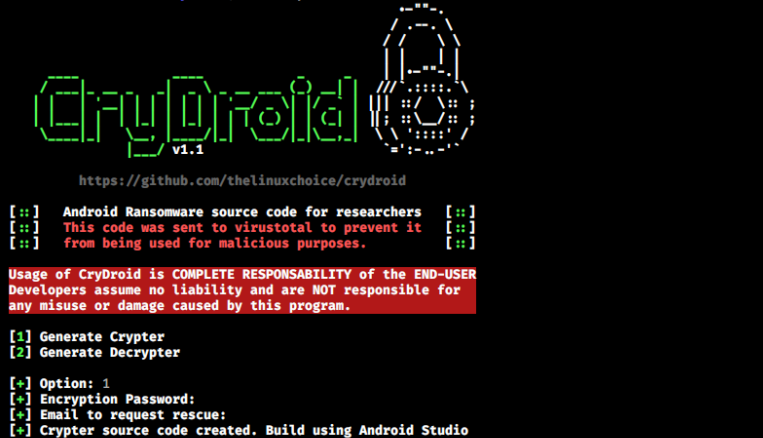
As for where this new ransomware strain comes from, CryCryptor is based on an open-source project that is hosted on GitHub - sharing many of the strings, as well as the app package name. This project is named “CryDroid,” and it doesn’t seem to be the product of research. It’s clearly an Android ransomware that is offered for free and can be easily modified to look like anything, really.
Source: GitHub
The two domains that were spreading CryCryptor were taken offline yesterday, but the actors are bound to return through other sites or even under a different disguise. That said, avoid downloading apps from outside the Google Play Store, use a mobile AV solution (and keep it up to date), and even better, avoid using any tracing apps in general. The discovered campaign has been active since at least June 12, 2020, and was very specifically targeted.