Andariel Group Used RID Hijacking in Recent Breaches, Security Researchers Confirmed
- The latest campaign orchestrated by the Andariel threat actor focuses on modifying a low-privileged account's Relative Identifier.
- By making the RID match a highly privileged account, the hackers can achieve system privilege escalation.
- They then create hidden local user accounts that evade detection through SAM-traceable common system commands.
The Andariel hacker group has a new campaign involving RID hijacking attacks during breach operations, which leverage sophisticated methods to manipulate system account privileges and gain unauthorized access while evading detection.
The AhnLab Security Intelligence Center (ASEC) has identified a new campaign by the well-known Andariel gang, which is believed to be tied to North Korea’s intelligence office.
RID Hijacking is an advanced attack technique where attackers modify a low-privileged account's Relative Identifier (RID) (e.g., general user or guest account) to match the RID of a highly privileged account – such as an administrator – and trick the operating system into granting the compromised account administrative-level privileges.
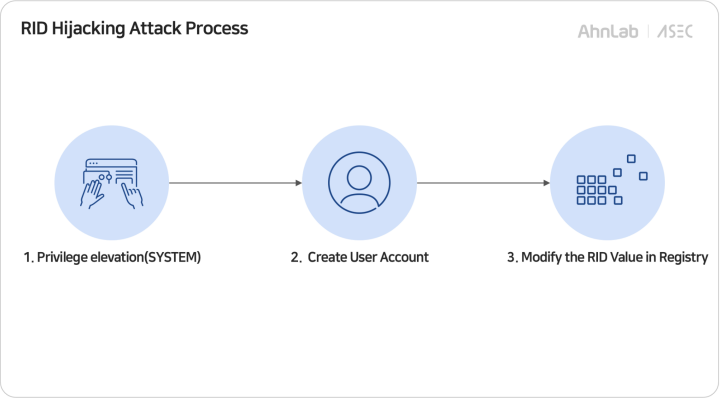
Recent breaches analyzed by ASEC have revealed the detailed steps deployed by the Andariel group to carry out RID Hijacking operations effectively: system privilege escalation, creating local user accounts, and modifying RID values.
Attackers must first escalate their privileges to access and modify the Security Account Manager (SAM) database to obtain SYSTEM-level access. The SAM database is the core repository for managing authentication and user account data within Windows.
Andariel attackers used tools like PsExec, a Microsoft utility, to remotely execute malicious files with SYSTEM privileges. This step is essential, as general administrator rights are insufficient for modifying SAM registry values.
The attackers strategically utilize existing accounts or create new ones for RID hijacking. They establish accounts with concealed attributes using the "net user" command. Adding “$” to the account name creates hidden accounts that evade detection through common system commands but remain traceable in the SAM registry.
Next, the hackers add it to critical groups, such as Remote Desktop Users and Administrators, using the "net localgroup" command, and leverage Remote Desktop Protocol (RDP) access for system control.
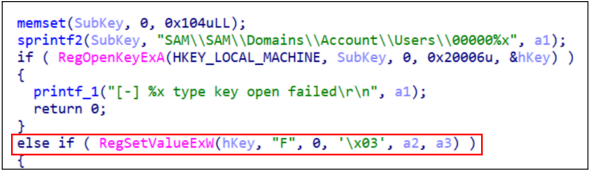
Altering the RID values of the new or existing accounts allows for privilege escalation. By replacing the RID value of the low-privilege account with that of an administrator account, the operating system recognizes the hijacked account as having administrative rights, allowing the attackers to carry out their objectives.
The Andariel group employed custom-built malicious files and open-source tools to execute RID hijacking with precision, such as modifying SAM registry access permissions, concealing accounts, and minimizing detection.
This technique has been previously highlighted by the Korea Internet & Security Agency (KISA), where Andariel was documented using RID Hijacking to create backdoor accounts. These hidden accounts allow attackers to maintain persistence, making them exceedingly difficult for victim organizations to detect.