Anatova is One of the Most Sophisticated Ransomwares Ever
- Anatova comes with multi-layered cipher key encryption that makes one-step decryption impossible.
- The ransomware is also wiping its traces and keys from the memory to prevent data dump and decryptor development.
- The analysts warn that they have detected signs of plans for the addition of extended functionality.
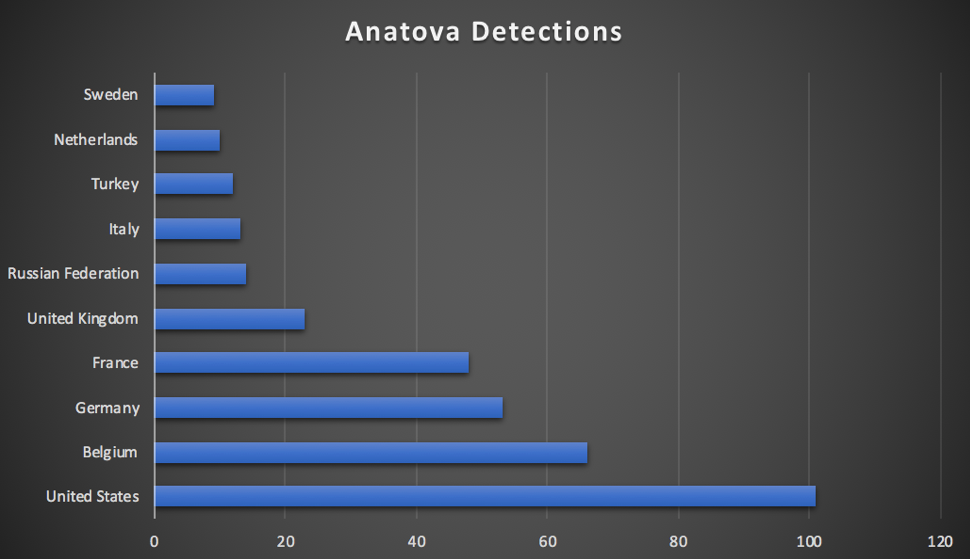
As the McAfee security analysts warn, the new ransomware family “Anatova” that was first discovered a few weeks back is one that was undoubtedly created by very skilled developers. Having infected systems from around the globe, the ransomware is preparing for its next “update” that will open up the gates for a modular extension. Right now, Anatova is already very robust, sitting behind unprecedented encryption and activity concealing features that make its tracking and analysis especially hard.
Anatova is a tiny (32kb) 64-bit executable that uses multiple encryption keys and dynamic system calls to encrypt as many files as possible in the infected system without leaving a detectable or analyzable trace. The malware gets the kernel32 functions and then proceeds with similar procedures with other windows libraries like crypt32, advapi32, and shell32. If any of these first steps fail for any reason, Anatova cleans up everything and exits. If all goes well, it proceeds to detect the username (to identify if the machine belongs to a security researcher) and then checks the system language. CIT countries are being excluded, either because getting ransoms from there will be harder, or because the authors of Anatova originate from one of these countries.
Image source: securingtomorrow.mcafee.com
The interesting stuff comes next, as Anatova is encrypting all files on the infected system, using a random 32-bit key and another 8-bit Salsa20 key, creating a 2-layered ciphering result. As each string is encrypted by using the random key, each file features a unique encryption path. The private key is encrypted through the Salsa algorithm again, and create a BASE64 string in the system memory. Having created this Inception-like series of encryptions, all keys are wiped from the memory so nothing can be retrieved. To decrypt the files, one would be the Anatova authors to perform the Salsa20 key decryption, and then use the private RSA key that is unique to each victim.
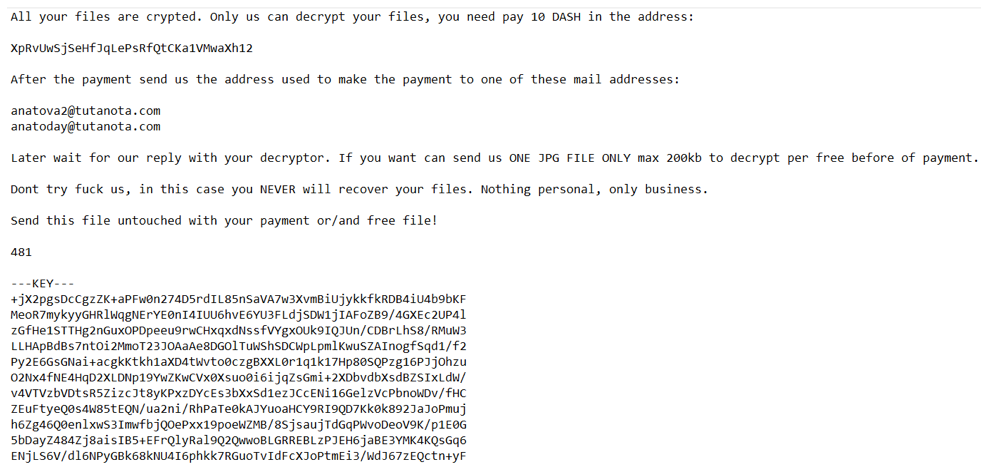
Right now, Anatova asks for a ransom of $700, providing free decryption of a 200-kilobyte .jpg image as proof. The payment is actually demanded in the form of the Dash cryptocurrency, so the corresponding amount may fluctuate or be adjusted in the future. As always, users who have been infected by Anatova are not advised to pay the ransoms, as there is no guarantee that they will get their files back. For now, Anatova stays well hidden and ready to get empowered by more features, as McAfee analysts discovered that it is almost ready to leverage two additional DLLs.
Image source: securingtomorrow.mcafee.com
What is your experience with ransomware? Share it in the comments below, and don’t hesitate to share this story through our socials on Facebook and Twitter, hearing more of the rise of Anatova.