Amazon Confirms MOVEit-Related Data Breach Exposed Employee Information
- Amazon announced employee details were stolen in the massive data breach that occurred via the MOVEit exploit.
- The announcement comes after a hacker claimed the breach on a cybercriminal forum recently.
- Lenovo, HP, HSBC, McDonald's, and more are also on the leak list posted on the hacker forum.
Amazon has confirmed that employee data was compromised following a breach at a third-party vendor. The breach, which involved the mass exploitation of the MOVEit Transfer software, was revealed after a threat actor claimed responsibility for publishing data on a popular hacking forum.
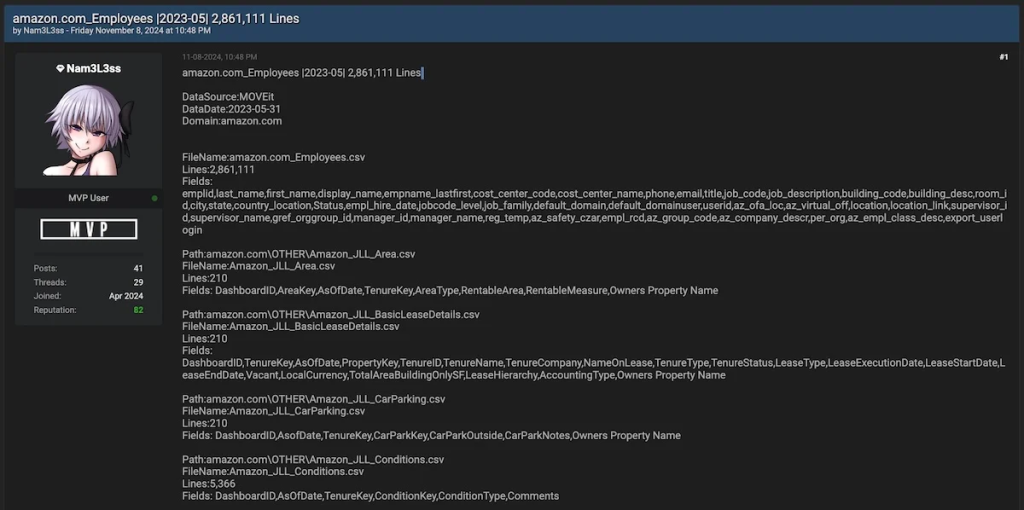
The stolen data reportedly includes work contact information such as email addresses, desk phone numbers, and building locations. Critical data, like Social Security numbers and financial information, were reportedly not accessed. The exact number of affected Amazon employees has not been disclosed.
However, the threat actor, identified as "Nam3L3ss," claims to possess over 2.8 million lines of data totaling over 250TB of archived database files, purportedly from 25 major organizations and obtained from other sources, including exposed AWS and Azure buckets and leak sites belonging to ransomware groups.
Lenovo, HP, TIAA, Schwab, HSBC, Delta, McDonald's, and Metlife are on the list of companies whose data was stolen or harvested.
Amazon spokesperson Adam Montgomery stated that the breach occurred at a property management vendor utilized by Amazon and several other customers. Importantly, Amazon's own systems, including AWS, remain secure.
“Amazon and AWS systems remain secure, and we have not experienced a security event. We were notified about a security event at one of our property management vendors that impacted several of its customers, including Amazon. The only Amazon information involved was employee work contact information, for example, work email addresses, desk phone numbers, and building locations,” Montgomery said.
This breach is part of a larger campaign associated with the MOVEit Transfer exploit, orchestrated by the Clop ransomware gang. The attack has impacted over 1,000 organizations globally, including significant breaches involving U.S. government services.
Amazon is working closely with third-party vendors to address security vulnerabilities and mitigate the impact of data breaches. The company is also taking steps to inform affected employees and provide necessary support.
Last month, security researchers discovered an Amazon Web Services Cloud Development Kit vulnerability that could have led to a full account takeover.