Almost Half of All Malware Now Passes Communications Through TLS
- Malware authors and malware campaign operators are now increasingly using TLS for their communications.
- This helps malicious actors blend with legitimate traffic, as in most cases, they are abusing legit services.
- Dealing with the problem is challenging, and that’s why threat actors are now massively adopting TLS for their operations.
TLS (Transport Layer Security) is a cryptographic protocol designed to provide security in communications over computer networks. It has been previously used by email platforms, instant messaging tools, VoIP solutions, and HTTPS (Hypertext Transfer Protocol Secure), among others.
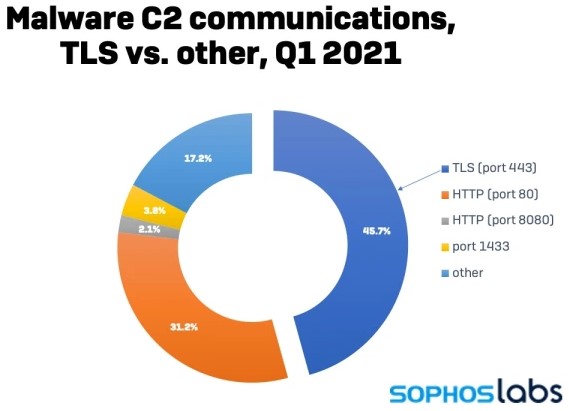
As Sophos researchers report now, there’s a surge of malware authors adopting TLS for their communications, rising to 46.7% of all samples analyzed in Q1 2021. This is both impressive and problematic, as having malware sending and receiving encrypted data practically means it’s harder to detect.
Here’s a breakdown of the communications protocols recorded by the Sophos labs in the first three months of 2021, showing TLS on port 443 as the method that takes the lion’s share.
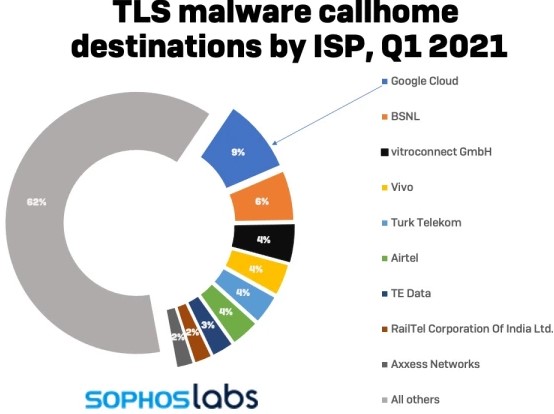
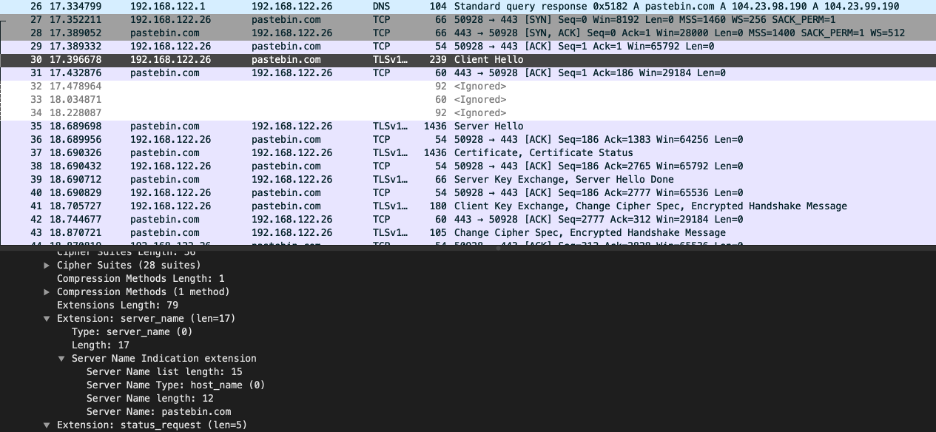
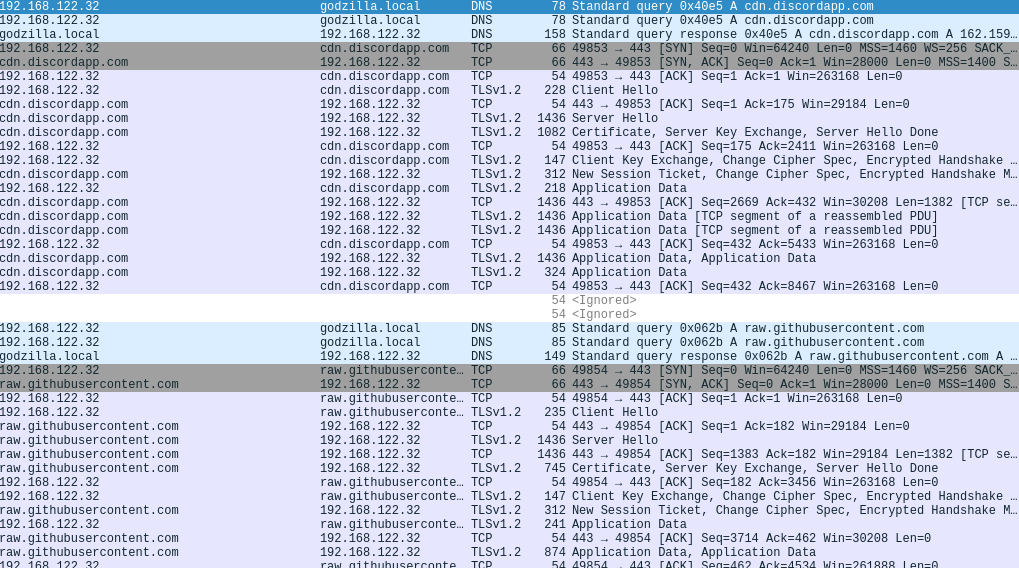
A noteworthy reason for this seemingly sudden rise in the adoption of TLS is the abuse of legitimate web and cloud services, which are in turn using TLS. Malware authors are using services like Google Drive, Github, Pastebin, and Discord because they help them evade detection, and TLS is one part of how that happens - with another being their good reputation, of course.
Approximately 9% of all TLS requests made by malware tools are accommodated by Google’s cloud services, making a clear case of the rampant abuse that the tech giant seems unable to deal with.
The most neuralgic part of a malware operation is using TLS on the infection stage because this is where AV tools have a chance to detect and stop the process. As such, the majority of TLS traffic that Sophos recorded comes from droppers, loaders, and payload fetchers attempting to hide the binaries from anything that may be scrutinizing network data packets.
But C2 communications are also often obfuscated with TLS, with HTTPS requests and TLS-based proxying being the two main ways to do it. Similarly, when the time for data exfiltration comes, most banking trojans are encapsulating the pack in a TLS-based HTTPS POST or export it via a TLS connection to a cloud service API.
Stopping this is technically complicated, and the only way to deal with the problem would be to see service providers ramp up their effort to shut the door to malware. Oftentimes, threats can be identified through a network monitoring solution that is configured to scrutinize non-standard IP port traffic that could be malicious.