Akira Ransomware Group Claims Cyberattack on Spain’s STE Group and Exfiltrating 30GB of Data
- The STE Group may have been impacted by a data breach that allegedly resulted in the leak of sensitive information.
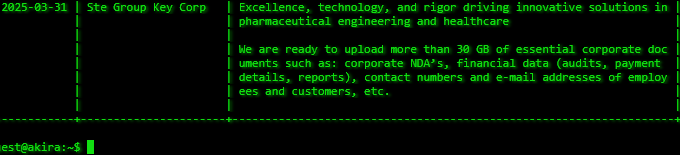
- Hackers claim to have stolen 30GB of corporate files from the Spain-based pharmaceutical and healthcare company.
- The data set reportedly includes NDAs, audits, payment details, and financial reports.
The Akira ransomware group has alleged responsibility for a significant breach targeting STE Group, a Spain-based pharmaceutical engineering and healthcare company. According to claims made on the group’s dark web leak site, over 30GB of sensitive data has been exfiltrated.
The data reportedly stolen includes Corporate NDAs (Non-Disclosure Agreements), financial information, and contact details:
- Sensitive NDAs that may impact STE Group’s ongoing partnerships and projects.
- Audits, payment details, and financial reports, which could potentially expose the company's internal financial structure and transactions.
- Email addresses and phone numbers of employees and customers were allegedly compromised, posing identity theft and phishing risks to these individuals.
The Akira group threatened to release this information, a tactic commonly used to pressure entities into paying hefty ransoms in exchange for keeping stolen data private.
The Akira ransomware group emerged in early 2023 and has rapidly gained notoriety for targeting businesses across multiple industries. The group utilizes double-extortion tactics, exfiltrating data before encrypting systems to maximize leverage over their victims.
They have mainly focused on organizations with weak cybersecurity defenses or outdated data protection protocols.
Recently, a security expert reverse-engineered the Akira ransomware process and discovered the encryption’s timing mechanism flaws, so the group’s victims have a way to potentially retrieve their locked data.