“Adrozek” Malware Is Silently Injecting Ads in Search Results
- Microsoft warns about a stealthy ad-serving malware that has spread extensively.
- The malware called “Adrozek” is changing browser settings and installs laced extensions.
- The goal is to make money by tricking people into visiting affiliate marketing URLs.
The sneakiest a malware attack is, the higher its chances of being successful. Microsoft reports about a new malware called “Adrozek,” which has been silently spreading without any researchers noticing, affecting internet users and many popular browsers like Google Chrome, Firefox, Edge, and the Yandex browser.
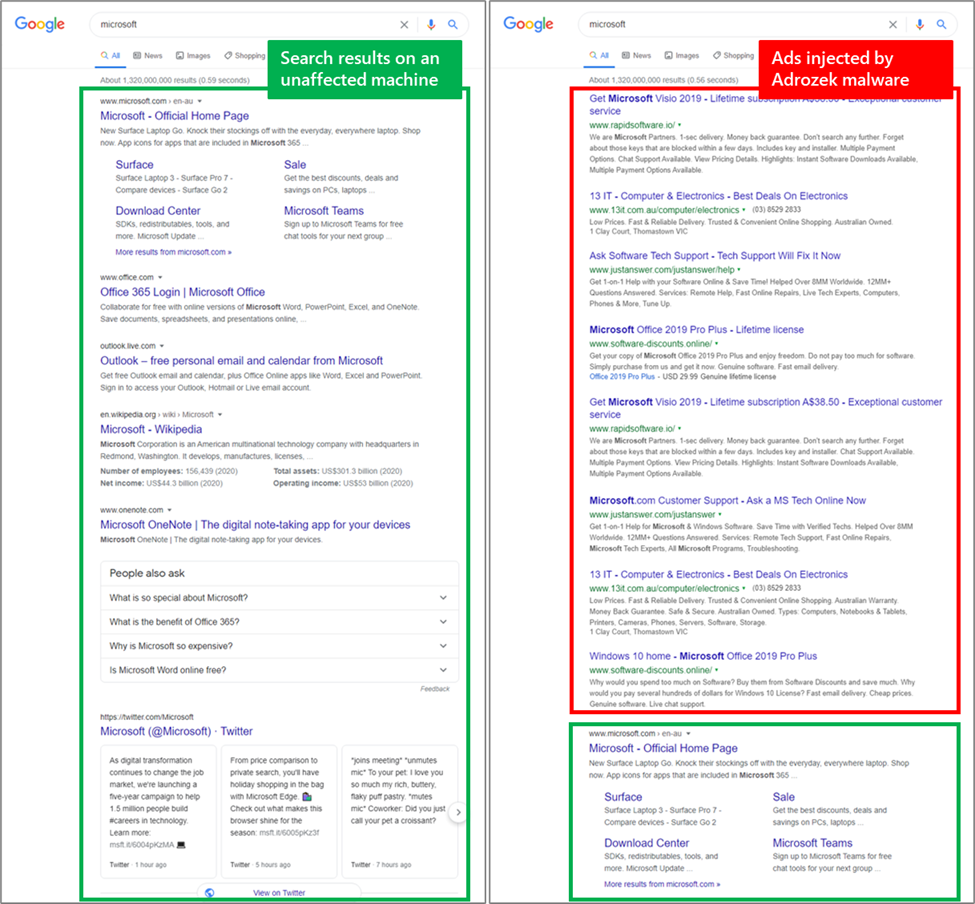
It is basically a browser modifier that adds extensions, modifies DLLs, and changes browser settings to insert malicious ads onto the user search results and make them appear legitimate.
The actors’ goal is to make money through affiliate advertising, so the victims aren’t running a serious risk, but they are still falling victims of abuse. In the end, they get search results that aren’t relevant to their interests, so their internet experience or even its personalization is severely degraded and undermined. In the case of Mozilla Firefox, Adrozek can even steal user credentials.
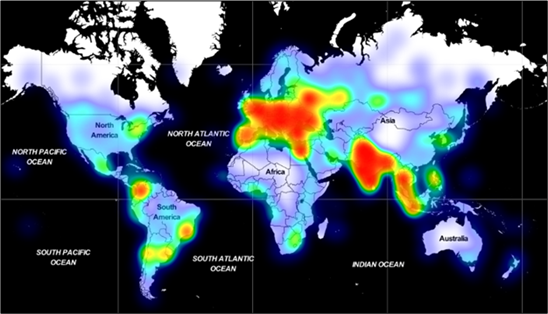
The most problematic areas right now are the whole of Europe, India, and Southeast Asia. Adrozek is dropped via drive-by downloads, while Microsoft has recognized at least 159 unique domains distributing a large number of samples. To avoid detection, the authors use a type of polymorphism, generating hundreds of thousands of slightly different malware samples that essentially do the same thing but have a different signature.
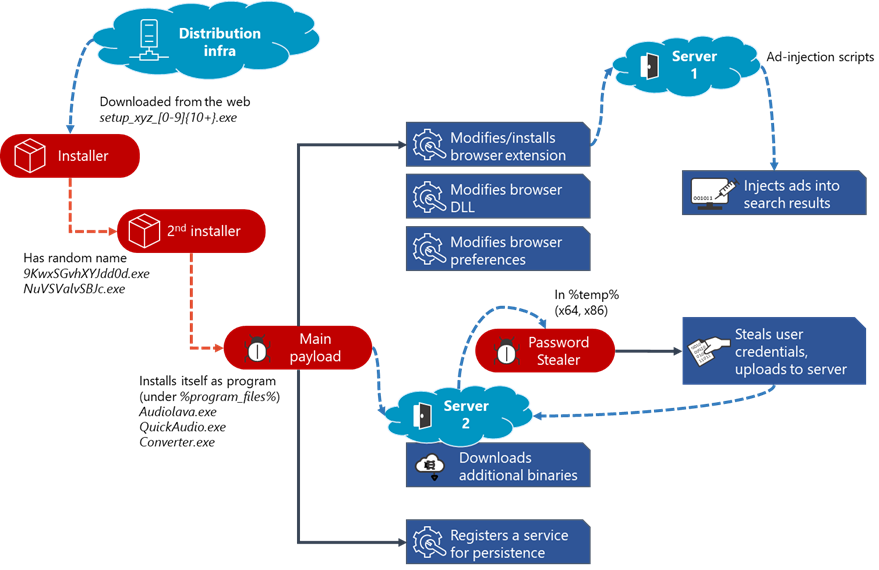
This also applies to the distribution infrastructure, with domains being frequently rotated, refreshed, or replaced. Some stay active for just a day, and others attempt to stay up for longer by reputation-cleaning tricks. The following diagram gives a picture of the attack chain and how Adrozek is distributed.
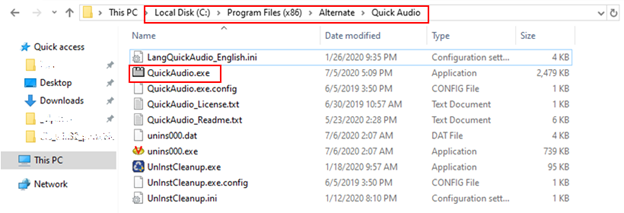
If you have it in your system, you will find it under ‘Local Disk (C:) / Program Files (x86) / Alternate / Quick Audio’. The “exe” file dropped by the malicious installer is “QuickAudio.exe,” making it appear as if this is something relevant to audio. Other names noticed by Microsoft’s researchers include “converter.exe” and “Audiolava.exe.” If you suspect an Adrozek infection, you should re-install your browser.
The extensions that are added onto the browsers use the IDs of legitimate extensions, but they are fake clones. The project that is masqueraded the most is “Radioplayer,” but of course, there are many more that are abused like that.
In all cases, the malware adds seven JavaScript files on these cloned plugins, sets the browser’s visibility to “hidden,” and even adds it in the incognito mode. Finally, the automatic updates of the browser are turned off so that the malware won't be uprooted by a security patch.