Cisco Talos Discovered a Serious Vulnerability in Adobe Acrobat Reader
- Attackers could potentially use JavaScript code to run code on the machines of victims arbitrarily
- Cisco Talos discovered the vulnerability and detailed its triggering process
- Adobe collaborated with Talos to release a fixing update marked with the “priority 2” rating
A report from Cisco Talos intelligence team reveals a severe vulnerability in Adobe’s one of the most widely used products, the Acrobat Reader DC. The vulnerability allowed an attacker to possibly execute code on a remote machine, using a custom PDF file containing malicious JavaScript code. The bug has now been fixed, as Cisco Talos and Adobe collaborated to resolve it, and the relevant update has already been rolled out.
Adobe Acrobat Reader supports the function of running embedded JavaScript in PDFs in order to accommodate higher levels of user interaction. This functionality, however, can be exploited by an attacker as the JavaScript code could potentially cause memory corruption in the machine of the user, leading to malicious code execution at a second phase. To trigger this vulnerability, the user would have to open the infected file which people could easily do since they consider PDF files as being generally safe. To make things worse, this PDF could be embedded in a webpage, so merely visiting it could cause trouble if Adobe is set to open web PDF files.
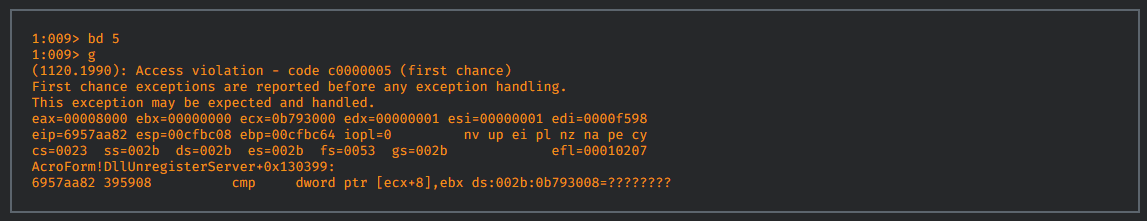
The malicious code could contain an incorrect integer size promotion, creating a regular expression with a very large string value, leading to the heap corruption. After a series of integer promotion executions, the loop continues to access out of bounds memory until it hits an unallocated page, and then the subsequent crash occurs:
The vulnerability has now been fixed, as Cisco Talos reported this find to Adobe and they worked together in resolving it. Adobe released the fix update with the “priority 2” classification, which corresponds to an “elevated risk” fix that has currently no known exploits. Thus, it’s a proactive fix, and all users are recommended to update their Adobe Acrobat Reader within 30 days. However, and considering the detailed publicity by Cisco Talos, you would be safer in updating right away. While we're at it, don't forget to read our other post on how to protect yourself from malicious PDFs.
Do you use Adobe Acrobat Reader for your PDF viewing? Let us know what your experience is with the famous piece of software in the comments below, and don’t forget to visit our socials on Facebook and Twitter to learn more about what’s new today.