Actors Engage in Social Engineering-Based Email and Voice Phishing Targeting Amazon Users
- Amazon users are falling to the trap of clever fraudsters who are sending phishing emails that pass through security filters.
- The actors are compromising the accounts of vendors to send messages to people who have submitted orders.
- In other cases, they sent emails containing a number to a fake “fraud protection” line that steals sensitive user details.
Armoblox has recorded a new wave of phishing attempts that take place against Amazon clients, involving both emails and voice messages (“vishing”). The new methods deployed by the threat actors manage to bypass email security controls because they do not follow standard practices, and are generally pretty tricky for the recipients.
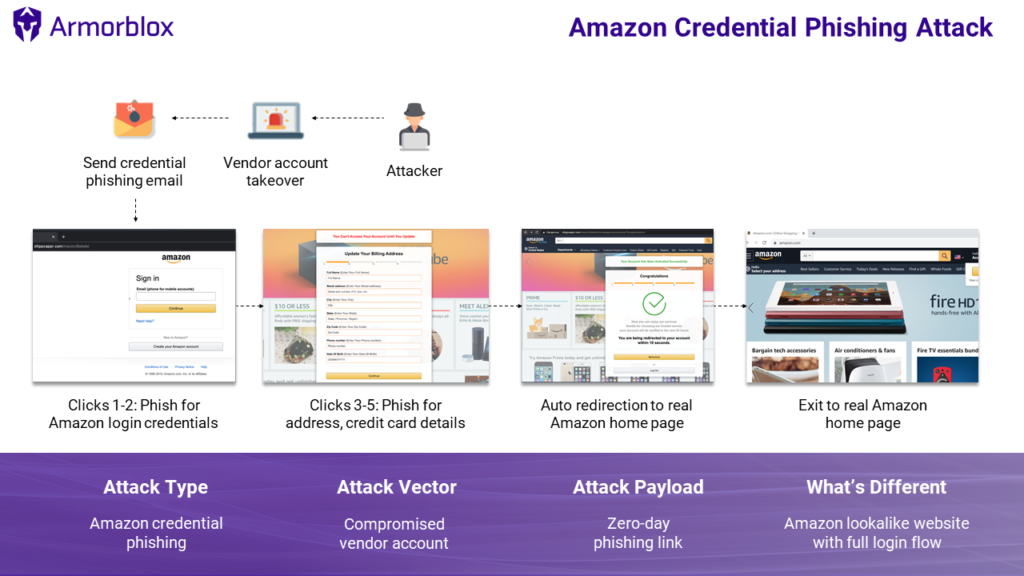
In many cases, a compromise on the vendor’s account and a full takeover creates the setting for effective social engineering attacks, so here’s how it’s done.
Source: Armoblox
The attacker takes over the vendor’s account on Amazon, and then sends credential phishing email messages to people who have placed recent orders to that merchant. The message informs the recipient that their order cannot be shipped due to a payment processing failure, and so they are asked to update their details.
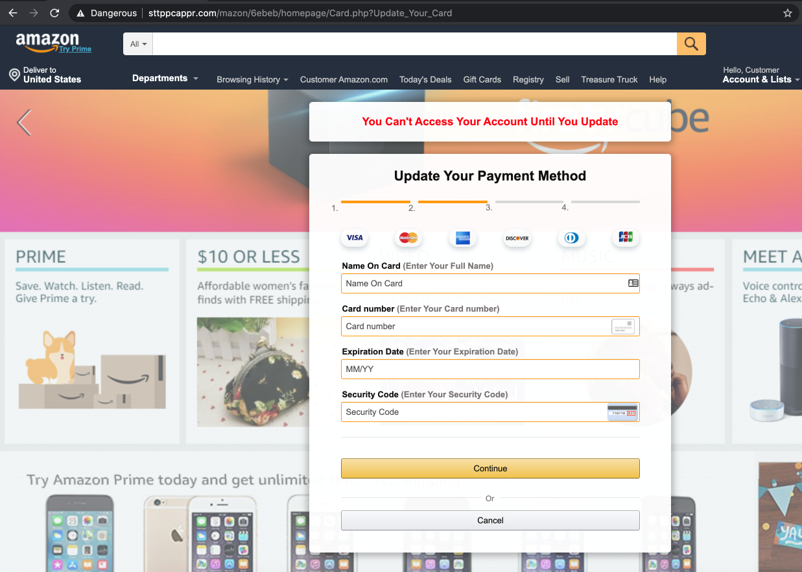
Clicking on the link takes the victim to a phishing webpage (sttppcappr.com), where they are urged to fill out a form. Once they do, they are redirected to the real Amazon website to dissipate any suspicions. The phishing page is very nicely-designed, easily convincing the careless visitor.
Source: Armoblox
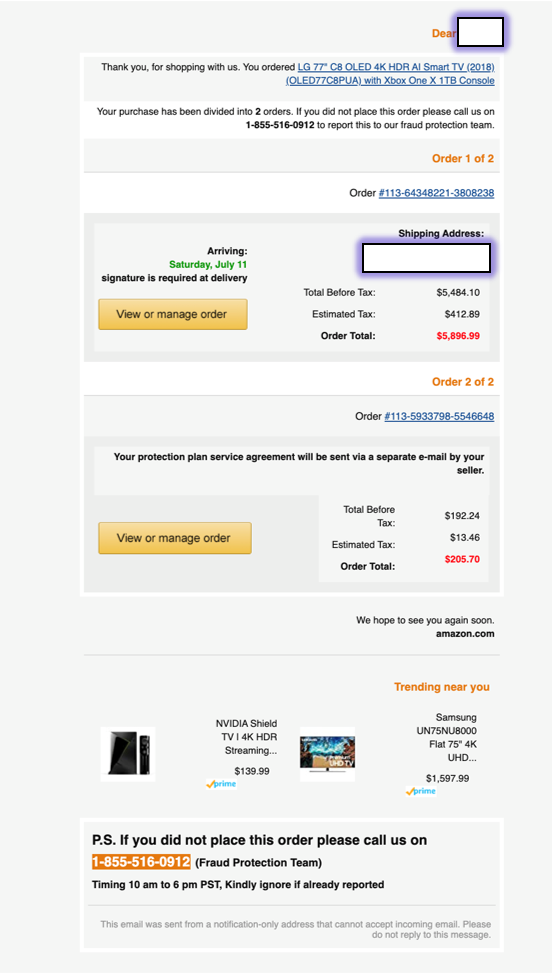
The voice phishing technique follows a different approach. Instead of taking over vendor accounts, the actors are creating Gmail accounts that impersonate Amazon (no-reply Amazon), and send carefully crafted messages to inform recipients that their order has been shipped.
The email claims that the recipient has placed a $6,000 order and urges the alarmed victim to call a “Fraud Protection” line using the number provided at the bottom of the message.
Source: Armoblox
If the target does call, a fraudster who impersonates a member of Amazon’s team will answer the call, convincing the victim that all that is happening is legit. The fraudster proceeds to ask for the order number, the caller’s name, and even their credit card details, supposedly to confirm that they’re handling a valid request. Once the victim gives away this information, the scammer ends the call and blocks the number.
The absence of links in the emails helps these messages to easily pass through security filters and reach more potential victims. Moreover, the fact that the sender hasn’t sent an email to the target address before helps them avoid any unexpected blocks along the way.
All in all, these attempts are based on the diligent design that is required for brand impersonation - Amazon, in this case - and a whole lot of social engineering. When receiving email messages, stay vigilant, stay calm, look closely, and identify fraud signs.
Read More:
- The New “Spox” Phishing Kit Makes Campaign Deployment Easier
- Phishing Actors Target “Office 365” Users Through Samsung and Oxford Servers
- Beware of “Sad to See You Go” Spotify Phishing Campaign