Actors Attempted to Harvest Database Credentials From 1.3 Million Sites
- A large-scale campaign has attempted to fetch database credentials for 1.3 million WordPress websites.
- The actors behind this campaign are the same who launched a similar scale XSS campaign last month.
- Admins are advised to reset their passwords, keys, and salts, as well as to check their configurations.
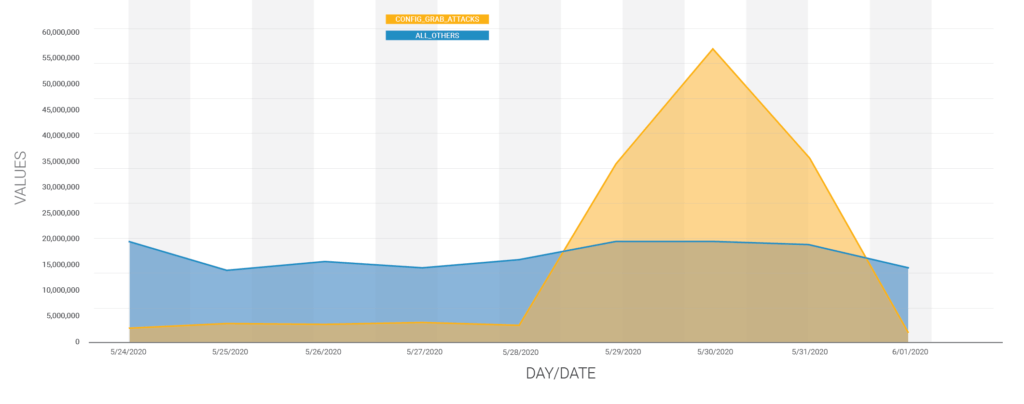
According to a Wordfence report, malicious actors have attempted to harvest database credentials from 1.3 million websites by downloading their configuration files. This large-scale campaign occurred between May 29 and May 31, 2020, and accounted for 75% of all attempted exploits across the WordPress ecosystem. The researchers were able to link this activity with actors who have engaged again in similar scale campaigns in the recent past. The following diagram gives a clear idea of the sudden surge of credential harvesting attacks.
Source: Wordfence
The database-password-harvesting actors are the same who engaged in the cross-site scripting attacks against 900,000 WordPress websites almost a month ago. The most common indicators of compromise provided by Wordfence this time are the following:
- 200.25.60.53
- 51.255.79.47
- 194.60.254.42
- 31.131.251.113
- 194.58.123.231
- 107.170.19.251
- 188.165.195.184
- 151.80.22.75
- 192.254.68.134
- 93.190.140.8
The signs that you have been targeted are left in the server logs, with the entries containing “wp-config.php” in the query string, accompanied by a 200 response code. This status code means that the request has succeeded, and the actor has managed to exfiltrate the database credentials. In some cases, the 200 response code is still given even if no data is transferred, although 404 and 301 would be clearer indicators of failure.
One protective step that you can take now is to change your database password, authentication keys, and salts. Although the campaign activity has subsided now, you never know when the next spike will happen. Moreover, make sure that your database is not configured to allow remote access - otherwise, someone could add an admin user and take over your website. Remember, if a hacker has your authentication keys, all other security layers can be easily bypassed or overridden. Finally, keep in mind that changing the database password without updating the “wp-config.php” file may result in the website being taken offline, so if you don’t know how to do it, ask your host for technical support.
These reports usually come only after the damage has been done, so it is essential to take a proactive approach when it comes to website security. Wordfence says they blocked 130 million attacks that originated from the particular campaign, but, of course, large-scale campaigns always find vulnerable targets to compromise. Website admins need to know what is going on out there, implement defensive mechanisms, update their WordPress installations, and also the plugins that are used, and finally, to use safer configurations when possible.