Access to the Networks of 7,500 Companies Offered on Dark Web Forums
- A hacker is selling access to the networks of thousands of companies for over a million USD.
- The organizations that have been compromised by that person are using unpatched software.
- RDP scanning has grown into massive proportions right now, and no vulnerable system is missed.
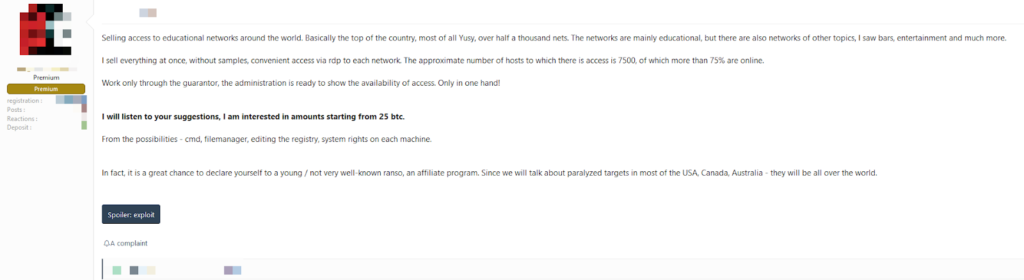
Someone is selling network access to 7,500 organizations based in the United States, Canada, and Australia. The hacker claims to be the only one in possession of RDP access to the particular entities and offers it all for purchase via an auction.
The initial bid was set to 25 BTC, which is about $386,600, but there’s also a “Buy Now” option that goes up to 75 BTC ($1,159,750). The listing appeared on multiple dark web forums that are populated by Russian users, once on October 3 and another on October 26.
This is a hefty price to pay to someone who may as well not send anything back, but we’re talking about a galore of networks here. Someone could deploy PowerShell tools, access files, edit the registry, change administrator rights, and plant spyware on the target systems connected with the compromised networks.
The possibilities of exploitation are limitless, and this pack is not to be used by one person alone. It would take a populous group of threat actors to take advantage of it properly.
RDP access sold by access brokers is a field that’s exploding right now, going hand in hand with the ransomware space. The main method hackers used to enter the networks was scanning unpatched systems and exploiting publicly disclosed vulnerabilities. It’s a “standard” process that has been streamlined through high-level automation, leading to tens of thousands of attacks each day.
These scans happen at such a scale right now that keeping unpatched systems online and hoping that nothing bad happens is just totally naive. If patching isn’t an option for whatever reason, retracting RDP ports that remain exposed should be the next best option. Finally, using an antivirus solution from a reputable vendor and setting up a strong firewall could save the day.
Remember, these actors are doing “bulk” scans, so they don’t persist much on specific targets. If your network’s configuration makes it even a tad bit harder to break it, actors move on to other targets as there are plenty of them out there. So, there is the basis for “security through abundance,” but you also need to do something to differentiate your systems from the pack.