A 13-Year Old Trojan Is Back and Used Against Worldwide Targets
- “Bandook” is back and getting widely deployed in the wild, targeting entities in at least eight countries.
- The main infection vector is through documents that download macro-laced templates in the background.
- The original authors and operators of Bandook could be selling access to the trojan to other actors.
A 13-year old backdoor trojan known as “Bandook” appears to have returned in the wild, going after a large variety of entities in many countries around the globe, indicating that it’s probably being sold to hackers on the dark web. Bandook had almost disappeared completely in the past three years, while its most recent prominent deployment was by Kazakh and Lebanese governments in the “Operation Manul” and “Dark Caracal.”
Check Point researchers have been monitoring Bandook actors’ activity lately and have a detailed write-up where they present the associated infection chains.
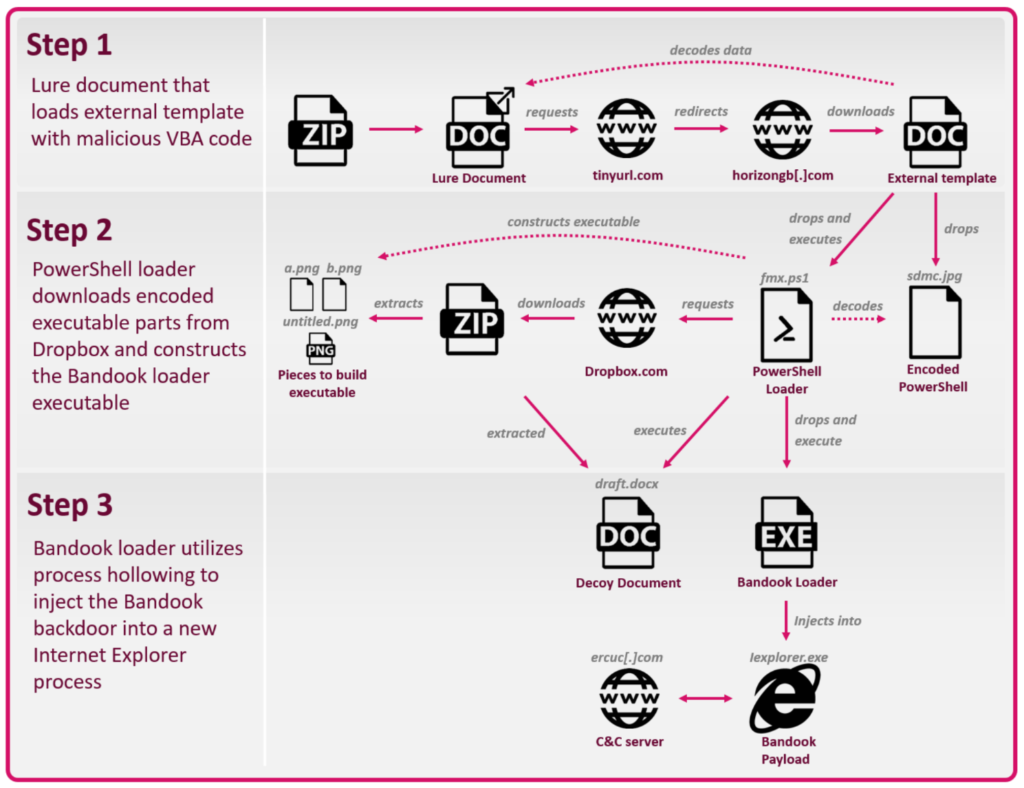
The infection begins by opening a lure document that loads malicious VBA macro code, so the main infection vector is via emails. The code loads base64 encoded PowerShell, which, in turn, downloads encoded files from Dropbox, assembling the Bandook loader onto the infected system. Once this is done, the “.exe” loader injects the backdoor into a newly started Internet Explorer process and establishes communication with the C2 server.
What is interesting is that the lure documents don’t contain the malicious macro code themselves, but instead, they use an external template for that. The templates look legitimate, even though the victim doesn’t normally get to see them.
They are downloaded in the background and provide the macro component that is required for the unfolding of the infection process.
Some document files that the researchers sampled can be found below:
- Malaysia Shipment.docx
- Jakarta Shipment.docx
- malta containers.docx
- Certified documents.docx
- Notarized Documents.docx
- bank statement.docx
- passport and documents.docx
- Case Draft.docx
- documents scan.docx
Of course, these may change any time, especially now that Check Point has revealed them.
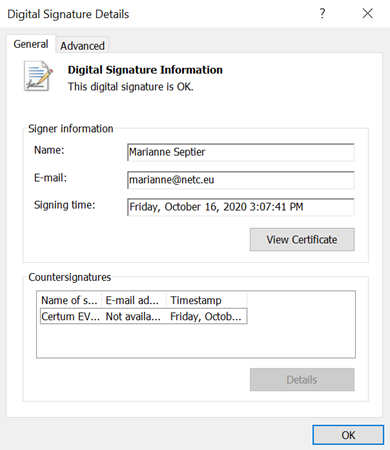
The Bandook malware used in the recent campaigns is a “light” version of the regular one, supporting only 11 commands, including file operations, screenshot capturing, file upload, file download, file execution, shell execution, and get public IP. As for the executable itself, it uses a valid Certum certificate, so it doesn’t appear as a threat to most AV tools.
The targeting scope is pretty extensive, including government, financial, energy, food industry, healthcare, education, IT, and legal institutions in Singapore, Cyprus, Chile, Italy, USA, Turkey, Switzerland, Indonesia, and Germany. This large-scale resurgence indicates that the original operators are selling access to Bandook, which could continue to be the case for a while.