MedusaLocker Remains One of the Primary Ransomware Dangers Right Now
- The MedusaLocker ransomware is a threat to network drives and inter-connected systems.
- The ransomware is running every 15 minutes, scanning for newly connected devices on the network.
- Medusa features a strong encryption implementation and quite a few Windows-related persistence mechanisms.
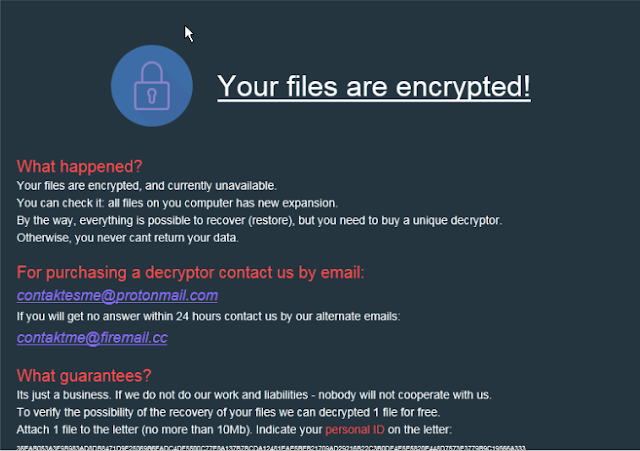
Researchers at Cisco Talos are turning their spotlight over the “MedusaLocker” ransomware, one of the most active and prolific malware tools in existence right now. The particular piece of ransomware was first deployed last year, but it has remained relevant through the development of additional variants, advanced persistence mechanisms, and deep network infiltration capabilities. MedusaLocker is combining a set of typical ransomware characteristics with the ability to map network drives, forcing their remapping and eventual content encryption. It means that if it finds its way into a single system on a network, it may cause extensive damage on all drives in that network.
MedusaLocker is copying itself to the %APPDATA%\Roaming\ directory, and then creates scheduled tasks on Windows with 15-minute intervals. This is for scanning for, locating and encrypting any media connected to the infected system or the network after the initial run. It is precisely why you are always advised to disconnect infected computers from the network. The ransomware is using the straight-forward “.encrypted” extension for the encrypted files, while the ransom note that is generated on all directories is quite typical. As for the encryption, all variants use AES 256 with an RSA-2048 key embedded in the executable.
Source: Cisco Talos
To deprive victims of the ability to recover their systems, MedusaLocker is also deleting the “vssadmin” utility from Windows, which is used for the restoring of shadow copies/backups. If users were able to restore from a backup, they wouldn’t pay the actors a dime. Additionally, MedusaLocker is attempting to force the re-connection of the infected system with the network, making use of a Windows registry entry for this purpose. To prevent this possibility, you are advised to disconnect the system in a physical manner, such as by removing the connecting cable, for example.
As Cisco’s team points out, to defend against the MedusaLocker threat, you should apply email and spam filters, perform regular updates on all system components, enable multi-factor authentication where possible, and use an up to date endpoint security software. As for the backup strategy, you should still maintain a solid plan in this regard, keep your backups offline, and only attempt to restore on 100% cleaned systems. Legacy security products won’t be enough with the particular ransomware strain, while common analysis and reverse engineering tools are also actively blocked by MedusaLocker.