The “Winnti” APT Group Is Back to Targeting Gaming Companies
- Activity attributed to the “Winnti” group of Chinese hackers has been spotted by researchers recently.
- The hackers are now targeting the creator of “Ragnarok Online,” the Korean “Gravity” gaming firm.
- The researchers warn that medium-sized highly promising German companies remain the main target of Chinese hackers.
The Chinese hacking APT (Advanced Persistent Threat) group known as “Winnti” has had its activity noticed again, and it looks like they have returned to targeting gaming companies. More specifically, security experts from QuoIntelligence report that they have spotted Winnti launching attacks against Gravity, a South Korean video game creator who is famous for the “Ragnarok Online” MMORPG title. Potentially, the reason why Winnti hackers turned their attention to Gravity is that people who are stuck inside due to Coronavirus are spending money playing games, and Ragnarok is a good destination in that regard.
Source: QuoIntelligence
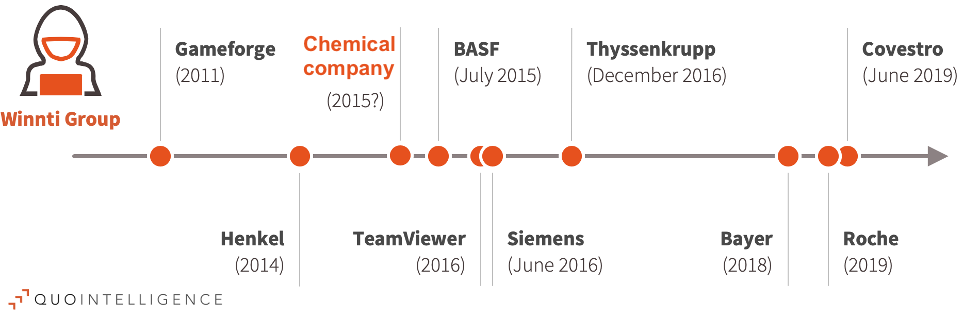
Winnti is generally acting as a cyber-espionage group, trying to steal valuable information from foreign entities. They are then selling this information to those who are willing to pay for it, or they are sharing it with the Chinese state. A year ago, we reported about the German pharmaceutical Bayer AG finding out that Winnti had planted a trojan in their corporate network. When the Chinese regime was facing the wrath of the Hong Kong students, the notorious APT was “caught” spying on the systems of the country’s universities again and trying to deploy a custom backdoor named “ShadowPad”.
Sometimes, Winnti is going after the required financial support, and QuoIntelligence believes that this is precisely the case with the most recent attack against Gravity. The researchers have already informed the Koreans about the attack and sent a notification to the local law enforcement agencies as well. The team noticed the first signs of Winnti activity on February 21, 2020, so this has been going on for a while now. Finally, there is clear evidence that leads to the particular attribution, from the C2 details, the collected samples, and the malware toolkits that were deployed.
Source: QuoIntelligence
Besides the Koreans, QuoIntelligence warns medium-sized German companies that they remain the main target of the Chinese APT. In fact, the researchers have detected and analyzed a previously undetected malware sample, which they are confident is the same that was used against a chemicals firm back in 2015. Thus, they were able to connect some new dots now, realizing that Winnti is responsible for past attacks that remained unattributed to this day. The Winnti group has been around since 2007 and is a highly-sophisticated hacking team that develops and deploys it’s very own custom tools. If you are responsible for the cybersecurity of a German “unicorn” company, you should be very careful and prepared against these threats.