Millions of Telegram User IDs and Phone Numbers Leaked Online
- Forty-two million records of Iranian Telegram users have been exposed online via an unprotected database.
- The data remained online and accessible for at least 11 days before the host took them down.
- Telegram and its various forks are very popular in Iran, but using unofficial software comes with risks.
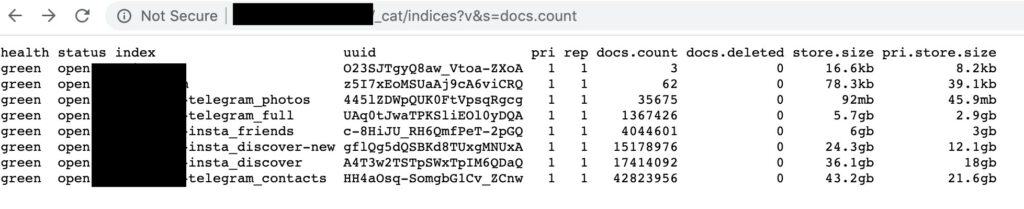
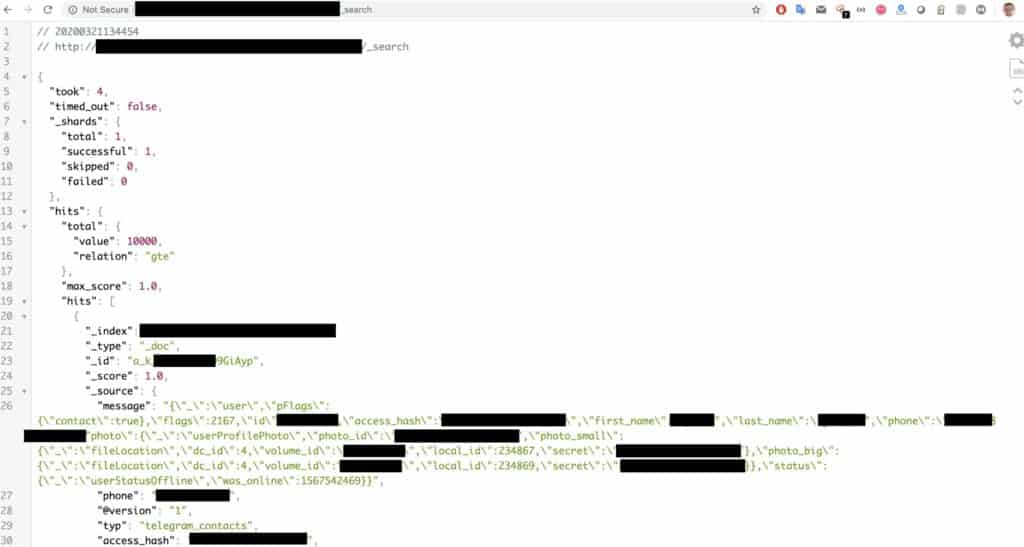
A fork messaging app that was derived from the Telegram source code has leaked 42 million records belonging to Iranians. The discovery was the work of researcher Bob Diachenko, who found the database online and accessible without any password protection. Each database entry contained the username (Telegram ID), the corresponding phone number, hashes, and secret keys. The owner of the database and uploader of the data had the name “Hunting System,” which is not affiliated with the official Telegram entity. As the owner would never respond, Diachenko notified the hosting provider, and the Elasticsearch cluster was deleted.
Source: Comparitech Blog
The date of the discovery is March 15, 2020, while the deletion of the cluster came 11 days later. It means that the 42 million records remained accessible to anyone with a Web browser for a significant period. As for the implications that resulted, for starters, the leak revealed the identities of those using Telegram (or a Telegram fork). In countries like Iran, this alone should be a reason for concern. Secondly, the exposed individuals are now at risk of getting SIM-swapped, and eventually, have their Telegram account taken over. Thirdly, phishing, and scamming via SMS is always a possibility too.
Source: Comparitech Blog
Telegram and its various forks are very popular in Iran, counting over 50 million users. If the above are unique entries, this exposure has compromised almost all Telegram users in the country. The reason why Iranians prefer to use Telegram is due to the end-to-end encryption that protects their communication from prying eyes, i.e., those of the government and the law enforcement authorities. Many people revert to using unofficial forks like the one responsible for this leak, because Telegram is blocked in Iran since two years ago, and one may only access it through proxies or via VPNs.
One explanation for this leak could be the negligence of the operators of the particular Telegram fork. Another answer could be the compromise of the data of this fork by the Iranian authorities, which could be “hunting” for Telegram users in the country. A third scenario, however, could link the app indirectly with the authorities, making it their creation. Remember, open-source code is available to anyone and not to a selection of ethical individuals, so anyone can create a Telegram fork and promote it to the users as trustworthy. The name “Hunting System” is one to get the cogs of conspiracy theorists turning for sure.