Zero-Day in LILIN Products Allowed Botnets to Spread Quickly
- Actors are exploiting a series of zero-day flaws in LILIN devices and planting botnets in them.
- The reason behind it is most likely to “zombify” the devices and use them as members of DDoS swarms.
- Most of the vulnerable products remain unpatched, and they’ll likely stay this way.
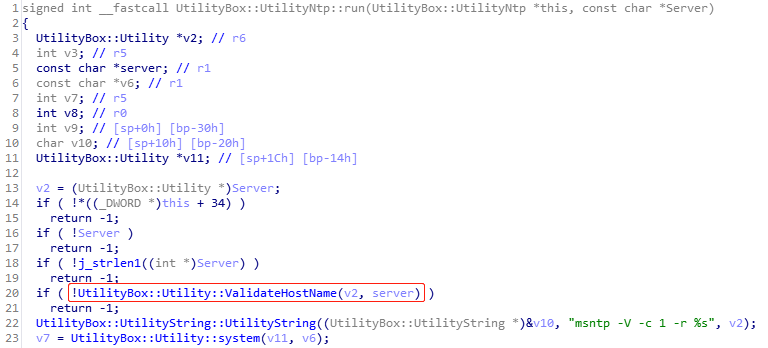
A team of researchers from 360NetLab has discovered that actors are using zero-day vulnerabilities in LILIN DVR and IP Camera products to propagate botnets. The recorded malicious activity involves three individual attack groups, spreading the Chalubo, Fbot, and Moobot botnets. The problem has started in August 2019, while the researchers notified LILIN in January 2020. A month later, the vendor released firmware version "2.0b60_2020207," which essentially plugs the flaws. The zero-day exploit was based on the existence of three vulnerabilities, namely a command injection flaw, an arbitrary file reading flaw, and the presence of hard-coded login credentials.
LILIN is a Taiwanese manufacturer of IP video cameras and recording devices with over three decades of experience in the field. They are an established entity in the field of IP video surveillance, and many thousands around the globe use their products. The products that are affected by the particular set of flaws are the following:
- DHD516A
- DHD508A
- DHD504A
- DHD316A
- DHD308A
- DHD304A
- DHD204 IP Camera
- DHD204A IP Camera
- DHD208 IP Camera
- DHD208A IP Camera
- DHD216 IP Camera
- DHD216A IP Camera
If you’re using one of the above products, you should update the firmware immediately. Some models were using a firmware version that dated as far back as in 2015, while others were vulnerable even with a firmware released in 2019. All problems were fixed with the latest versions, though, so you can grab the fixing firmware from LILIN’s download portal. The patched version stops the exploit chain by checking the server field and filtering out special characters, essentially making the command injection impossible.
Source: 360NetLab Blog
Checking the server field before writing the configuration also prevents the actors from modifying the FTP or NTP parameters, which was a way to inject backdoor commands and to access the DVR interface remotely. Finally, regarding the hard-coded credentials, these were the following: ‘root/icatch99’, and ‘report/8Jg0SR8K50’. Moreover, the devices were set to use ‘admin/123456’ by default, which is a pretty risky practice that still holds on.
The actors were possibly infecting the targeted LILIN products to launch DDoS (Distributed Denial of Service) attacks. Right now, there are more than 5,000 vulnerable LILIN devices connected online, and the vast majority of them remain unpatched. It will take many months to see some patching action taking place for them, and unfortunately, in most cases, this will never happen.