Moroccan Hacker Compromised Critical Infrastructure French Firms
- Many French firms were compromised by a hacker with unknown motives and goals.
- The information leads back to a successful “white-hat” security researcher from Morocco.
- The man explained that it all happened through his email, but from someone who had stolen it.
KrebsOnSecurity reports that a large number of French firms engaging in the provision of critical infrastructure services were targeted and partly compromised by an attacker who is based in Morocco. Reportedly, this same person has received accolades from big tech companies such as Microsoft, Apple, and Dell for responsibly reporting crucial flaws to them about their products. The victim list includes the French national power company, large hospitals in the country, one major French bank, a French car maker, a local airport operator, the state-owned railway company, nuclear research facilities, and various contractors of the French postal and transportation firms.
The first signs of the attacks became evident in 2018 when the IT teams of the victims noticed “njRAT” infections. This is the same piece of malware that was used against Samsung’s Service Centers in July 2018, and part of the “CypherIT” package that became so popular throughout 2019. The French entities were aided by the security firm “HYAS” which notified the country’s national computer emergency agency as well as the FBI. As it took investigators a while to respond, HYAS asked the identified Dynamic DNS provider to sinkhole the control servers behind the malware attacks in order to at least stop the malicious activity.
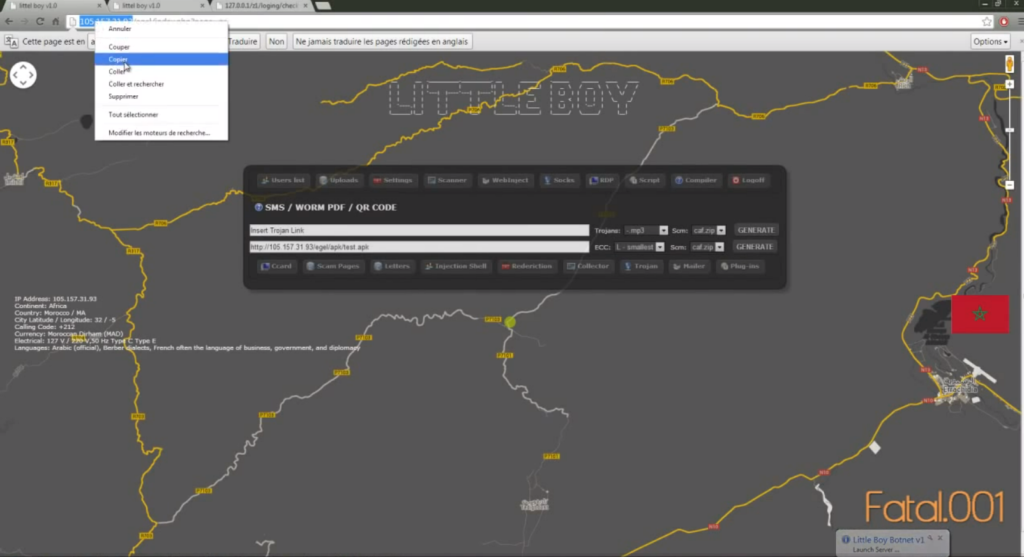
The next move was for HYAS to analyze the data that was shared with them by the DNS provider, where they figured that one of the registration keys was using an email address ([email protected]) which belonged to a legitimate business located in Morocco (talainin.com). This led back to the name of Yassine Algangaf, who has reported flaws in widely used software products in the past. In his Facebook account, the man has posted instructional videos on how to steal credit card numbers and passwords by using “Little Boy”, a RAT (remote access tool) that he developed himself. It all seems to add up nicely, but the man has refused having taken part in hacking operations when Krebs approached him on LinkedIn.
Source: KrebsOnSecurity
Algangaf admitted that the email address belongs to him, but he claims it was hacked in 2017, and recovered by him later. As for the RAT deployment tutorials, he explained that he publishes this stuff to raise awareness of potential security risks. He has also stated that “Little Boy” was just one of the many security research tools he has developed, that he sold no tools to others, and that he has no interest in “black-hat” activities in general. Maybe he’ll now have to explain all that in greater detail to the FBI and the French authorities, as we’re guessing that they have a few questions to address to the man.