The ‘Winnti’ Group of Chinese Hackers Targeted Hong Kong Universities
- Researchers found evidence of the Winnti hacking activity in at least five Hong Kong universities.
- The notorious group planted a new variant of their “ShadowPad” backdoor and tried to steal data.
- It is almost certain that the hackers were after the names of the organizers of the Hong Kong protests.
ESET researchers have discovered a new campaign launched by the notorious Chinese state hacking group known as “Winnti”. The targets of this new series of attacks are two Hong Kong universities (and possibly also another three), and the time of the detection coincides with the time the Hong Kong protests began. Based on the method of the attacks and the tools that were used, the researchers deduced that Winnti was trying to exfiltrate data from the compromised systems, and not to cause any disruptive damage.
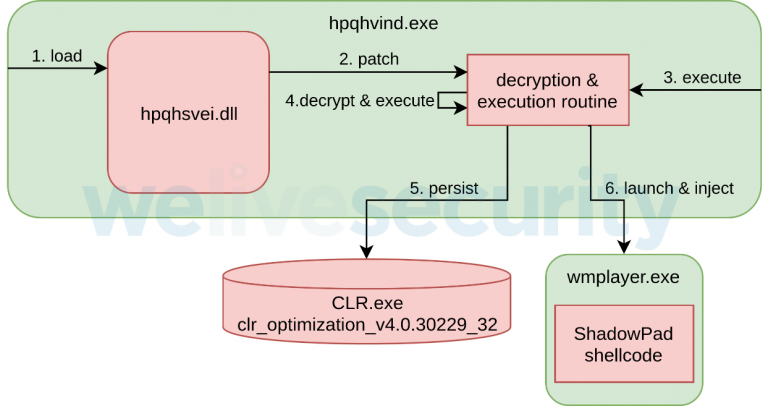
More specifically, the Winnti Group actors have deployed a new variant of the “ShadowPad”, which is one of their custom backdoors. This malware is capable of taking screenshots, conducting keylogging, parsing local files, and stealing browsing data and communications. For some reason, Winnti decided to replace their payload at some point, and use one that wasn’t obfuscated using VMProtect. This new payload was also missing the RC5 encryption that is typically present in Winnti’s tools. The 32-bit launcher of the ShadowPad is named “hpqhvsei.dll”, and it is used as a side-loading element when the victims launch the ‘HP Digital Imaging’ app which controls HP printers.
Source: WeLiveSecurity
Once the payload has established its presence on the infected machine, it is decrypted via an XOR loop, and then a shellcode execution follows. The backdoor is then taking some steps to ensure persistence, and finally, the modules are loaded as needed. This particular version deploys 17 different modules, and they were all compiled at around the same time. As for the network communications, ShadowPad starts a hidden MS Windows Media Player process and injects itself into it. Then, the ‘Online module’ contacts the C2 server, sets the firewall rules as needed, and starts listening on port 13567.
Winnti’s targeting of Hong Kong universities is not at all random. The still ongoing protests in the region were organized first and foremost by the local universities, so it is very possible that Winnti wanted to find out exactly who was behind these actions. In previous years, Winnti was engaged in cyber-espionage, targeting German industry leaders like Bayer AG (pharmaceuticals), and TeamViewer (technology). Kaspersky has also expressed their belief that Winnti was behind the “ASUS ShadowHammer” operation too, as the ShadowPad supply chain attack was used there too. For a full list of the indicators of compromise that concern this campaign, check out this GitHub repository.