Scammers Take Advantage of Iran-U.S. Tensions for Phishing Purposes
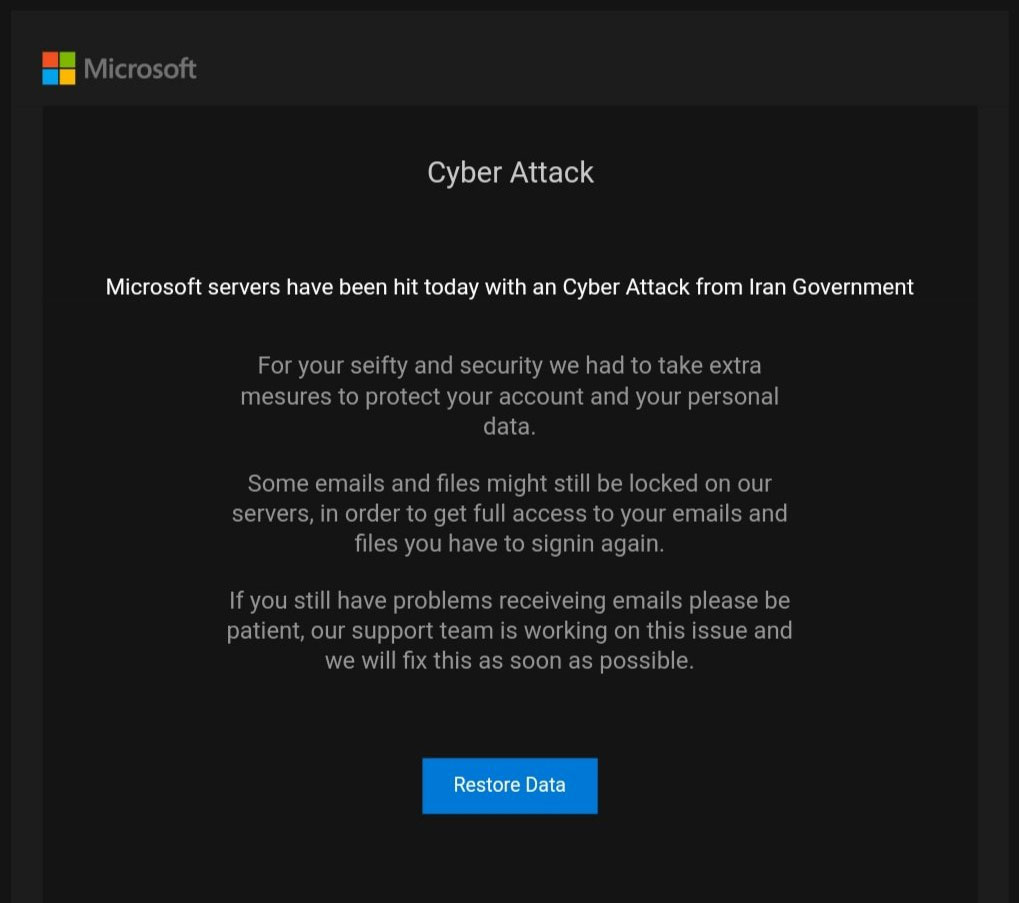
- Scammers have launched a phishing campaign pretending to be Microsoft MSA.
- The crooks are claiming that the recipient’s MS account was locked for reasons of protection.
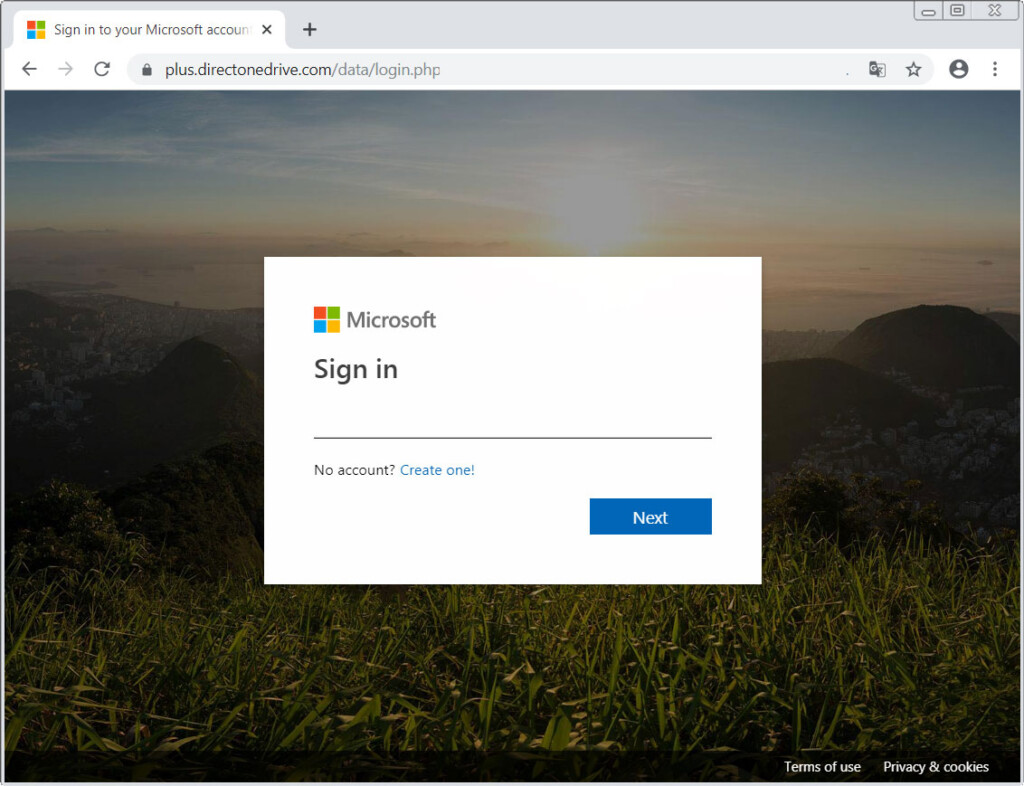
- The recipient is requested to login again, so they are redirected to a phishing page.
Following the killing of General Qassem Soleimani, the U.S. government and its cyber-security experts warned American organizations about the high chances of Iranian hackers seeking revenge online. Surely, pro-Iran actors have managed to make their statements almost immediately by hitting a couple of secondary U.S. government websites and defacing them to spread their message of retribution. This activity is a first-class chance for some to trick people into phishing scams, and crooks are always on the lookout for the slightest opportunity.
According to recent reports, scammers are sending phishing emails claiming to come from ‘Microsoft MSA’, and warning the recipient about a security breach that has occurred on the tech giant’s servers. Allegedly, Microsoft was forced to lock the email and data of the recipient in order to protect them from the Iranian government hackers. The message asks the recipient to log in again to gain back access to their Microsoft accounts, presented as a precautionary and protection step. As the users report, the emails of this campaign somehow manage to get through the Outlook spam filters and arrive on the people’s inbox. This detail is increasing the chances of success for the actor exponentially.
Source: Bleeping Computer
If the recipient clicks on the “Restore Data” button that is embedded in the phishing message, they will be redirected to a phishing webpage that looks very similar to Microsoft’s legitimate login page. Those who are careful enough will notice that the URL is way off what it should be, but not everyone will observe this. If the username and password are entered on that form, the actors will grab them for future credential stuffing attacks, more targeted phishing, account takeover, or just sell them on the dark web.
Source: Bleeping Computer
As always, when receiving messages that make bold or weird claims, chances are that they are phishing attempts so always treat them as such. If you’re still curious and want to click on buttons or links that are on the message, check the URL that you've landed on, seek for the existence of a padlock, and activate your online security suite. Even with all the above, you still can’t be sure that you’ve landed somewhere safe. If someone is urging you to login onto a platform, open a new tab and login on that platform from the official website instead of following the email link.
Have you received an email like the above? Share your experience with us in the comments down below, and help us spread the word of warning to others by sharing this post via our socials, on Facebook and Twitter.