Ransomware Actors Exploiting iTunes and iCloud Zero Day on Windows
- Researchers have discovered a blunder in Bonjour’s coding, which introduces a well-documented flaw.
- A capable group of malicious actors have found it and have been exploiting it since August this year.
- Apple has fixed the zero-day last week, so users of iTunes and iCloud on Windows need to update.
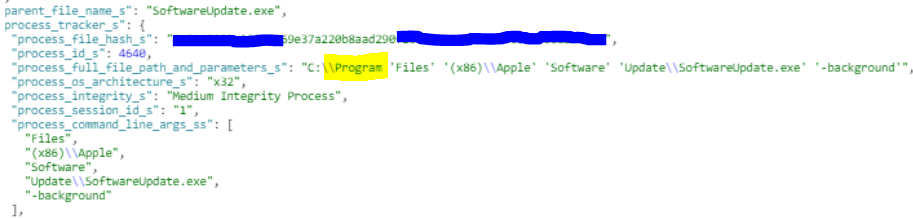
According to a report by security researchers of Morphisec, there’s an ongoing ransomware campaign that exploits a zero-day vulnerability in the Bonjour updater. Bonjour is Apple’s software updater that comes bundled with iTunes and iCloud. While Apple has decided to sunset iTunes for macOS, Windows users will continue using it indefinitely. As reported by the researchers, they noticed attacks that abused an unquoted path to maintain persistence and evade detection, based on a technique that was first discovered 15 years ago. That said, this is a case of carelessness from the developers of Bonjour and at the same time, thorough research from the attackers.
Even if iTunes is uninstalled from the system, Bonjour remains there as it is a separate program that needs to be removed individually. In most cases, users are not aware of this, but the attackers are. This leaves thousands of enterprise-level systems vulnerable to attacks due to the existence of Bonjour, which remains active in the background. If the iTunes has been removed from the system, Bonjour doesn’t have anything to point at, so there are no update checks and patch downloads, yet the utility is still running.
By taking advantage of the “unquoted path” flaw, the attackers can execute ransomware executables (BitPaymer in this case) through Bonjour without the AV tools catching the activity as suspicious. Bonjour is a signed app from a trusty vendor, so whatever runs through it is treated with trust by AV solutions. The malicious file can be placed anywhere, and the only requirement for the attacker is to have write-privileges for the containing folders. The researchers have observed no successful privilege escalation attacks, but this could be theoretically possible if the actors were going for that.
Source: Morphisec blog
The attacks that were observed and analyzed are attributed to the “BitPaymer/IEncrypt” group, who is a notorious and very capable malicious actor. The first signs of this activity appeared in August 2019, and Apple was almost immediately informed of the vulnerability. The tech company released fixing patches for iCloud and iTunes on both Windows 7 and Windows 10, along with a relevant security advisory.
Have something to comment on the above? Let us know of your opinion in the section below, or on our socials, on Facebook and Twitter.