Varenyky Malware is Recording People’s Screens and Delivers Sextortion Messages
- Varenyky is a new breed of malware and spambot that records people’s screens using FFmpeg.
- The malware is also capable of stealing user credentials right from the Web browser.
- The actors demand 750 Euros from the victims and threaten to publish their intimate moments on social media.
Porn extortionists are usually delivering empty threats to their victims, trying to convince them that they have them recording doing nasty things in front of their computer camera. However, in almost all cases, the actors cannot materialize the threats as they have recorded nothing. According to a recent report by ESET researchers, a new malware tool called “Varenyky” is changing this, as it’s able to record porn on the screen of the infected machines, and then distribute sextortion spam that is much more compelling and convincing than a typical sextortion scam.
The researchers report that the campaign which deploys Varenyky is focused on the subscribers of the French ISP Orange S.A., and the first signs of this new spambot were noticed by the team back in May. Right now, the campaign is still active, so people not only in France but everywhere are advised to be very careful. Moreover, they warn that Varenyky is under heavy development at the moment, so it’s adding more features and power on a daily basis. At its current state, it is using the FFmpeg open-source suite to record audio and video on the infected computer.
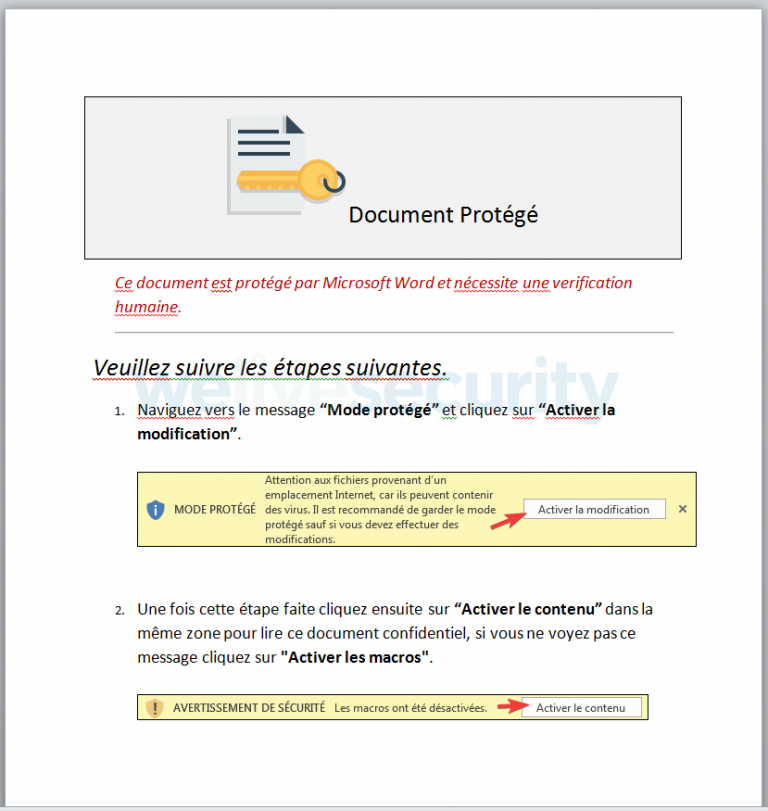
The distribution of Varenyky occurs through email which carries malicious document attachments. The topic of the mail concerns a bill of a few hundred Euros that are supposedly available to the recipient and only require “human verification” to claim. The verification process includes the enabling of the macro's functionality on the victim’s office suite so that the malicious code can run in the background. Everything is written in French, and the malware has an active filter to exclude potential victims that are using an unsupported locale. The identifier even excludes Belgians and Canadians who also speak French.
Image source: welivesecurity.com
One of the features that were added onto Varenyky at a later stage was the ability to deploy NirSoft’s WebBrowserPassView and Mail PassView tools, enabling the malware to steal user passwords and exfiltrate the data to the C2 server. This is to cover for the inability to screen-record these inputs. Besides that, Varenyky can also click on the screen, read the text, navigate menus, perform window management actions, open Web browsers, and execute things on the 'Windows Run' dialog.
Image source: welivesecurity.com
As for the extortion mail that will reach those who were recorded while visiting adult content websites, it is asking for an amount of 750 Euros in Bitcoin paid during the time-frame of 72 hours before the video is sent to family, colleagues, and even posted on Facebook and Twitter. The actors claim that they have activated the webcam as well, combining the two recording feeds into a single video. Unfortunately, as it looks from one of the BitCoin wallet addresses used by the actors, they are already enjoying success with their sextortion methods. Of course, no matter what material these actors prove that they have, you are advised not to pay them any ransom. Simply put, they will be able to extort you repeatedly using the same material, as they are not exactly the most ethical and trustworthy people you can find online.
Have you received an email containing the Varenyky malware? Share the details with us in the comments down below, and help the warning reach more people by sharing it through our socials, on Facebook and Twitter.