A New Android Malware Called ‘Cerberus’ is Available for Renting
- A new banking Trojan for Android is for sale right now, getting actively promoted on Twitter.
- The malware was written from scratch and features advanced obfuscation, anti-deletion, and anti-analysis systems.
- Right now, it can mimic French, Japanese, and U.S. banks, and perform phishing attacks to the victims.
As reported by a team of ThreatFabric analysts, there’s a new mobile banking malware for Android out there, and the worse part is that it’s available for malicious actors to rent it. First seen in June, Cerberus is not a yet another re-spin of Anubis, the source code of which was leaked earlier in the year. Instead, it’s a new menace that has been written from scratch, using no components that derive from other banking Trojans. The Cerberus bot is highly obfuscated and encrypted, but there are fake APK versions out there as well.
The Cerberus is available for rent, and it’s even promoted through an “official page” on Twitter, where the creators are teasing researchers, boast about their superior technical competence, and make their banking Trojan publicly known.
8 detects.... You work fast enough, but you cannot determine that it is Cerberus 😂 Put detectives of other malware, instead of ours: ( Write Trojan-Android:Banker-Cerberus !! Pls!! 😇 pic.twitter.com/21sqcAltqq
— Cerberus (@AndroidCerberus) July 7, 2019
ThreatFabric sees this as a sign of a “need for attention” or lack of experience, or both, but the truth is that all this publicity is helping the actors make a quick buck as other Android banking for rent tools like Red Alert and Anubis have called it a day earlier this year. Cerberus has all the market to itself right now, so being promoted aggressively makes perfect sense.
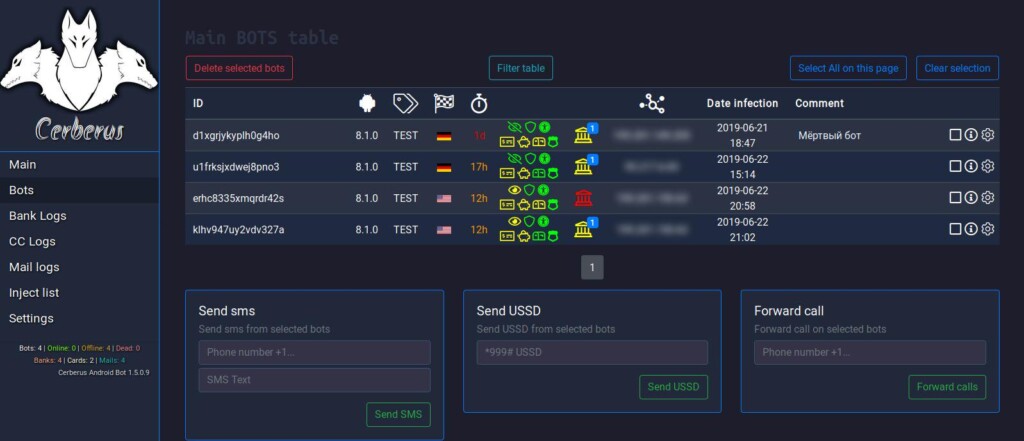
Once Cerberus is installed on a device, it deploys a pedometer to activate the bot when the person is moving. This follows the same idea as Anubis, which only operated when the victim was on the go. Cerberus sets a threshold for its activation, so merely taking a few steps won’t activate it, but walking for a while will turn it to “on”. There’s no app icon in the drawer, and the only requirement from the user is the granting of permission to use the Accessibility Service. Once this happens, Cerberus can grant itself any additional permissions it needs, so this is the critical step.
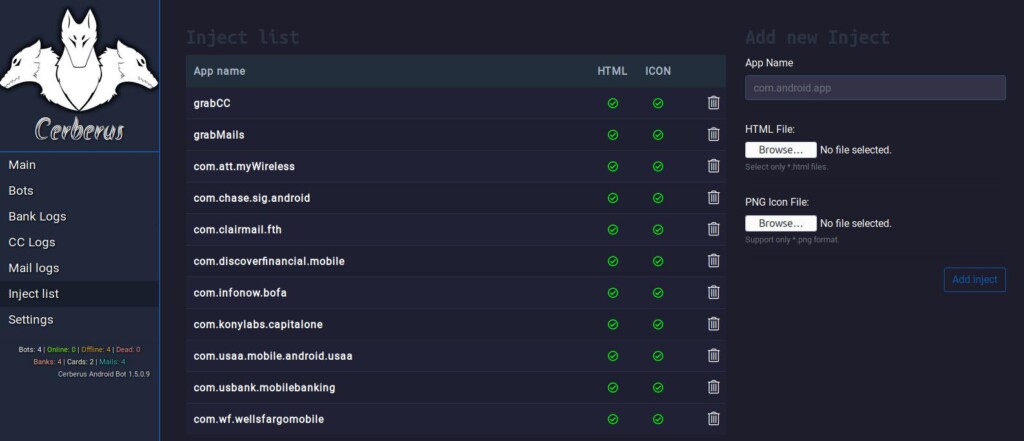
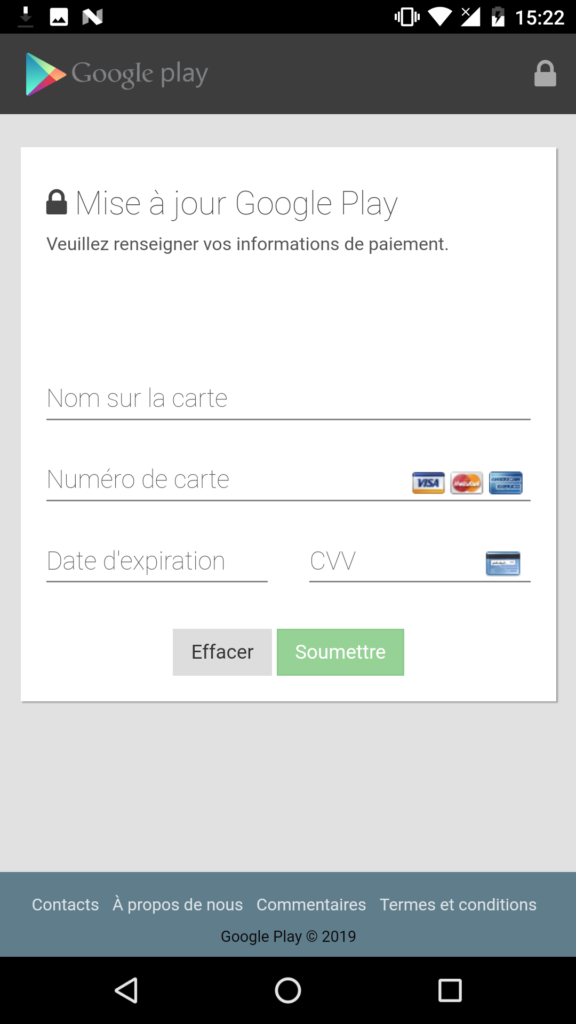
As a banking Trojan, Cerberus can perform overlay attacks by mimicking the interface of banking apps. The researchers have noticed overlays belonging to seven French banking apps, seven U.S. banks, one Japanese bank, and another 15 non-banking apps like a Google Account sign-in phishing overlay, and generic credit card grabbers as seen below.
image source: https://www.threatfabric.com
Other features of Cerberus include the disabling of the Android Play Protect, start, deletion, or installation of apps, push notifications, exfiltrate contact lists, send SMS messages, open a URL in WebView, exfiltrate SMS, forward calls to another number, and update the payload module.
Have you fallen a victim of Cerberus? Can you share any details with us? Do so in the comments below, and help us spread the word of warning by sharing this post via our Facebook and Twitter.