Researcher Demonstrates How to Exploit a 20-Year-Old Windows Vulnerability
- A Google researcher has disclosed a 20-year-old bug that plagues all Windows versions since XP.
- The researcher demonstrated that it’s possible to gain system privileges and bypass UIPI.
- Microsoft ignored his report for 90 days, but they will have to update their CTF system urgently now.
A Google Project Zero security researcher named Tavis Ormandy has discovered a high-severity vulnerability that has been with us for the past 20 years, and thus affects all versions of Windows from the XP to the latest 10. The researcher has informed Microsoft of the particular flaw back in May, but with 90 days have passed since then and no action having been taken to plug it, Ormandy is now disclosing it along with all the juicy details and the proof of concept. He is even sharing the custom open-source tool that he used in order to discover this flaw.
image source: https://bugs.chromium.org
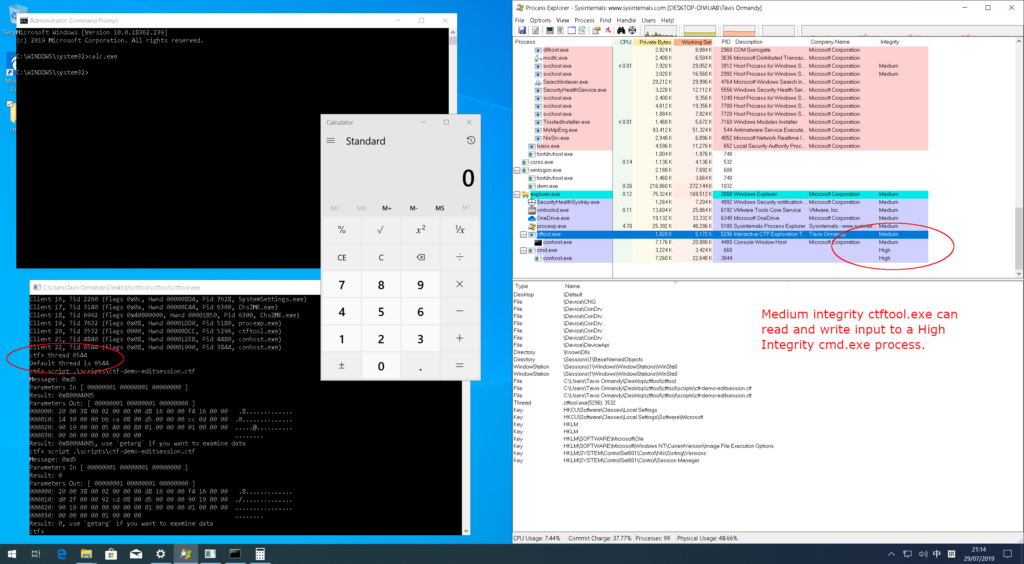
The vulnerability resides in the method of communication between MSCTF clients and servers, allowing the reading and writing of data to applications and users of all privilege levels, including the lowest possible. The researcher has demonstrated that it’s possible to probe the CTF subsystem, read and write data from other sessions that are running on the system, connect to another user’s active session, take over applications, modify the process IDs, create a fake CTF service and trick apps to connect to it, steal the admin login credentials, and finally to escape from sandboxed environments and escalate privileges.
All of this is possible thanks to the fact that there’s no access control for the CTF subsystem. The researcher has developed a tool called “CTF Exploration Tool”, and which offers a command-line interface to access the CTF system, perform debugging, interact with CTF clients and servers, and perform simple fuzzing. For anyone interested, it’s available on GitHub with its commands list and instructions on how to use it for exploitation.
The CTF client is automatically loaded upon the launching of any UI application in Windows, while the TSF system that is its parent is loaded during startup by default. As Ormandy points out, CTF is vast, complex, and completely outdated, having received no real overhauling since 2001. Now, with the exploit being public and the tool to do it available for free, Microsoft has put themselves in the difficult position of having to modernize CTF quickly, following a questionable and almost inexplicable decision to ignore Ormandy’s report.
Have something to comment on the story above? Share your thoughts with us in the section beneath, or join the discussion on our socials, on Facebook and Twitter.