‘TA505’ Hacker Group Deploys a New Downloader Malware Called ‘AndroMut’
- A hacker group known as 'TA505' is using a brand-new downloader malware for their summer campaign, called 'AndroMut.'
- For now, the only payload that is downloaded by AndroMut is the good old FlawedAmmyy RAT.
- The group of actors is currently targeting commercial financial institutions across four countries.
Proofpoint researchers who have been following the TA505 threat actors group spotted a new downloader malware that has just been deployed by the hackers, called “AndroMut”. This new tool features several similarities with the Andromeda malware that was used in the past by the same actor. The main payload that is downloaded by AndroMut is one that’s called “FlawedAmmyy”, a powerful remote access trojan (RAT) that has been under active deployment for more than three years now. The targets of TA505’s summer campaign are mainly commercial banking organizations based in the United Arab Emirates, Singapore, South Korea, and the United States.
In almost all cases, the infection begins with an email that carries a malicious HTM or HTML attachment. The Microsoft Word or Excel file contains macros that execute a Msiexec command upon their opening, downloading and launching either the FlawedAmmyy or the AndroMut malware. If AndroMut is downloaded as the first step, FlawedAmmyy follows as the second. In the English version of the campaign, the sender of the malicious message is given the name “Mir Imran Medhi”, “Ong Kai Chin”, or “Rejeesh Aj”, and the subject and attachments of the mail are related to invoices or holding cheques.
image source: proofpoint.com
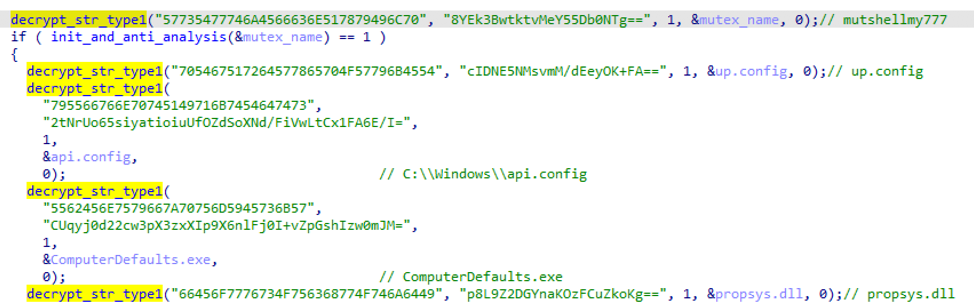
The AndroMut malware was written in C++, and Proofpoint researchers believe it was developed in June 2019. The malware resolves Windows API calls at the runtime level, which is preferable for avoiding detection. The 32-bit hex strings that are used by AndroMut are decrypted with AES-256 in ECB, further adding to the anti-analysis features of the tool. AndroMut is also capable of detecting a sandbox environment, check for debuggers, zeroes memory after using important data, and even checks if it runs on Linux or Mac through the Wine software.
image source: proofpoint.com
The persistence of AndroMut will be another inexhaustible source of headache for the victims. The malicious software creates scheduled tasks that execute an LNK file that has been automatically generated and added in the Recycle Bin, or by following the “Registry run” method.
To stay safe from the AndroMut and TA505, disable macros on your Microsoft Office suite, don’t download and open documents from senders that you don’t recognize, and don’t even trust documents that are sent by familiar persons if you weren’t expecting something from them. Finally, use an up-to-date AV tool from a reputable vendor, and apply OS patches as soon as they become available.
Have you received a message from the senders we mentioned above? Can you share something with us? Feel free to leave your comments down below, or help us raise awareness by sharing this post through our socials, on Facebook and Twitter.