Riltok Android Malware Breaks Out of Russia and Hits the World
- Riltok is targeting Android devices from all around the globe now, as it was translated in English.
- People receive SMS messages of payment notice and are urged to enter banking credentials on a phishing site.
- The malware is getting distributed to more victims through the compromised devices and their contact lists.
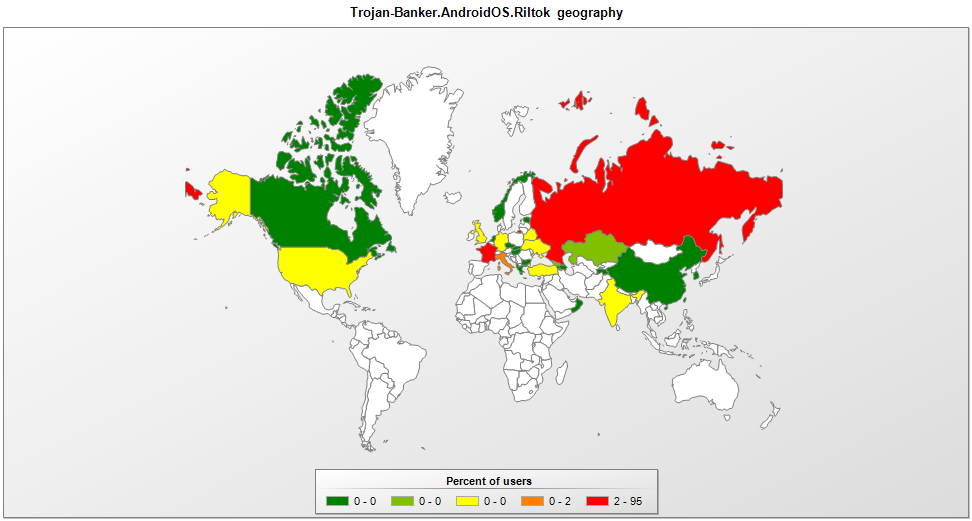
The Riltok banking trojan that was previously confined in Russia has now gone global after its creators “added English language support”. The new Riltok variants are spotted in France, the U.K, Ukraine, Italy, India, Turkey, and the USA, but Russia remains the country that holds the lion’s share of the infections. The malware reaches the devices of its victims through an SMS, with the message containing a link to a website. Depending on the region, different versions of the tricking website are used, impersonating local services or pretending to offer an update to one of your applications.
image source: securelist.com
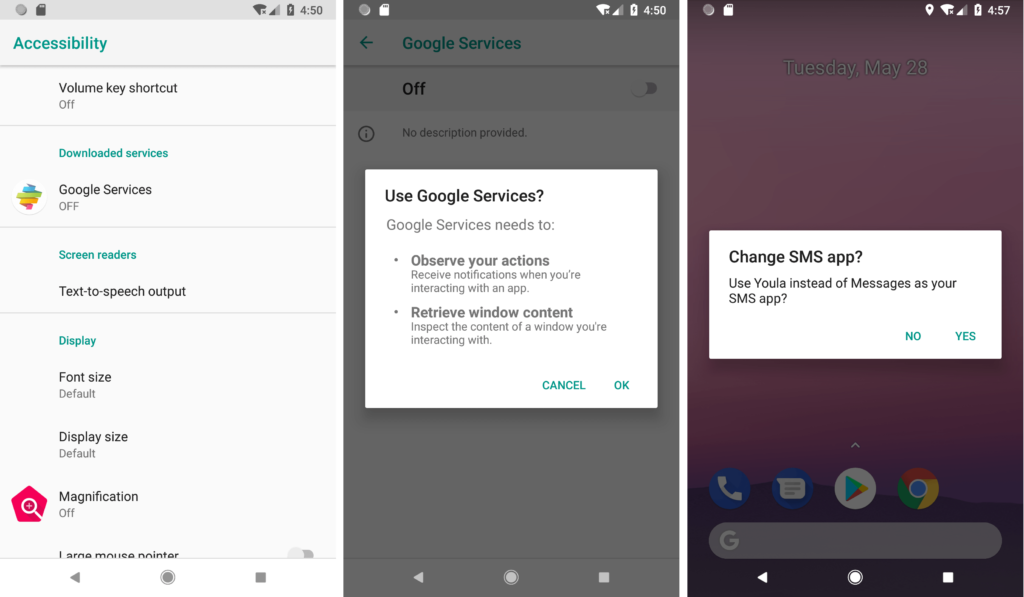
The SMS messages come from contacts that the potential victim's trust, as the distribution occurs through compromised devices. The texts are sent to the whole contact list, and the message has the sender claiming that a payment that was made to the recipient. If the victim chooses to tap on the link and downloads the malware, the next step will be to grant the requested permissions. First, for the installation of the Riltok malware, the user will have to enable “unknown sources”, as this APK is not coming from the Play Store obviously.
image source: securelist.com
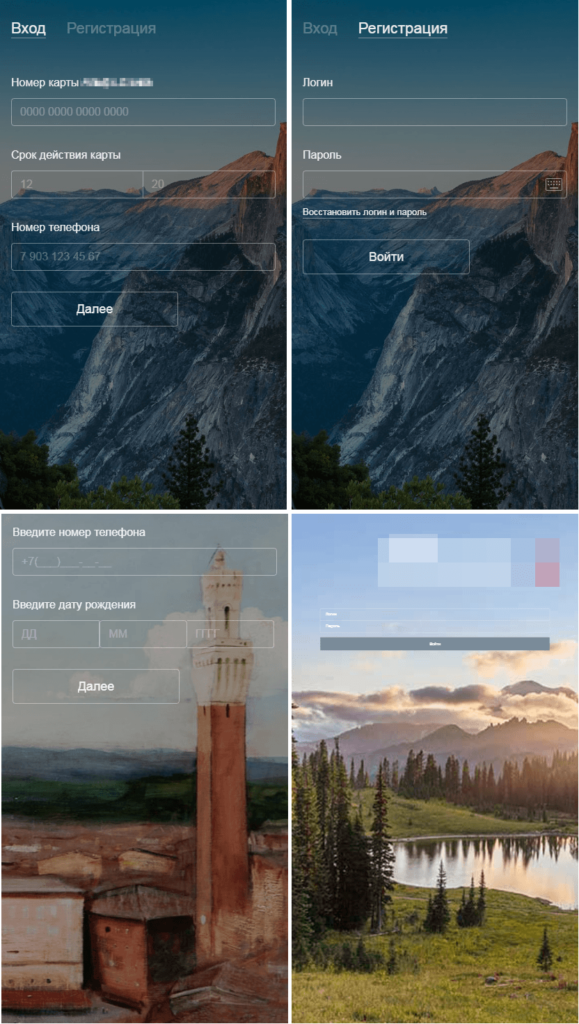
Another permission that Riltok asks for is to change the default messaging app with itself so that your device can be rendered into a malicious propagator as described above. Once the banker is all set up on your device, it launches a browser and takes the victim to a fake login page that impersonates a local banking service. Any credentials added there are sent directly to the C2 server. Other information that is gathered transferred to the C2 includes the device’s IMEI, the phone number, country, mobile carrier, device model, root status, Android version, installed apps list, and the contacts list.
image source: securelist.com
The fake apps that are used as pretend by Riltok are called “Avito”, Youla”, Gumtree”, Leboncoin”, and “Subito”, but of course, more names and icons can be added by the actors at any time. This means that you should be very careful with SMS messages that contain links, and never trust on clicking them. Even if these messages come from one of your contacts, it doesn’t mean that they are sent by that person. For increased security, keep your phone’s software and apps up to date, use an anti-virus tool from a trusty vendor, and never grant permissions requests from apps that shouldn’t need them to work.
image source: securelist.com
Share your views in the comments down below, or hop to our socials and join the discussions of our online community on Facebook and Twitter.