Android Devices Fall Victims of Cyber-Espionage Actors Across the Middle East
- A new cyber-espionage campaign is taking place in the Middle East, while also getting heavily promoted on social media.
- The malware that is spread can steal all types of files and information from the infected devices.
- Researchers notice similarities with another tool used by an Iranian cyberespionage group.
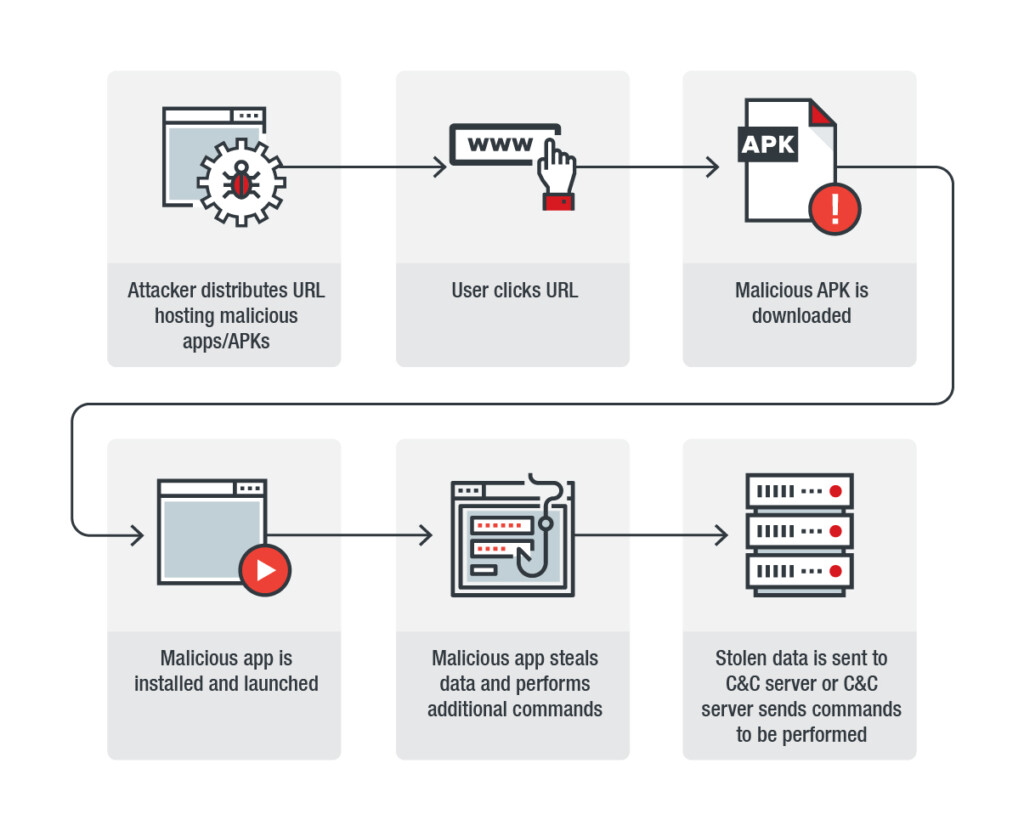
According to a Trend Micro report, there’s an ongoing cyber-espionage campaign that targets Android devices in Middle Eastern countries. The particular campaign is called “Bouncing Golf” due to the names of its packages and has already infected at least 660 devices. The actors are not randomly targeting individuals, but users who hold or have access to sensitive military information. This implies that the group behind this campaign could be state-sponsored, but no definitive conclusions about that are drawn by the Trend Micro researchers.
Image source: blog.trendmicro.com
The malware that can infect the targeted Android devices is given the name “GolfSpy” and is capable of stealing the following information:
- Device accounts;
- List of applications installed in the device;
- The device’s currently running processes;
- Battery status;
- Bookmarks/Histories of the device’s default browser;
- Call logs and records;
- Clipboard contents;
- Contacts, including those in vCard format;
- Mobile operator information;
- Files stored on SDcard;
- Device location;
- List of image, audio, and video files stored on the device;
- Storage and memory information;
- Connection information;
- Sensor information;
- SMS messages;
- Pictures.
Besides stealing information, GolfSpy is also capable of downloading and installing additional APKs onto the infected device, connect to a remote server, and execute additional commands, take screenshots, record audio, record video, and update itself.
The propagation of the GolfSpy malware is done via social media posts that point users to a website that hosts apps that are repackaged to include malicious tools. That said, the APKs that carry the particular malware are not to be found in the Google Play Store or any other of the popular APK download portals. Again, this is an example of why people should never trust sources outside Google’s official app store, which has some level of app code reviewing and approval.
Image source: blog.trendmicro.com
While Trend Micro couldn’t unmask the C&C domain registrant information, and with the IP addresses not offering any type of useful data, they believe that the actors behind the Bouncing Golf campaign are the same that spread Domestic Kitten between 2016 and 2018. That cyberespionage operation appeared to originate from Iran, and Check Point Research pointed to Iranian government entities. Trend Micro researchers base their assumption on the connection on the similarity of the structure of the strings of code as well as the format of the theft operation. For example, the Domestic Kitten and the GolfSpy use the same decoding algorithm for C&C communications. This could also be a case of code sharing between related groups, or even monitor-based reverse engineering, but that’s unlikely.
Share your views with us and our community in the comments down below, and don’t forget to also check our socials on Facebook and Twitter, for more news and tech stories.