GoldBrute Botnet Spreading Like Wildfire Over 1.6 Million RDP Servers
- A new botnet reaches RDP pandemic proportions, as it is already knocking on the door of 1.6 million endpoints.
- The botnet is based on brute forcing action, and it doesn’t try to exploit the “trending” BlueKeep vulnerability.
- Network defense systems fail to detect it because each bot tries one password against the server.
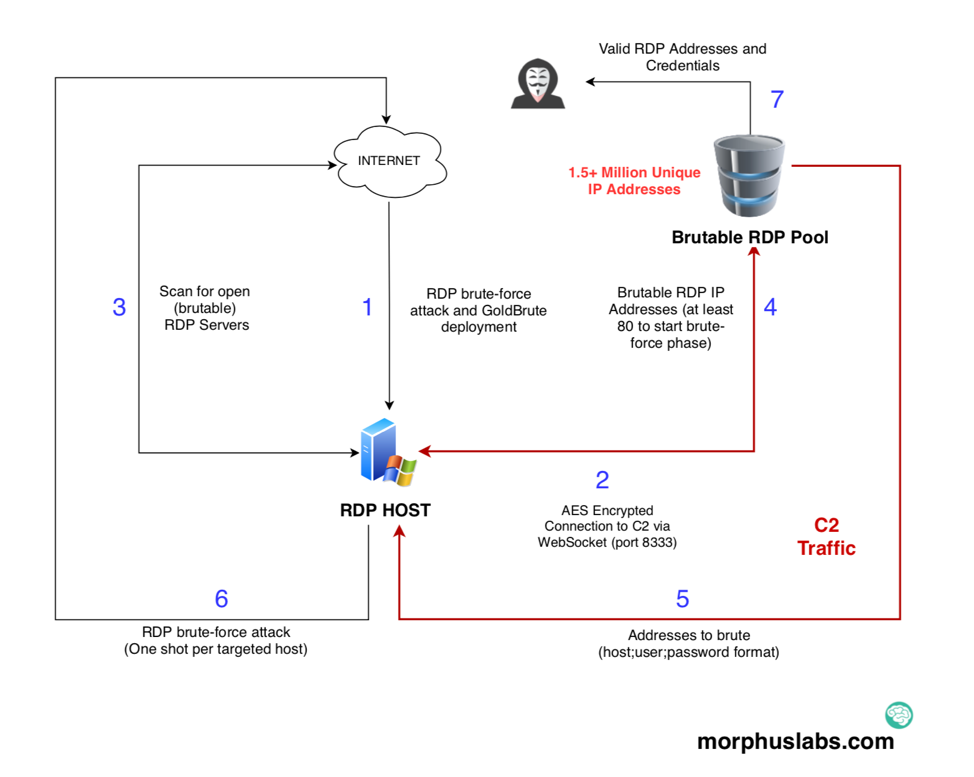
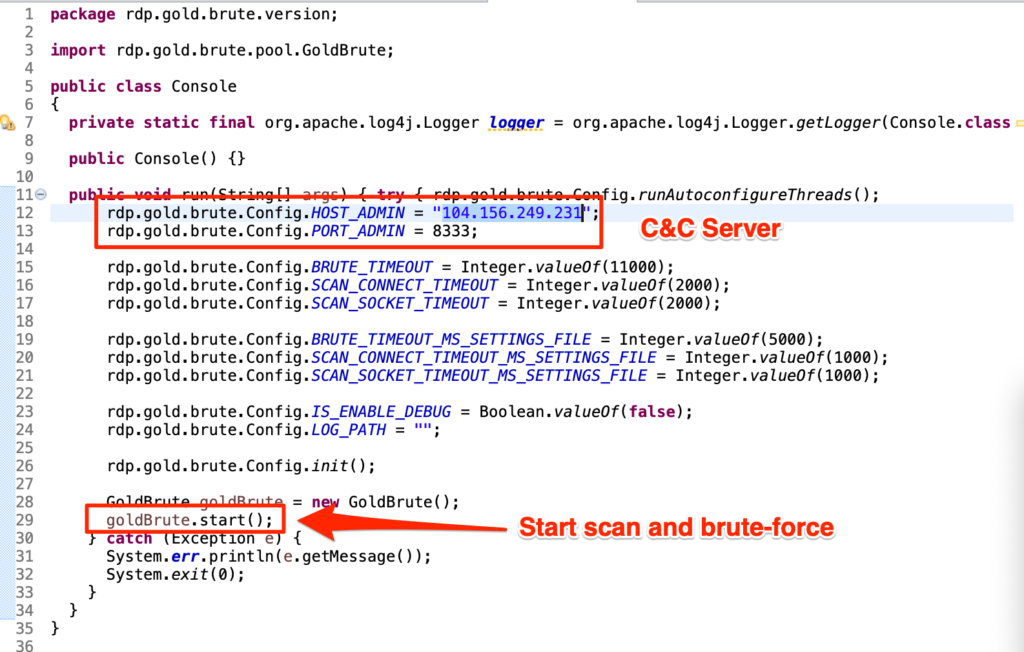
A new botnet called “GoldBrute” is currently at the peak of its activity, searching of RDP (Remote Desktop Protocol) servers and trying to brute force its way in. Right now, the researcher who discovered the worm, Renato Marinho, says the botnet is targeting about 1.6 million RDP endpoints, but as Shodan results indicate the number of exposed RDP servers is at least 2.4 million, so GoldBrute has not unfolded its full potential yet. The researcher noticed a single command and control server, while the communication between the bots and their C2 server is AES-encrypted.
image source: isc.sans.edu
Once a machine is infected, it downloads a relatively large file of 80 MB which includes the Java Runtime code. The bot then scans a wide range of random IP addresses trying to locate more hosts with exposed RDP endpoints. Whatever is found is sent to the C2 server, and then instructions to brute force are sent back accordingly. Each bot tries one username and password combination per target, so as not to trigger any protection and network defense mechanisms reaction. When a bot reaches 80 “brutable” servers, it enters the brute-force phase, trying various “host + username + password” combinations.
image source: isc.sans.edu
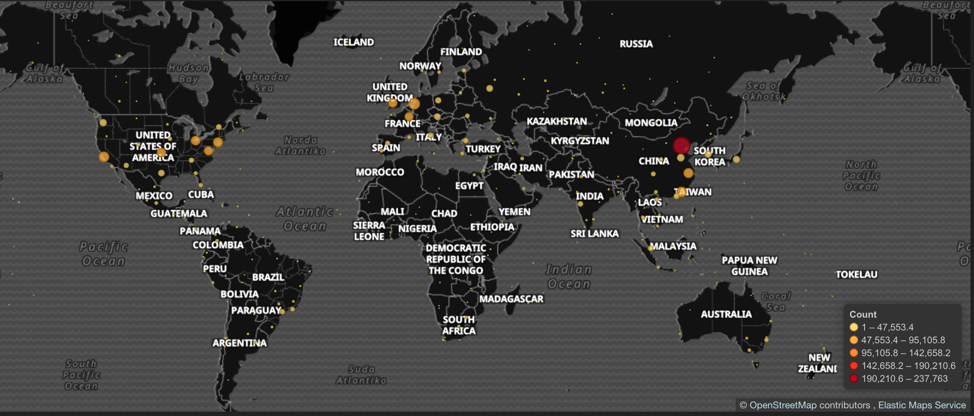
The researcher tried to configure the code of the GoldBrute to make it save all of these login data combinations onto his testing machine, and after six hours of logging, he received 1.6 million unique IP addresses. By geolocating these IP addresses, it became evident that the problem is global, and not contained in a specific area, although GoldBrute is mainly to be found in the USA, Europe, and East Asian countries. Although the infection has reached such an extent, almost no one realized anything thanks to GoldBrute’s method of guessing the password once and not multiple times.
image source: isc.sans.edu
This discovery raises the concern for RDP system safety and reminds experts of the fact that brute-forcing attempts are still the biggest problem faced by exposed servers. In the last month, everyone went frenzy about the disclosed BlueKeep vulnerability that affects RDP systems and can result in a WannaCry-like worm problem. However, RDP threat detections show that more than 96% of the attacks launched throughout last week are brute-force attacks, and only 3.4% of them try to exploit the BlueKeep vulnerability.
Have something to say on the above? Let us know in the comments down below, or on our socials, on Facebook and Twitter.