When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
What is VPN Encryption?
In today's world of growing cybersecurity threats, VPN encryption ciphers play a crucial role in safeguarding your online data. That’s what scrambles your data into unintelligible code, preventing any third party from interpreting it. Furthermore, it’s also practically impossible for third parties to decrypt your VPN-encrypted data.
Encryption has countless benefits for Internet users. For example, if you regularly shop online, you would want to protect your credit card information and other online data from cybercriminals and hackers. Or, you simply don’t like the idea of your Internet provider knowing what you do online. In such scenarios, VPN encryption can come in handy.
But how does VPN encryption work, and which encryption cipher is the best? In this article, we will answer all these questions for you. You will also learn about the types of encryption and the steps to test it using Wireshark. Let’s get started!
What Is VPN Encryption?
VPN encryption is a process that changes the plaintext data into an encrypted code. After that, the data can only be decrypted by the intended party. The goal of encryption is to increase your Internet privacy and prevent third parties from spying on your Web traffic.
Using a capable VPN is a foolproof way of encrypting your Internet traffic and hiding your browsing activities. All this information gets hidden after it passes through the VPN’s server (here’s more info on how a VPN works, by the way).
Generally, good VPNs use the AES-256 cipher for data encryption because it’s one of the best encryption technologies. Hence, it should be the minimum requirement. However, alternative options like the ChaCha20 and Blowfish ciphers are also used, as explained later in the article.
How Does VPN Encryption Work?
VPN encryption works by creating a secure channel that ensures your data remains safe even if it gets intercepted. It generally consists of the following 4 steps:
- Asymmetric Key Exchange: Your VPN client communicates with its server by creating a private and a public key. The public key can encrypt your data, but it won’t be able to decrypt it. This key is sent to the server, which uses it to encrypt your traffic such that it can only be decrypted by you.
- Symmetric Key Exchange: This step creates a new key that will be used by the encryption algorithm. This establishes “perfect forward secrecy,” which means your data will stay secure even if the encryption channel from step 1 gets breached.
- Encryption Algorithms: Algorithms like the AES-256 will use the symmetric key exchange from the previous step and encrypt your data.
- Integrity Algorithms: Their main use is to determine if your data has been tampered with during transit. You first scramble some part of your data using a hash function. The receiving party checks your private key and the hash function to confirm a match. If the match is positive, it means that nobody has changed your data.
Types of Encryption
Generally, based on the encryption key, there are two types of encryption methods. These include asymmetric key encryption and symmetric key encryption.
- Symmetric Key Encryption: Symmetric key encryption involves using a single key for both encrypting and decrypting data. This is comparable to a lock-and-key system where the same key is used for locking (encrypting) and unlocking (decrypting) information. To ensure secure communication, the sender and the receiver must share the key in a secure way beforehand.
- Asymmetric Key Encryption: Asymmetric key encryption involves two keys, i.e., a public key and a private key. The public key can be shared openly, but the private key is never shared. To send a secure message, the sender encrypts the data using the recipient’s public key. The recipient decrypts this message using their secret private key. Because the private keys never get shared, this type of encryption is more secure.
Common VPN Encryption Ciphers
Encryption ciphers are algorithms that scramble and unscramble data to protect your security. One of the most important aspects of encryption is the key length, where longer keys are considered to have stronger encryption. For example, AES-256 is more secure than AES-128 due to its longer key length.
There are multiple VPN encryption ciphers out there. In the following sections, we will explore four popular ciphers - AES, Blowfish, ChaCha20, and Camellia - and their respective features.
Advanced Encryption Standard (AES)
AES is often regarded as the gold standard for encryption protocols. It was developed by Belgian cryptographers Joan Daemen and Vincent Rijmen, and adopted by the US government in 2001 as a replacement for the earlier Data Encryption Standard (DES).
AES is available in key lengths of 128-bit and 256-bit. When you hear about "military-grade encryption," it typically refers to AES-256-bit encryption, which is nearly impossible to break.
Blowfish
Blowfish was designed by Bruce Schneier in 1993 as a fast, free alternative to existing encryption algorithms. It uses key lengths ranging from 32 to 448 bits. However, Blowfish has a weakness: it’s vulnerable to a "birthday attack." This type of attack exploits the fact that the probability of finding two identical elements in a set increases with the size of the set.
Due to this vulnerability, Blowfish is often only used as a second resort, with AES-256 being the preferred encryption cipher.
ChaCha20
ChaCha20, designed by Daniel J. Bernstein in 2008, is a relatively new encryption cipher. It’s the only cipher compatible with the WireGuard protocol, making it popular in the VPN industry. ChaCha20 uses a 256-bit key length and is considered to be about three times faster than AES.
While ChaCha20 is generally considered secure, it hasn't been as extensively tested as other ciphers like AES, so it could potentially reveal vulnerabilities in the future.
Camellia
Camellia is an encryption cipher similar to AES in terms of speed and security. Developed by Japanese researchers, it’s available in key lengths of 128, 192, and 256 bits. Despite its smaller key length, brute force attacks are still considered infeasible against Camellia.
However, Camellia is not NIST-certificated. The National Institute of Standards and Technology (NIST) certification is significant for encryption ciphers as it attests to their security and reliability. Due to the lack of NIST certification and extensive testing, Camellia is rarely available in VPN apps.
How to Check if Your VPN Is Encrypted?
You can test whether your VPN is encrypted using Wireshark (Windows/macOS), which is a free, open-source tool for network analysis and troubleshooting.
Wireshark allows inspection of individual data packets, which means that you can easily verify whether your Web traffic is encrypted or not. Let’s take a look at the steps involved, and keep in mind that we’re using ExpressVPN, our #1-rated VPN.
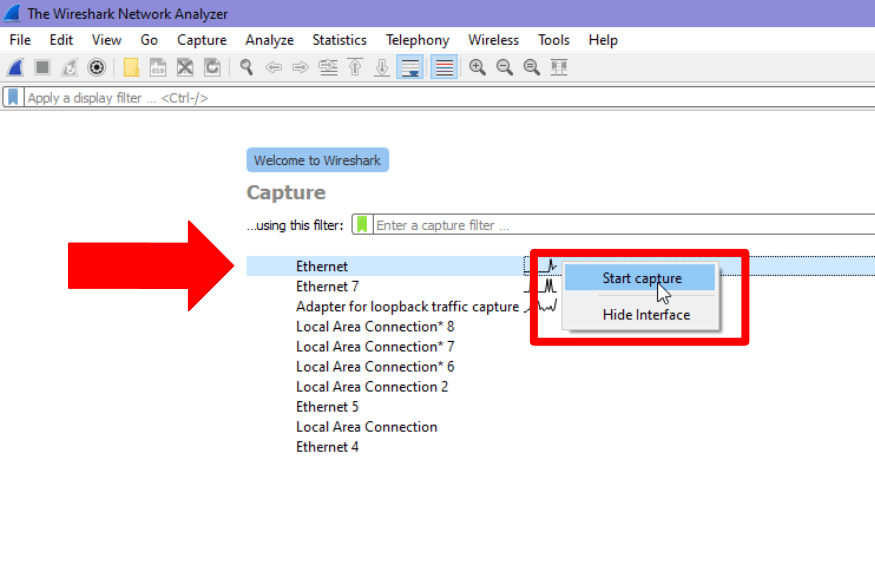
- Download Wireshark from the official website and install the application.
- Run Wireshark and choose a network that you want to test, and click “Start capture.”
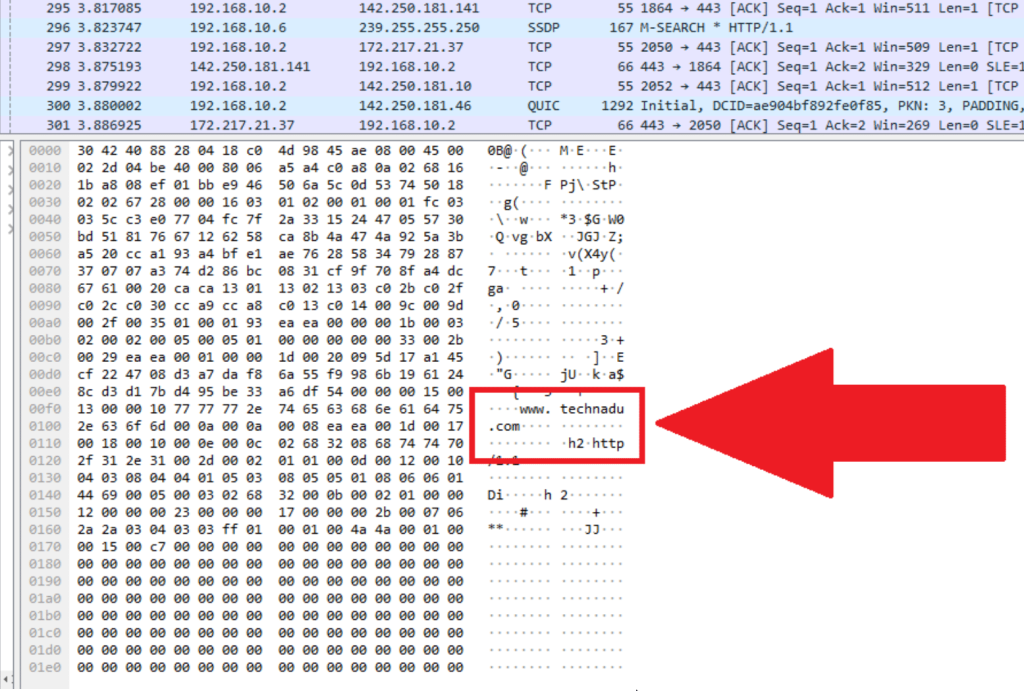
- As shown in our screenshot below, the website names are visible in the contents of the data packets, which means that the data isn’t encrypted.
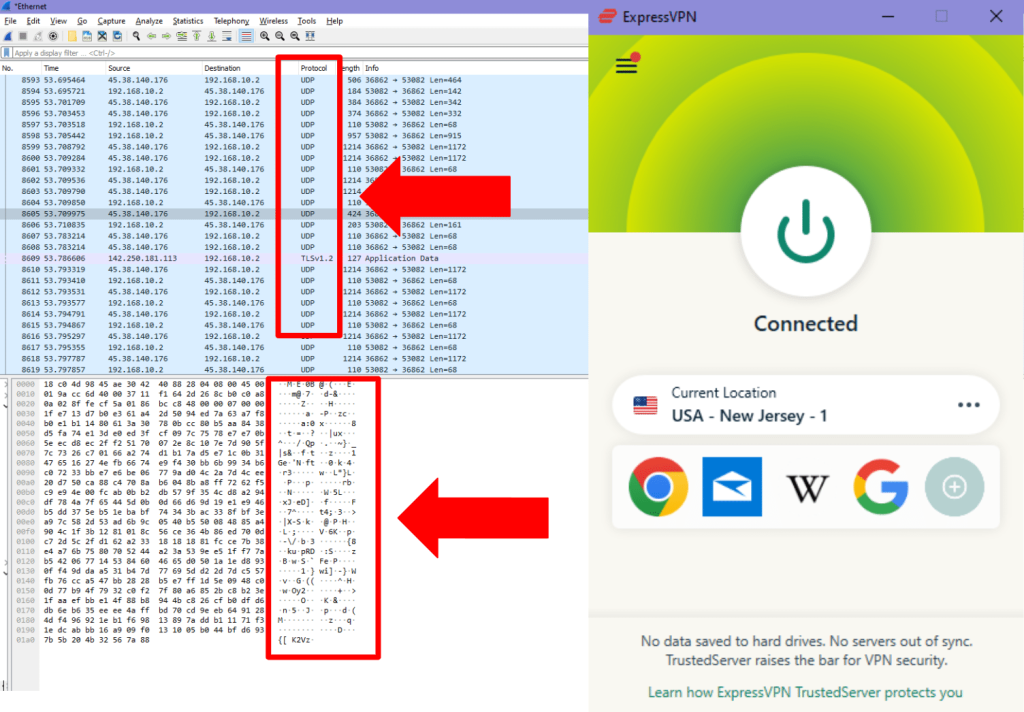
- Now connect to your preferred VPN, and recapture your internet traffic on Wireshark.
- If you can’t see anything written in readable text on the data packets, it means that your information is successfully getting encrypted.
Along with that, you may notice in the screenshots above that the protocol has also changed from TCP to UDP. This happened because our VPN client is set to use OpenVPN UDP.
Difference Between VPN Protocols and VPN Encryption Ciphers
VPN protocols are a set of rules and processes that a device follows to establish a connection with a VPN server. These protocols are responsible for forming the VPN tunnel, which secures the data that flows between your device and the VPN server.
On the other hand, encryption ciphers are the algorithms used to encrypt the data that flows through the VPN tunnel, ensuring that your information remains safe and unreadable even if intercepted.
Now, let's briefly explore some of the most popular VPN protocols:
- OpenVPN: A widely-used, open-source VPN protocol that balances security, speed, and compatibility across various platforms.
- WireGuard: It’s a newer VPN protocol designed for high performance. WireGuard provides excellent security and speed while being lightweight.
- IKEv2/IPsec: This protocol is particularly suitable for mobile devices, as it’s very stable when switching between two networks or if you briefly lose your connection.
- SoftEther: An open-source VPN protocol that offers high-speed connections and strong encryption, making it an excellent choice for bypassing geo-restrictions and censorship.
- L2TP/IPSec: While this protocol has potentially slower speeds, it’s widely supported and provides high security by combining L2TP with IPSec encryption.
- SSTP: A Windows-based protocol that provides a high level of security by using SSTP over an SSL/TLS connection, making it difficult to block.
- PPTP: An older but faster VPN protocol considered to be less secure due to known vulnerabilities. It’s not recommended for use if privacy and security are your top priority.
For more information, consider reading our complete guide on VPN protocols.
Are VPN Encryption Ciphers Unbreakable?
Yes, VPN encryption ciphers are practically unbreakable. That is because the length of the keys used to encrypt and decrypt data are quite lengthy, which is what makes VPN encryption so secure.
For example, 256-bit keys are considered the gold-standard encryption for securing credit card transactions and other sensitive information on the Internet.
Since each bit can only have two states (1 or 0), the number of possible combinations for a 256-bit key is 2 to the power of 256. That is a properly, massively, stupendously huge number.
Even if you took the most powerful computers in the entire world, like the ones governments have, and you let it guess millions of possible key combinations every second of every day, it would still take billions of years for that computer to try every possible combination of bits that make up the key.
So while it’s not technically impossible to use brute force to 'crack' strong encryption, it’s so impractical that you can consider it unbreakable.
Based on this, here's the answer to the question of whether VPNs can be hacked - no, they are safe as long as their encryption is strong.
Final Thoughts
VPN encryption ciphers are essentially algorithms that scramble and descramble your data to protect it from prying eyes. Protocols, on the other hand, are responsible for forming the VPN tunnel based on a particular set of rules.
When we talk about encryption, AES-256 is considered to be the gold standard because it’s practically unbreakable. That is why all capable and security-focused VPNs use this encryption.
If you are looking for military-grade encryption, we recommend ExpressVPN because it uses AES-256-bit encryption. This VPN also has other security and privacy features, such as obfuscated servers and an anti-tracking system, ensuring total privacy on the Web.
We hope that this article has answered all your questions about VPN encryption. If you have a question or additional information to share, feel free to add it in the comments section below. Thank you for reading!