Researchers Discover Data Leaking From 25000 Linksys Wi-Fi Routers
- A wide range of Linksys Wi-Fi routers is leaking sensitive information that can lead to serious problems.
- Most of the routers are in the US, but the problem is global as there are hundreds of ISPs using the vulnerable models.
- Linksys denies the existence of any problems and isn’t planning a fix to be rolled out soon.
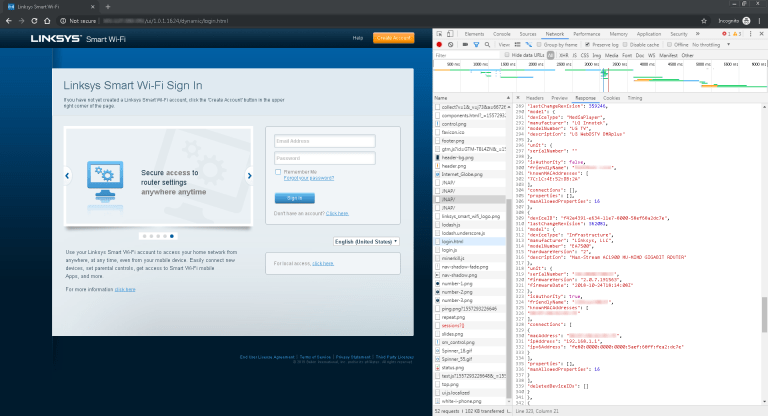
Bad Packets Report researchers have discovered that over 25000 Linksys Smart Wi-Fi routers are leaking sensitive information such as the device name, the model number, the MAC address, and the operating system. In some cases, the leaking data includes firmware update settings, DDNS settings, WAN settings, and firewall status. According to the researchers, the vulnerability can be exploited remotely, and there’s no requirement for any type of authentication for the attacker.
image source: badpackets.net
The researchers demonstrate how easy it is to exploit the vulnerability by sending a request to the following JNAP endpoint: “X-JNAP-ACTION: http://cisco.com/jnap/devicelist/GetDevices”. Alternatively, you may visit your router’s public IP in the web browser, open the developer console, hop to the Network tab, and click to the JNAP to open it.
The number of Linksys Wi-Fi routers that are currently leaking the data described above was found to be 25617, and include the following models:
- Linksys E1200
- Linksys Max-Stream AC1900, AC4000, AC5000, AC5400
- Linksys AC3200 Tri-Band Smart Wi-Fi
- Linksys Simultaneous Dual-Band Wireless-AC and Wireless-N
- Linksys Velop
- Linksys Max-Stream AC1900 and AC2600
The geographical dispersion of the vulnerable devices has the United States in the first place with 11834 routers, Chile second with 4942, Singapore third with 2068, and Canada fourth with 1215. Of course, there are vulnerable Linksys routers across the whole world (146 countries), as this is not just an isolated batch.
If you are among the vulnerable system owners, beware that leaking your MAC address means that the geolocation of the router is entirely possible. Moreover, this information opens the door to escalated attacks, especially for routers that still use the default “admin” password. This could possibly lead to router takeover, and from there on anything is possible. DNS hijacking, Wi-Fi password exfiltration, fiddling with the open ports, setting UPnP traffic redirection, routing malicious traffic through it, or even brick the device.
Now, the weird element in this whole story is that Linksys isn’t identifying anything wrong with what the Bad Packets researchers have reported to them, so they are not planning to fix anything. The vulnerability remains present even for the routers that are using the latest firmware version, and no one knows when the flaw will be plugged. If a patch is released, more than half of the vulnerable routers will receive the updates immediately as they have enabled the auto-updates option.
How are you ensuring the security of your router? Share your comments with the community in the section down below, and help us spread the word of warning by sharing this post through our socials, on Facebook and Twitter.