HawkEye Reborn Malware Kit Hits Organizations Hard
- There’s a surge in the use of automated information exfiltration kits like HawkEye lately.
- The tools are harder to detect, analyze, and stop, as they have been developed with care for years now.
- The HawkEye keylogger/stealer is now capable of exfiltrating account credentials from a rich set of applications.
The Cisco Talos research team has been following the “HawkEye Reborn” malware kit in these past months, and now warns of a rise in its deployment against organizations from around the globe. Malicious kits like the HawkEye make it possible for even those who have little programming or computer knowledge to carry out attacks against anyone, stealing account credentials, sensitive information, or compromising corporate networks. While HawkEye is not the only tool of this kind for sale out there right now, it’s definitely one of the most successful, and the rise in its deployment reflects this with clarity.
HawkEye is one of the oldest kits, with its first appearance in dark web marketplaces going back in 2013. Since then, the kit has gone a long way through continuous development and the implementation of additional features, with the stealing of sensitive information from a wide range of applications remaining its spearhead. The most recent version, HawkEye Reborn v9, was first spotted in December 2018, and since then, there has been a widespread deployment and sale across multiple crook websites. Marketed as an “Advance Monitoring Solution”, it is sold for $27/90 days, $37/180 days, or $47/year.
image source: blog.talosintelligence.com
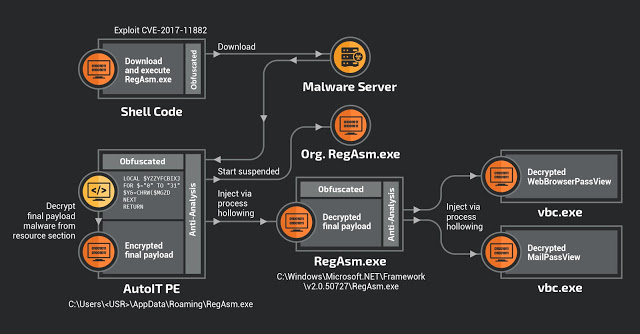
The Talos team has detected multiple email distribution campaigns that spread the HawkEye Reborn keylogger/stealer and leveraged the chance to analyze the latest samples. What the team has found is that the newest versions add heavy obfuscation and AV binaries detection. The stealer is usually accompanied by financial documents such as invoices or order confirmations that concern the recipient organization. The actors have even used Dropbox-hosted folders to store malicious documents that can exploit the CVE-2017-11882 MS Office vulnerability. The chain of events includes an arbitrary code execution pointed to a buffer overflow flaw, leading to shellcode execution and the downloading of the HawkEye binary.
image source: blog.talosintelligence.com
In version 9, the stealer can grab passwords from all major web browsers, Filezilla, Beyluxe Messenger, CoreFTP, and even the Minecraft video game. The methods include the employment of a keylogger process, clipboard content parsing, and even taking screenshots of the desktop or snapping pictures from the webcam. Whatever information is gathered by HawkEye is compressed in a temporary file and then sent via FTP, SFTP, HTTP POST, or email, as per the actor’s preference. All of this is indicative of the level of automation and exfiltration comfort that modern credential thieves enjoy, and this is only about to get worse for organizations in the following months, as tools and malware kits evolve further.
Have any comments to share on the above? Feel free to drop them down below, and don’t forget to check what else is on today through our socials, on Facebook and Twitter.