Legacy IMAP Cloud Email Accounts Under Massive Takeover Attack
- Many thousands of cloud email account takeover attempts were detected in the past couple of months.
- Most of the targeted accounts use the IMAP protocol, resulting in high success rates for the actors.
- The attacks originated from African regions, something that is consistent with several recent arrests there.
Proofpoint researchers have published a detailed report, according to which the number of attacks against Office 365 and G Suite cloud accounts has risen alarmingly. While the targeted accounts are protected with multi-factor authentication, the weak link of using the now obsolete IMAP protocol allows the hackers to brute-force their way in. According to the numbers that are given in the report, out of the 100,000 cloud email accounts that were monitored in the recent six months, 150 were successfully breached, 2% of the active user accounts were targeted, and 72% of the tenants were targeted by threat actors at least once.
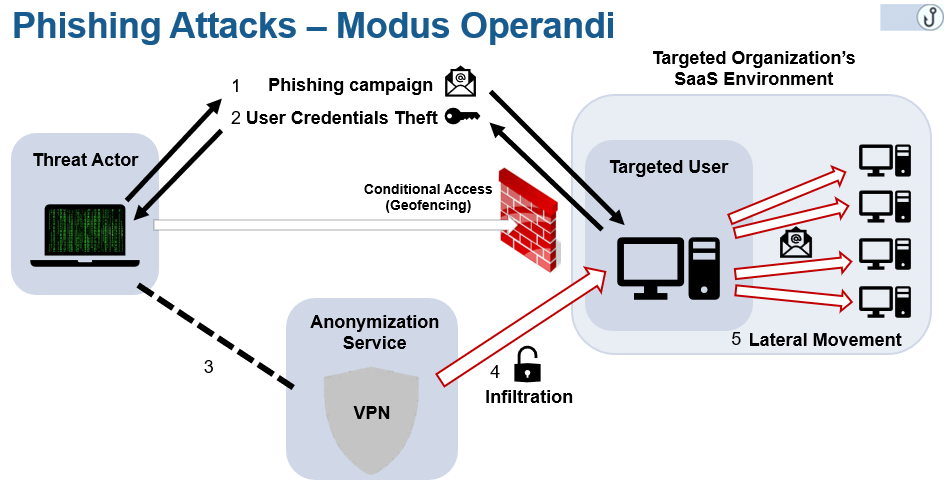
The actors are using credential data dumps combined with intelligent brute force cracking to infiltrate a network. From there, they evaluate the importance of their first victim and decide whether an internal phishing attack should be conducted inside the compromised corporate network. These internal phishing attempts which are also known as “lateral movement”, are more tricky and far more convincing for the employees of a company, since they don’t originate from an external point and thus create a false sense of trust for the receiving end. According to Proofpoint, about 31% of the successful attacks that were detected, originate from stolen credentials that were the direct result of internal phishing.
Source: proofpoint.com
The main type of organizations that were targeted during these past six months is educational institutes (15%), followed by industries such as retail, finance, and technology. Schools and universities are easier to compromise compared to corporate networks, as rerouting employee paychecks and accessing crucial financial documents were the main activities of the malicious actors. Because of this, the people who are targeted the most are those who work in the sales departments, executives, and managers.
Source: proofpoint.com
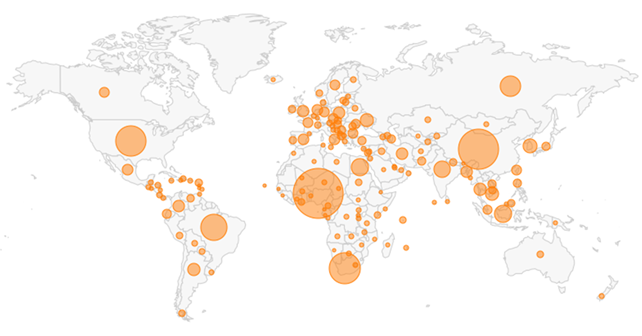
With all that said, the only thing that remains to be clarified is the “who”, but as it’s always the case with these stories, the actors behind these attacks stay well hidden. Proofpoint points to Nigeria, with 63% of the attacking IP addresses coming from there, and South Africa following with 21%. VPNs were also used by the actors, so there’s another 11% that passed through virtual networks in the US. To launch the attacks, the hackers utilized a vast network of compromised servers and routers, so whether the actual location of the actors is somewhere in Africa or not remains a conundrum.
Have you ever had the adverse experience of losing access to your cloud email account, or sharing it with a hacker? Share the details with us in the comments section below, and don’t hesitate to visit our socials, on Facebook and Twitter.