Adware infects 206 Android Apps Downloaded 150 Million Times
- Multiple Android app developers were tricked into using a malicious ad-serving SDK.
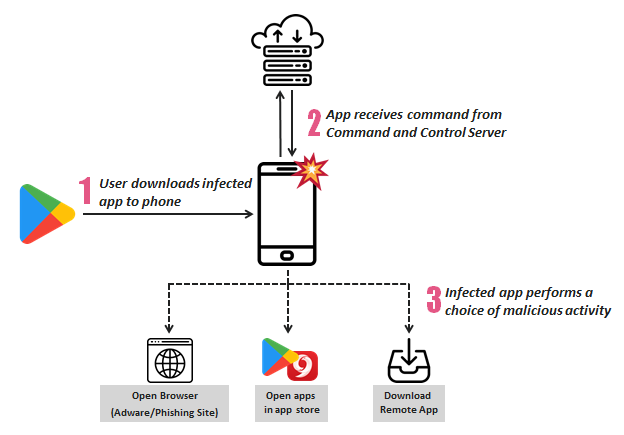
- The malware communicates with a C2 server and gets commands on what action to follow.
- The possible actions include opening a browser ad, visiting the play store, or downloading an app.
The “Mobile Threat Team” of Check Point research has made a colossal adware campaign discovery that affects about 150 million installations. Because the majority of the apps that deliver the adware to the users’ devices are “simulation games”, the researchers have named the campaign “SimBad”. While Google has removed all of those apps from the Play Store, there must be millions of devices that still hold the adware apps in their storage, so if you’re a sim-game lover, you should check your apps and uninstall those that are malware-ridden.
For a full list of the infected applications, you may check the detailed Check Point report, but we’ll provide you a short list with those that have over 5 million installations each.
- Snow Heavy Excavator Simulator
- Hoverboard Racing
- Real Tractor Farming Simulator
- Ambulance Rescue Driving
- Heavy Mountain Bus Simulator 2018
- Fire Truck Emergency Driver
- Farming Tractor Real Harvest Simulator
- Car Parking Challenge
- Speed Boat Jet Ski Racing
- Water Surfing Car Stunt
- Offroad Wood Transport Truck Driver 2018
- Volumen booster & Equalizer
- Prado Parking Adventure
- Oil Tanker Transport Truck Driver
The above, and all of the rest of the infected apps are not made by the same developer, so their adware infection is not a consciously malicious act from their side. Most probably, they have been deceived into using a malicious ad-serving SDK called “RXDroider”, which connects to a command and control server and initiates its vile activity which is divided into three distinct groups.
The first possible action of the malware is to open an ad-serving browser page or even a phishing page that can draw user credentials if the latter falls victim to it. The second action could be the opening of the Play Store, or other app stores such as “9Apps”, and download more Android applications on the infected device, increasing the revenue for the actors. The third option is to straight-forwardly download and instal an Android app from a designated server, essentially allowing the attacker to push anything to the infected device.
source: research.checkpoint.com
The C&C server is “addroider.com”, which is registered with GoDaddy and sits behind a privacy protection service layer. That said, the actors cannot be identified and considering that the particular domain expired seven months ago, it may have gone rogue at a second phase. Check Point researchers warn that while the SimBad campaign had purely adware characteristics, there’s really nothing stopping them from going full-fledged phishing and malware. As Google has now removed this batch, people who may still have one or more apps that are infected by RXDroider are urged to remove them immediately.
Have you been using one of the infected apps lately? Did you notice any kind of unexpected ad-serving action on your device? Let us know of your experience in the comments section below, and don’t forget that you have the power to help us spread the word and warn others, by sharing this post through our socials, on Facebook and Twitter.