Researchers Disclose Thunderbolt Vulnerabilities Affecting All Operating Systems
- Researchers found that specially crafted Thunderbolt devices can gain unrestricted malicious access to a system’s memory.
- The problem was first disclosed back in 2016, but OS developers have failed to address it properly until now.
- People are advised not to use unreliable Thunderbolt, or to disable the interface altogether through BIOS/UEFI settings.
Three years after the initial discovery, researchers from the University of Cambridge and SRI International have presented a set of vulnerabilities that concern the Thunderbolt connectivity interface during the ongoing NDSS 2019 Security Conference. The researchers have been working with development teams from all major OSes in order to remedy the problem, but as the vulnerabilities remain present after all this time, they have decided that it’s time for the world to know. Dubbed as “Thunderclap”, the security flaws allow an attacker to steal sensitive data from the system’s memory, something that resembles a DMA attack.
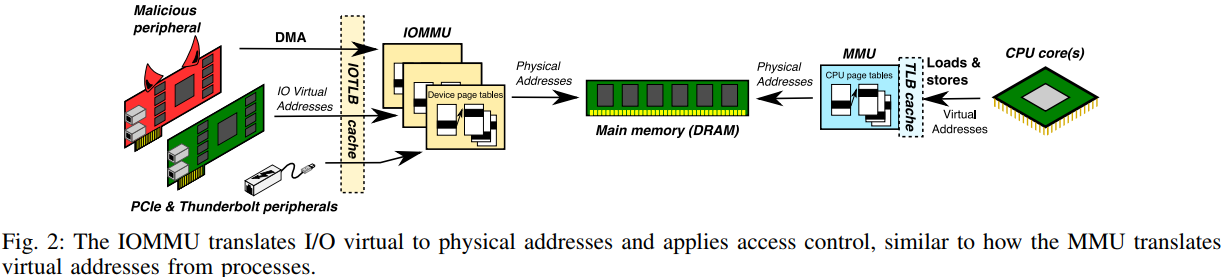
Direct Memory Access (DMA) is a state where the operating system allows a newly connected peripherally to access its memory without the needs for further authentication or permission granted. This automatic-trusting of anything that connects via Thunderbolt comes with great risks, as a specially crafted peripheral can be set to work as usual, while in the same time running malicious code in the background, bypassing the in-built IOMMU (Input-Output Memory Management Unit) security layer. The severity of this problem is high, as the memory banks can contain sensitive data such as user passwords, and thus having a peripheral send this data to a remote server could be a standard exploitation scenario.
source: thunderclap.io
The Thunderbolt interface was introduced as an Apple-exclusive technology that combines PCI Express, DisplayPort, and DC power into a single cable. This versatility made it popular, and so Windows and Linux added support for it so that laptops that are not running Mac OS can still benefit from its broad utilization potential. According to the team of researchers who made the revelations, all OSes and all interface versions, from the first to the third, are vulnerable to Thunderclap. Apple laptops and desktops that left the production lines from 2011 and then on are all susceptible, with the only exception being the 12-inch screen MacBook.
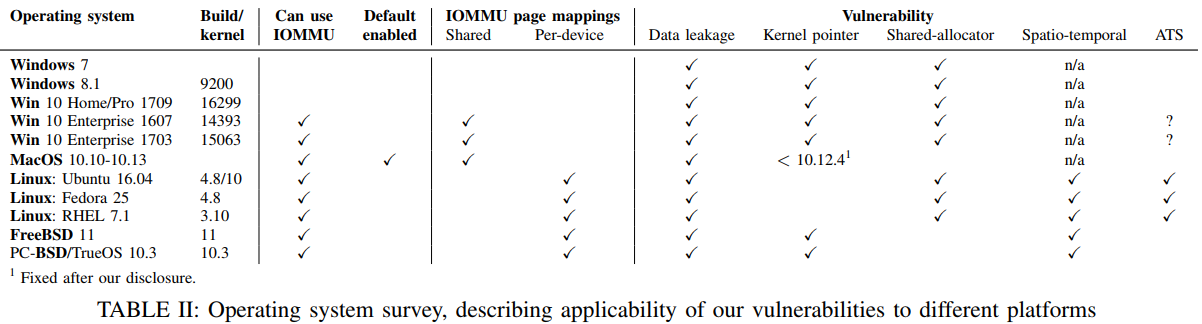
Not all systems are vulnerable on the same level though. Microsoft has enabled the IOMMU security layer for Thunderbolt devices in Windows 10 version 1803, but some vulnerabilities still remain. MacOS 10.12.4 and later features better handling of memory access requests, but Thunderbolt devices still have unrestricted access to all network traffic, and even keystrokes. On Linux, distributions that run kernel version 5.0 and above (currently in preview state) are using IOMMU for Thunderbolt and are considered more robust.
source: thunderclap.io
Users are advised to disable their Thunderbolt ports via the BIOS/UEFI firmware settings until the problems are fixed and to refrain from connecting untrustworthy Thunderbolt devices on their systems. As the research team released the associated proof of concept code on GitHub, hackers are bound to target systems with it soon.
Are you using a Thunderbolt interface? Have you ever had a security problem with it? Let us know in the comments below, and feel free to also share your experience with our online community on Facebook and Twitter.