Discovery of Fog Ransomware Affiliate’s Open Directory Highlights Expanded Threat Landscape
- Security researchers discovered an open directory connected to a Fog ransomware group affiliate.
- It contained reconnaissance, exploitation, lateral movement, and persistence tools and scripts.
- The group’s victims span industries like IT, education, retail, and logistics across Europe, the Americas, and Brazil.
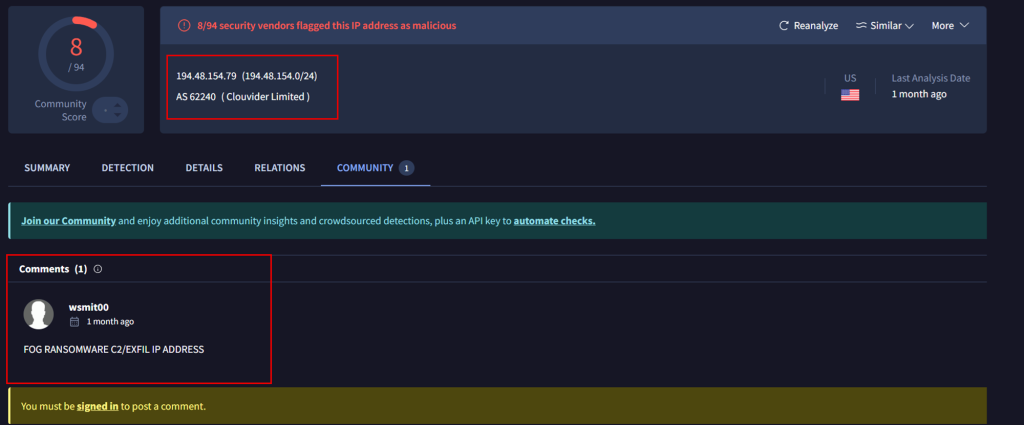
A recent investigation uncovered an open directory in December 2024, tied to an affiliate of the Fog ransomware group. The DFIR Report cybersecurity research team presents a significant breakthrough in understanding the Fog ransomware group’s operations.
It offers a detailed glimpse into the suite of tools and tactics deployed during their campaigns. This discovery sheds light on the persistent and evolving strategies of modern ransomware actors.
The exposed directory revealed meticulously curated tools for reconnaissance, credential theft, lateral movement, persistence, and command-and-control (C2) operations.
Among the tools discovered were:
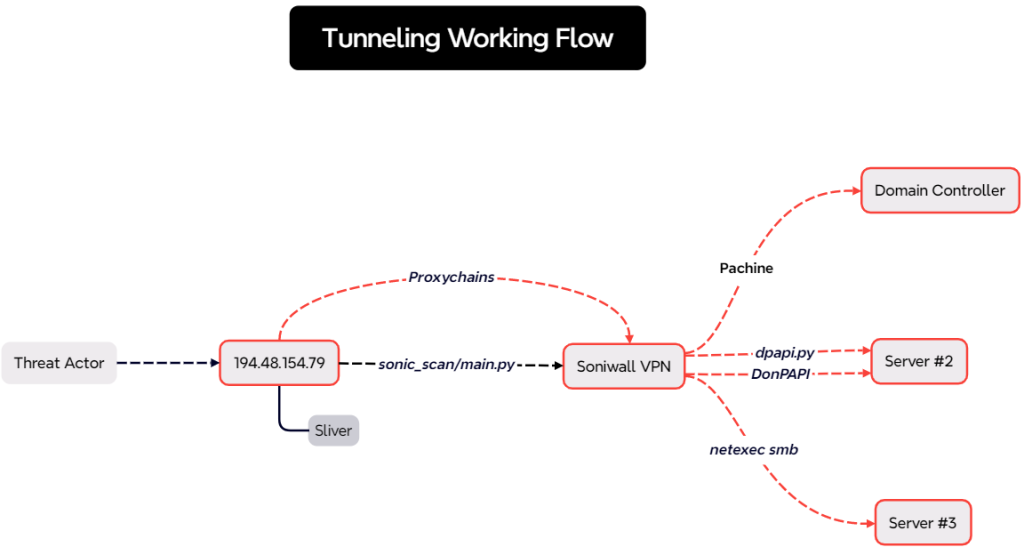
- SonicWall Scanner for exploiting VPN credentials.
- DonPAPI, a tool for extracting Windows DPAPI-protected credentials.
- Certipy, used to compromise Active Directory Certificate Services (AD CS).
- Zer0dump and noPac, exploited for Active Directory vulnerabilities, including CVE-2020-1472 (Zerologon) and CVE-2021-42278.
Notable C2 tools such as Sliver components and Proxychains were also hosted.
The threat actors employed sophisticated persistence mechanisms. For example, AnyDesk was used for remote monitoring and management, automated via a PowerShell script that pre-configured credentials for seamless remote access.
Other tools, such as Powercat, expanded the scope of lateral movement and command execution.
The utilization of a diverse toolkit demonstrates the Fog ransomware group affiliate's adaptability to various environments and targets, enhancing their ability to sustain prolonged campaigns.
Victim analysis indicated an extensive and indiscriminate targeting approach. The ransomware group’s victims spanned industries like technology, education, retail, and logistics across Europe, the Americas, and Brazil.
Evidence from the directory linked activity to several high-profile incidents, including compromise attempts targeting well-known organizations. The geographic scope and diversity of industries continue to place a broad spectrum of organizations at risk.