Lazarus Group ‘Operation SyncHole’ Targeted at Least Six South Korean Entities
- A sophisticated malware campaign has been targeting South Korean organizations for months.
- Based on malware and operational patterns, security researchers attributed this campaign to the Lazarus group with high confidence.
- The APT leverages a combination of watering hole attacks and software flaw exploitation to compromise systems.
The notorious Lazarus group, an advanced persistent threat (APT) actor, has been uncovered at the center of a sophisticated attack campaign targeting across South Korea’s software, IT, financial, semiconductor manufacturing, and telecommunications industries.
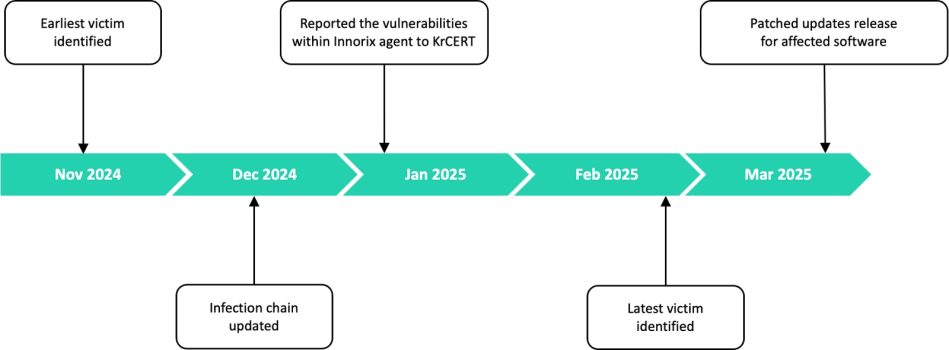
Dubbed "Operation SyncHole," this operation leverages a combination of watering hole attacks and software vulnerability exploitation to infiltrate systems. Security researchers from Kaspersky initiated the investigation after detecting unusual activity in November 2024.
The campaign compromises popular South Korean software solutions, exploiting flaws to target entities that frequently utilize these tools for banking, government, and corporate operations.
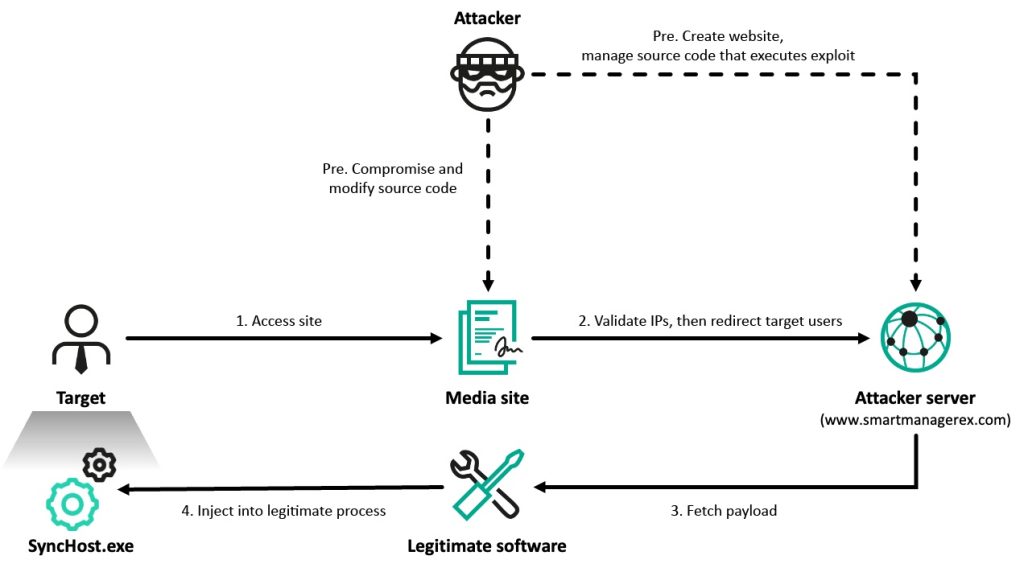
The campaign begins through watering hole attacks, with the North Korean Lazarus group compromising South Korean online media websites to host malicious scripts. By redirecting visitors to attacker-controlled domains, the group exploits vulnerabilities in widely installed software, such as Cross EX, to gain an initial foothold.
This method injects malware into legitimate processes running as a subprocess of targeted software, thereby enabling access to the systems of at least six identified victims as of this report.
The use of legitimate hosting domains and software underscores the group’s sophisticated approach to evading detection while scaling their attack.
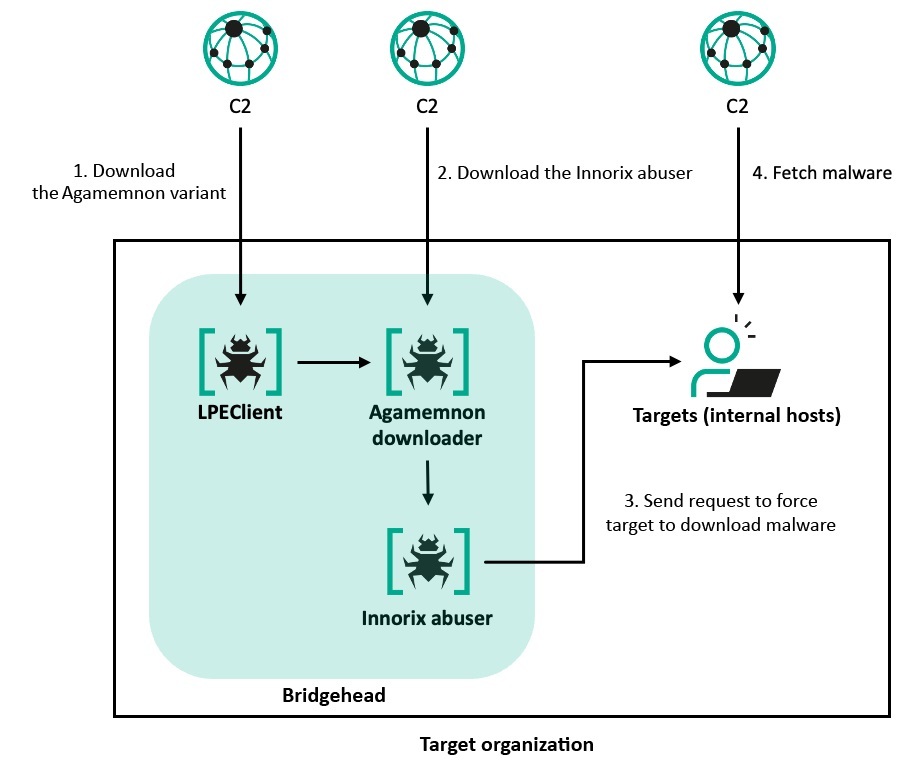
Kaspersky identified several Lazarus-developed malware strains employed during Operation SyncHole, one of them being ThreatNeedle Variant. This flagship backdoor now includes updated persistence and encryption capabilities, allowing attackers sustained access with minimal detection.
They also use the wAgent downloader, a heavily updated version focusing on the delivery of additional payloads, including COPPERHEDGE and the Agamemnon downloader, to execute specific malicious tasks.
SIGNBT and COPPERHEDGE are used during the campaign’s later phases to refine control over compromised systems and conduct reconnaissance.
These malware samples collectively served as modular tools for lateral movement, payload execution, and data exfiltration.
The Lazarus group also exploited a one-day vulnerability in the Innorix Agent to enable lateral movement within affected environments. This affected users with outdated versions of the software.